In the last article I provided you with a few tips on how to create strong passwords, in order to make the hackers job harder at accessing your personal data, in other words, “How do scammers get your information?”.
But where do scammers get your information?
The graphic below depicts the world where most of us find ourselves, and where scammers might obtain important snippets of our personal data that, in many cases, is there for the taking:
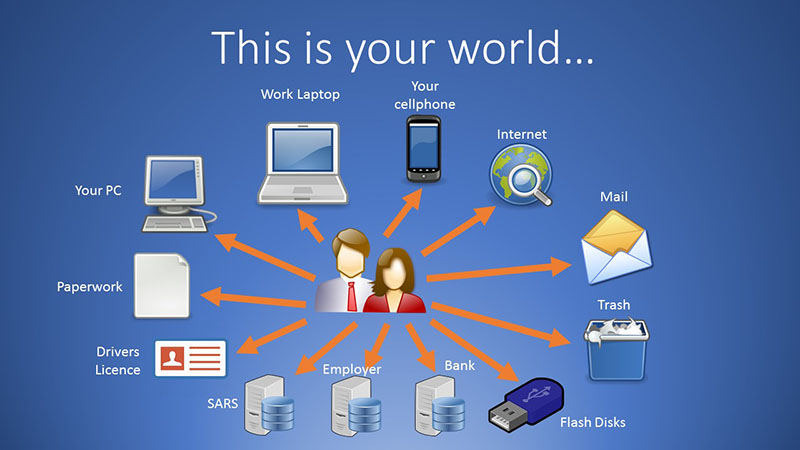
Your personal information is in places beyond your control!
The cellphone has become a indispensable communications tool in the 21st century. According to the Pew Research Centre, South Africa is placed 24th on the world list with a smartphone usage of 37% of the total population. However according to a recent global survey by McAfee and One Poll, 36% of those smartphone users have no form or password, pin or fingerprint protection on their devices. This means that if their phone falls into the wrong hands, they risk opening up all sorts of personal information such as bank details and online logins to whoever finds or steals the smartphone.
How much of your personal information have you placed out there on the internet?
- Over 30% of South African Internet users share at least 3 pieces of personal information posted on their social media profiles that can make stealing their identity easy.
- 60% of South African Internet users have revealed they had no idea what their privacy settings are and who could see their personal information on those sites.
Old-style junk mail, invoices, receipts and ordinary letters can still provide scammers with a wealth of information. Dumpster-diving can reveal documents with your ID Number, old bank statements with your account details, old credit cards, unwanted junk e-mail, payslips and tax forms. Even old prescriptions & medical aid claims can provide scammer with a wealth of information from your personal information.
The modern equivalent of a filing cabinet, a flash disk poses a huge risk to the security of your personal data. Flash disks are small and cheap and can often be forgotten plugged into computers, fall out of pockets and be stolen, providing scammers with all the data stored on that device.
Your bank, your employers and SARS all store and work with your personal information. You have placed a tremendous amount of trust in these organizations to keep your personal data safe. How many people at your bank, for instance, have access to your personal data, who can they potentially give that data to?
Your drivers license has a lot of information on it, including fingerprints, date of birth and ID number. The new style “smart” licenses will hold even more information, and if the license gets int the wrong hands it can be used for identity theft. For instance, in order to open up a cellphone contract, you would need an ID document or driver’s license, bank account details and proof of address, almost all of which can be obtained by dumpster-diving or someone rifling through your paperwork.
Finally your computer (at work or at home) or your laptop holds a huge amount of your personal information. If stolen, the hard-drives can easily be trawled for personal information. If there is no password or a weak password on the laptop it makes stealing this information so much easier!
…This is your world!
- Since 2007, more money has been made from trafficking financial data acquired by identity theft, than money made from drug trafficking.
- 8.8 million South Africans were victims of identity theft in 2015.
- 1 in 3 South Africans do not have a password on their cellphones or computer.
- 70% of South Africans change their passwords after being compromised. (So 30% of South Africans don’t do anything even after they have been compromised)
- 1 in 3 South Africans admit sharing passwords with other people
There are 4 areas where we all neglect the security of our personal information:
- Indifference – Lack of Feeling
- Ignorance – Lack of Knowledge
- Inability – Lack of Training or Education
- Inaction – Lack of Respect
During a recent information session I was asked to suggest to people what they could to to improve their personal data security and to prevent identity theft:
When someone comes and knocks on your front door, do you just open the door and let them in? No, you check who it is and then you decide if you want to open your door to them or not. The power of access is in your hands because you control the door!
The same principle applies to your personal data. Be careful and vigilant and be the gatekeeper of your personal data! Control what data is given out and who receives it. You have the control!
Next time we will look at the modus operandi of identity thieves.
Keep safe out there,
David Wiles









