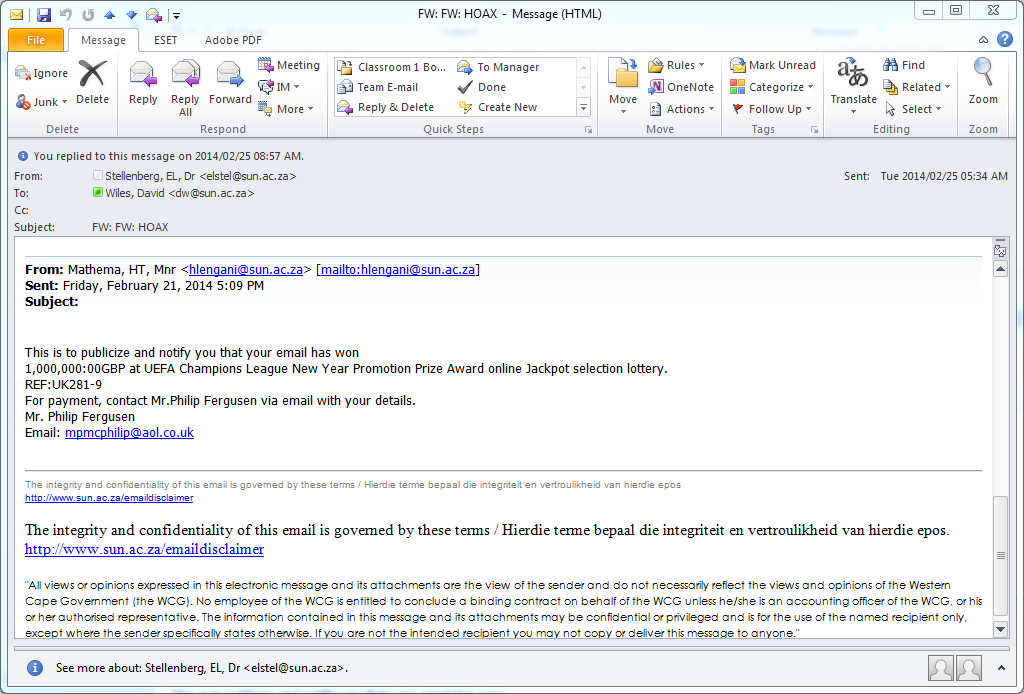
Below is an example of an phishing scam that has been sent out seemingly by a legitimate University-based e-mail account. Unfortunately this time, the e-mail message has been sent to other institution’s addresses and the university is being wrongly criticised for “allowing” this.
Remember: The only purpose of a phishing scam is to get victims to provide their personal information and thereby gain access and control of passwords, bank account numbers and personal details.
Information Technology will be investigating this incident but keep this in mind:
- Many times an automatic program is used to “spoof” or forge a phony e-mail address to disguise the real sender The address is often pulled from a database of “stolen addresses”.
- This university e-mail account owner might be a victim themselves of a phishing scam, and have provided their details to scammers, resulting in their address or computer being “hijacked” by the phishers.
- In some cases an e-mail address owner is employed by the phishers to operate and send out phishing mails on their behalf with the promise of earning money for their services. (Earn $10 000 per month and work from home) in this case it is unlikely, but nevertheless a risk.
In the screen grab below note the “honeypot”:
…There is no Subject line
…It seems to come from a university employee but the reply to address is some other address
…It promises that you have won a large amount of money. That always attracts people.
[ARTICLE BY DAVID WILES]
Onder is `n voorbeeld van `n nuwe strikroofpoging wat skynbaar uitgestuur is deur `n geldige Universiteit e-posadres. Ongelukkig is die e-pos boodskap ook gestuur na ander instellings se adresse en die universiteit word verkeerdelik gekritiseer omdat dit “toegelaat” is.
Onthou: Die enigste doel van hierdie lokvalle is om slagoffers so ver te kry om hul persoonlike inligting weer te gee en sodoende toegang en beheer oor wagwoorde, bankrekeninginligting en ander details te kry.
Informasietegnologie ondersoek reeds dié spesifieke insident, maar hou die volgende in gedagte:
1. Dikwels sal `n outomatiese program gebruik word om `n onegte adres te genereer om die regte versender van die e-pos weg te steek. Die adres word gewoonlik onttrek vanuit `n databasis van “gesteelde adresse.”
2. Die universiteits e-posrekeninghouer is waarskynlik self die slagoffer van strikroof en het hul details aan kuberkriminele verskaf – wat om die beurt gelei het daartoe dat hulle adres of rekenaar ge”kaap” is deur die krininele.
3. In sommige gevalle word `n e-posadres eienaar in diens geneem deur kuberkriminele om hierdie e-posse uit te stuur met die belofte dat hulle geld sal verdien vir hul dienste. (Earn $10 000 per month and work from home). In hierdie geval is dit natuurlik onwaarskynlik, maar dit bly steeds `n groot risiko om te reageer op sulke aanbiedinge.
Op die skermskoot onder, let op die weggeetekens:
… Daar is geen “subject line”
… Dit wil voorkom of dit van `n universiteitswerknemer gestuur is, maar die “reply to” adres is `n ander adres.
… Jy word belowe dat jy `n groot hoeveelheid geld gewen het. Natuurlik is dit `n groot trekpleister van die meeste mense!
[ARTIKEL DEUR DAVID WILES]