The only thing that must be more annoying than us constantly warning you of e-mail scams, is the persistence that is shown by the criminals and scam artists to attempt to con you, and steal your personal data and money.
The problem is they will continue to send phishing mails because they continue to catch people, even within an academic institution like the University.
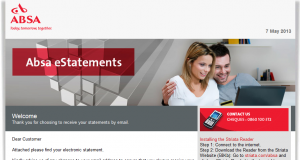 Recently another ABSA eStatement landed in our e-mail box, this time a little more sophisticated, but armed with a few basic tips you will be able to spot the scam quickly.
Recently another ABSA eStatement landed in our e-mail box, this time a little more sophisticated, but armed with a few basic tips you will be able to spot the scam quickly.
Keep an eye out for these mails in your mailbox and delete then or add then to your Junk-Mail filters to block them in future.
Here’s how you spot can them:
1. Did you give your @sun.ac.za work address as your primary contact for Internet Banking?
2. Do you bank with (in this case) ABSA?
3. Is the salutation addressed to you personally, or is it just “Dear Customer”?
4. Is there a .pdf or an .html file attached? (phishers almost always use .html – a forged web-page)
5. Is the Subject of the e-mail “important” sounding? (In this case “Absa Cheque Account Statement”)
6. If you click on (or open by mistake) the attachment, does the web page look like the bank’s normal login page but does it LACK the https:// text at the front of the address and is the normal http://?
Answering these questions, it will be easy to establish whether an e-mail is clearly a phishing scam and can be deleted. Be vigilant and alert. Anyone can be caught out – even you.
[ARTICLE BY DAVID WILES]
Die enigste ding meer irriterend as ons wat jou voortdurend waarsku teen e-pos skelmstreke, is die deursettingsvemoë van kriminele en kuberswendelaars om jou te probeer uitvang en jou data en geld te steel.
Ongelukkig sal die probleem nie verdwyn solank as wat hierdie metodes telkens suksesvol is nie – selfs binne `n akademiese instelling soos die Universiteit.
 Onlangs het nog `n ABSA eStaat in ons posbusse beland, hierdie keer `n bietjie meer gesofistikeerd, maar gewapen met `n paar wenke, kan jy dit baie maklik herken.
Onlangs het nog `n ABSA eStaat in ons posbusse beland, hierdie keer `n bietjie meer gesofistikeerd, maar gewapen met `n paar wenke, kan jy dit baie maklik herken.
Kyk uit vir hierdie e-posse, vee hulle uit of skuif dit na jou Junk-Mail filters sodat dit volgende keer geblok word.
Hier is hoe jy dit kan uitken:
1. Het jy jou @sun.ac.za werkadres as primêre kontakadres vir jou internetbankdiens gegee?
2. Doen jy jou banksake by ABSA?
3. Is die aanhef aan jou persoonlik gerig of is dit net `n vae “Dear Customer”?
4. Is daar `n .pdf of ‘n .html leêr aangeheg? (kuberkrakers gebruik graag .html omdat dit jou herlei na `n vervalsde webblad)
5. Klink die onderwerp van die e-pos “belangrik” of amptelik? (In die geval “Absa Cheque Account Statement”)
6. As jy kliek op die aanhangsel of dit per ongeluk oopmaak, lyk die webblad soos die bank se normale aantekenblad, maar sonder die https:// teks vooraan die adres? (https:// dui op `n veilige bediener, terwyl http:// `n oop webblad is)
Na aanleiding van bogenoeme vrae kan jy duidelik vasstel of `n e-pos `n phishing-poging is en bloot uitgevee kan word. Wees waaksaam en op jou hoede. Enigiemand kan uitgevang word.
[ARTIKEL DEUR DAVID WILES]


 Once of the most common questions we get asked by users is – How do these spammers get my e-mail address? Previously we looked at Rumpelstiltskin attacks, bots, trojans and zombies. This time around we focus at a third method – by using Subscribe/Unsubscribe newsletter services.
Once of the most common questions we get asked by users is – How do these spammers get my e-mail address? Previously we looked at Rumpelstiltskin attacks, bots, trojans and zombies. This time around we focus at a third method – by using Subscribe/Unsubscribe newsletter services. We’ve been having plenty of stormy weather over the past few days, so in keeping with the theme, did you know you even get e-mail storms?
We’ve been having plenty of stormy weather over the past few days, so in keeping with the theme, did you know you even get e-mail storms?