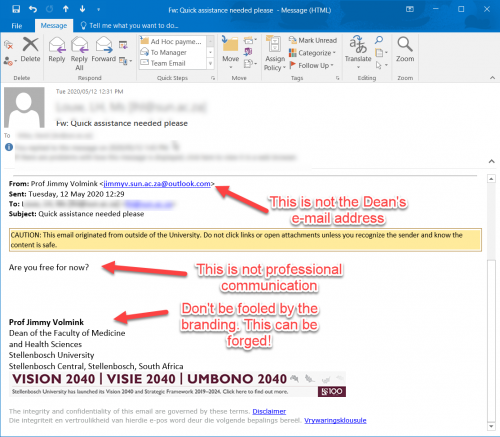
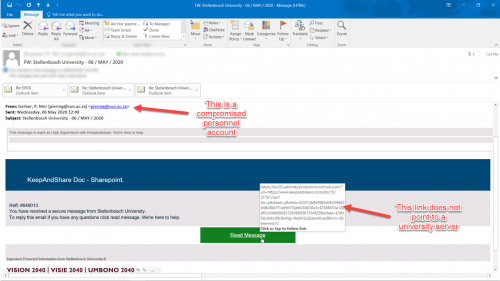
[:en]
 Stellenbosch University devices are equipped with the necessary software for our staff to perform their work effectively. This includes the latest operating system; all the Microsoft applications (Office 365, including Word, Excel, PowerPoint, etc.), Adobe Acrobat Professional, TeraTerm and the necessary Antivirus software. Licenses for specialist software can also be purchased through the IT department, will fall under the University’s educational license and therefore be less expensive than a license bought in a personal capacity. These include Adobe Creative Cloud; MatLab and Statistica, among others.
Stellenbosch University devices are equipped with the necessary software for our staff to perform their work effectively. This includes the latest operating system; all the Microsoft applications (Office 365, including Word, Excel, PowerPoint, etc.), Adobe Acrobat Professional, TeraTerm and the necessary Antivirus software. Licenses for specialist software can also be purchased through the IT department, will fall under the University’s educational license and therefore be less expensive than a license bought in a personal capacity. These include Adobe Creative Cloud; MatLab and Statistica, among others.
Installing and using this software is essential for staff, however some of our staff use their SU devices for their own personal use and subsequently download and install non-supported as well as illegal software on their PCs. This includes games and illegal series or movies.
Not only does this put the University’s network at a high risk security-wise, it also puts the University at risk legally. Even if Information Technology does not install the software, we are still being held responsible for it if it’s an SU asset and it runs on our network.
The fight against illegal software and piracy is mainly fought by the BSA. The Business Software Alliance (BSA) confronts companies that use or distribute illegal
software. Read BSA’s statement on illegal software.
Therefore we kindly request that you ensure that if you install software, it’s safe and legal to use. Otherwise it might have implications for you and the University.
[:af]
 Universiteit Stellenbosch rekenaars en ander toestelle word toegerus met die nodige sagteware om te verseker dat personeel hulle werk effektief kan verrig. Dit sluit die nuutste bedryfstelsel, alle Microsoft-applikasies (Office 365, insluitende Word, Excel, PowerPoint, etc.), sowel as Adobe Acrobat Professional, TeraTerm en die nodige anti-virus sagteware.
Universiteit Stellenbosch rekenaars en ander toestelle word toegerus met die nodige sagteware om te verseker dat personeel hulle werk effektief kan verrig. Dit sluit die nuutste bedryfstelsel, alle Microsoft-applikasies (Office 365, insluitende Word, Excel, PowerPoint, etc.), sowel as Adobe Acrobat Professional, TeraTerm en die nodige anti-virus sagteware.
Lisensies vir spesialis-programmatuur kan ook deur die IT-afdeling aangekoop word. Aangesien dit onder die Universiteit se spesiale lisensie vir opvoedkundige instansies val, sal dit ook goedkoper wees as om dit self aan te koop. Dit sluit, onder andere, Adobe Creative Cloud; MatLab en Statistica in.
Die installasie en gebruik van hierdie programmatuur is essensieel vir personeel. Sommige personeel gebruik daarbenewens egter ook US-toerusting vir persoonlike doeleindes en installeer programmatuur wat IT nie ondersteun nie of selfs onwettig is. Dit sluit dikwels speletjies en onwettige reekse of flieks in.
Hierdie tipe programmatuur en materiaal is ʼn hoë sekuriteitsrisiko vir die Universiteit se netwerk, sowel as vanaf ʼn wetlike perspektief. Selfs al installeer Informasietegnologie nie die programmatuur nie, word ons steeds verantwoordelik gehou wanneer dit ʼn US-bate is en op ons netwerk aanteken.
Die bekamping van onwettige programmatuur en rowery word deur die BSA aangevoer. Die Business Software Alliance (BSA) konfronteer maatskappye wat onwettige programmatuur gebruik of versprei. Lees die BSA se standpunt oor onwettige programmatuur.
Ons versoek dus dat, voordat jy enige programmatuur self installeer, jy sekermaak dat dit beide veilig en wettig is om te gebruik. Andersins mag dit verreikende implikasies hê vir beide jou en die Universiteit.
[:]