[:en]
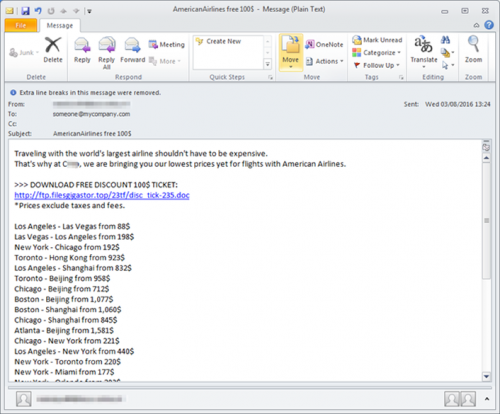
Our week starts off with the latest spam e-mail, one from FNB requesting that you activate your card. Of course this isn’t legitimate, even if it looks fairly convincing. Note the :-) in the subject line. This alone should be a dead giveaway. No bank will (we hope) communicate with emoticons.
The link in the e-mail will lead you to a temporary file in your browser where you have to fill in your details. Please ignore and delete this e-mail if you receive it. If you are a FNB customer and at any time, receive any e-mails you are not sure about, rather phone your bank directly and confirm.
If you receive any similar phishing e-mails, please forward then to sysadm@sun.ac.za as an attachment. This way we can add it to our spam filter and ensure no-one else receives them.
See the example of the FNB e-mail below. (Malicious links were deactivated)
…………………………………………………………………………………………………………………………
Date: Thu, 15 Jun 2017 23:41:08 +0000
From: inContact <fakeaddress@fnb.co.za>
To: Recipients <fakeaddress@fnb.co.za>
Subject: FNB :-) Account Card Activation Request 16Jun 00:00
x-spam-score: -89.7 (—————————————————)
[– Attachment #1 –]
[– Type: text/plain, Encoding: base64, Size: 0.7K –]
Dear Valued Card Holder,
As Directed by South African Credit Card Authorities, All card holders as advised to register their FNB cards on the new security platform to avoid your account from being compromised and also
+deactivated.
To reactivate your Credit / debit Card Kindly click on the below ATTACHED and follow instructions.
SEE ATTACHED TO REACTIVATE / REGISTER YOUR FNB CARD
*NOTE: Failure to do this will lead to suspension of your ATM Card.*
Copyright c 2017 Inter-Switch Limited
Thank you.
Administrator
………………………………………………………………………………………………………………………..
[:]