Microsoft Authenticator app’s number matching feature has been generally available since November 2022. If you have not already leveraged the rollout controls (via Azure Portal Admin UX and MSGraph APIs) to smoothly deploy number matching for users of Microsoft Authenticator push notifications, we highly encourage you to do so.
Microsoft extended the availability of the rollout controls until 8 May 2023, to deploy number matching in their organisations. Microsoft services started enforcing the number matching experience for all users of Microsoft Authenticator push notifications since then.
Please note
The expected behaviour for NPS extension have been changed to be more admin friendly. NPS versions 1.2.2216.1+ will be released once Microsoft starts to enable number matching for all Authenticator users. These NPS versions will automatically prefer OTP based sign-ins over traditional push notifications with the Authenticator app. An admin can choose to disable this behavior and fallback to traditional push notifications with Approve/Deny by setting the registry key OVERRIDE_NUMBER_MATCHING_WITH_OTP Value = FALSE. Previous NPS extension versions will not automatically switch Authenticator push notification authentications to OTP based authentications.
How does this affect the university?
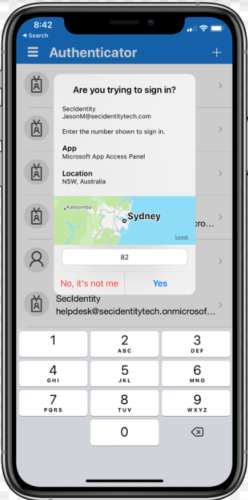
To prevent accidental approvals, admins can require users to enter a number displayed on the sign-in screen when approving an MFA request in the Microsoft Authenticator app. This feature is critical to protecting against MFA fatigue attacks which are on the rise.
Another way to reduce accidental approvals is to show users additional context in Authenticator notifications. Admins can now selectively choose to enable the following:
- Application context: Show users which application they are signing into.
- Geographic location context: Show users their sign-in location based on the IP address of the device they are signing into.
Number match behaviour in different scenarios going forward
- Authentication flows will require users to do number match when using the Microsoft Authenticator app. If the user is using a version of the Authenticator app that doesn’t support number match, their authentication will fail. Please make sure upgrade to the latest version of Microsoft Authenticator (App Store and Google Play Store) to use it for sign-in.
- Self Service Password Reset (SSPR) and combined registration flows will also require number match when users are using the Microsoft Authenticator app.
- ADFS adapter will require number matching on versions of Windows Server that support number matching. On earlier versions, users will continue to see the “Approve/Deny” experience and won’t see number matching till you upgrade.
o Windows Server 2022 October 26, 2021—KB5006745 (OS Build 20348.320)
o Windows Server 2019 October 19, 2021—KB5006744 (OS Build 17763.2268)
o Windows Server 2016 October 12, 2021—KB5006669 (OS Build 14393.4704)
- NPS extension versions beginning 1.2.2131.2 will require users to do number matching after May 2023. Because the NPS extension can’t show a number, the user will be asked to enter a One-Time Passcode (OTP). The user must have an OTP authentication method (e.g. Microsoft Authenticator app, software tokens etc.) registered to see this behaviour. If the user doesn’t have an OTP method registered, they’ll continue to get the Approve/Deny experience. You can create a registry key that overrides this behaviour and prompts users with Approve/Deny.
- Apple Watch will remain unsupported for number matching. We recommend you uninstall the Microsoft Authenticator Apple Watch app because you have to approve notifications on your phone.

