A serious virulent ransomware threat known as WannaCrypt0r/WannaCry has been affecting Windows computers on shared networks in around 150 countries worldwide. Once one computer on a network is affected, the malware infection easily spreads to other Windows computers on the same network, shutting down entire government agencies and national infrastructure companies. More on this attack.
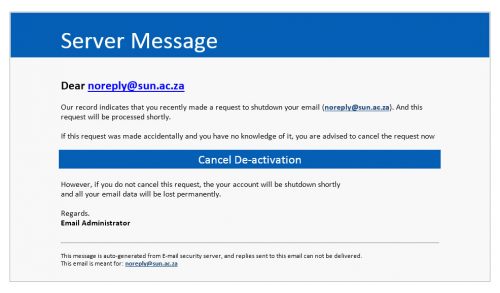
Ransomware forms part of a group of malicious computer software called malware, which installs itself on your PC. It can be installed by means of an e-mail attachment, an infected programme or unsafe website with malware installed on it. The software “kidnaps” your data by encrypting or limiting your access to it and then sending you a message demanding money to regain your access. The only way access is possible again, is by acquiring an encryption key from the creator of the ransomware at a fee and this isn’t necessarily guaranteed.
But how do you protect yourself from ransomware?
- If you use Windows, install the patch that Microsoft has released to block the specific exploit that the WannaCry ransomware is using. Instructions can be found in the Microsoft Knowledge Base. You can also directly download the patches for your OS from the Microsoft Update Catalogue. (Take note that this is mostly applicable to devices that are not on the university network.)
- Update your Antivirus software definitions. Most AV vendors have now added detection capability to block WannaCry. (Devices running on the SU network should be up to date)
- If you don’t have anti-virus software enabled on your Windows machine, enable Windows Defender, or Avast! AV or Avira AntiVirus, which is free.
- Backup regularly and make sure you have offline backups. That way, if you are infected with ransomware, it can’t encrypt your backups.
- For further reading, this is an excellent detailed write-up on the WannaCry ransomware.
- Get the word out.
[INFORMATION SUPPLIED BY DAVID WILES]