Over 2 billion people worldwide have purchased goods or services online during the pandemic. The danger of all this convenient shopping with Takealot, Checkers or any online store is that people provide their credit card number without diligence.
One of the most prevalent scams NOW is called POP or Proof of Payment Receipt. There are a number of new phishing scams with the subject “Proof of Payment” or “Suspicious Bank transaction” at the moment.Â
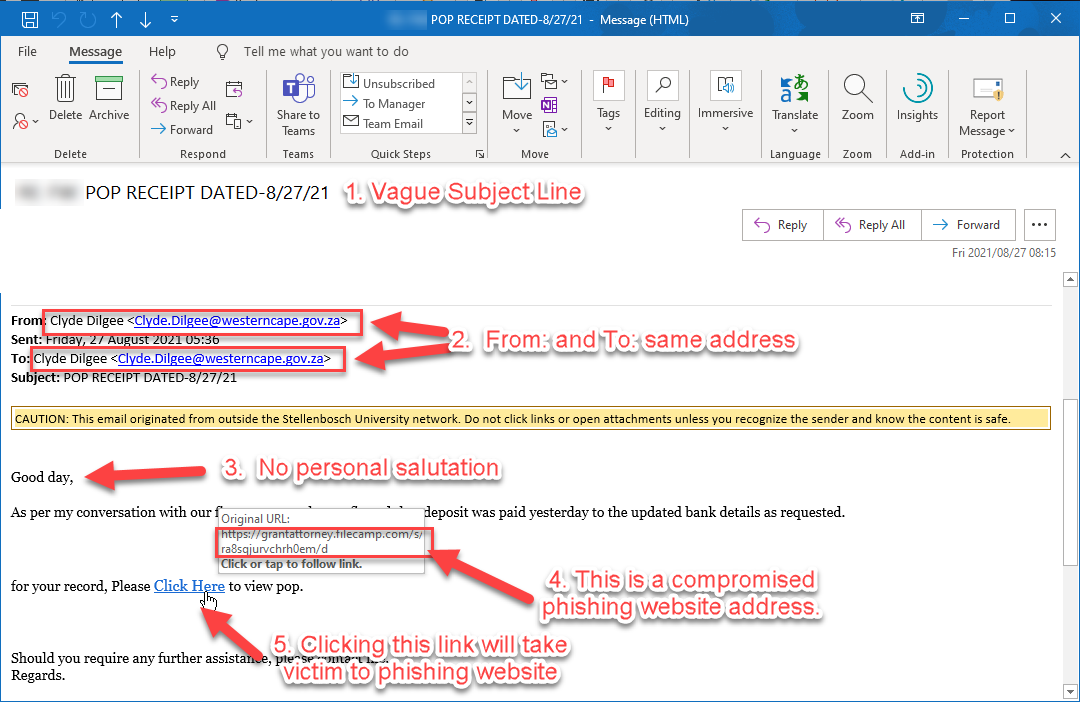
Here is one such scam that is currently being reported by personnel and students at Tygerberg.Â
The way that this scam works is that the scammers are trying to get their victims to click on the link and go to a specially engineered site to steal passwords and login credentials. Often bank account details and cell phone numbers are asked for, and this is how the scammers get access to bank accounts and can do SIM swaps, to steal money and personal details.
Notice how the mail details have been forged to make the sender and the recipient the same. This is to disguise the true sender and to bypass the mail filters which would normally accept mail from within an organisation. In this case this sender used a “throw-away” Outlook.com e-mail address and then forged the headers to change the sender. In this case there is a possibility that the government address has been compromised.
If you get one of these e-mails or one similar looking (scammers change tactics very quickly) please report it to IT on the ICT Partner Portal. Fill in your information and add the email as an attachment. Your request will automatically be logged on the system.​​
Secondly blacklist the sender under Junk mail, and perhaps even block the entire domain. You can do this by using the Report Message add-in on Outlook (available on your toolbar on the far right) More about the add-in on our blog or you can find the instructions on this .PDF
[ARTICLE BY DAVID WILES]


 Last month some university staff’s mailboxes were flooded with
Last month some university staff’s mailboxes were flooded with