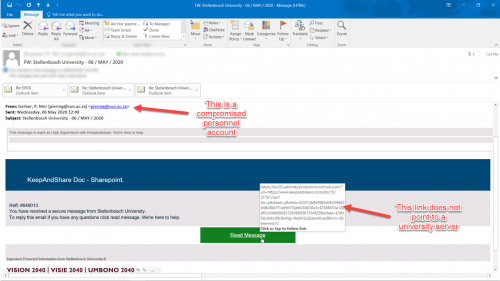
We are almost all in lock down and less careful with cyber security.¬†The scammers know this and are launching numerous attacks taking advantage of the “work-from-home” situation we find ourselves in. A number of personnel have reported getting e-mails from “Prof. Jimmy Volmink” asking for assistance and are not spotting the tell-tale signs of a phishing scam.
Here is the mail:
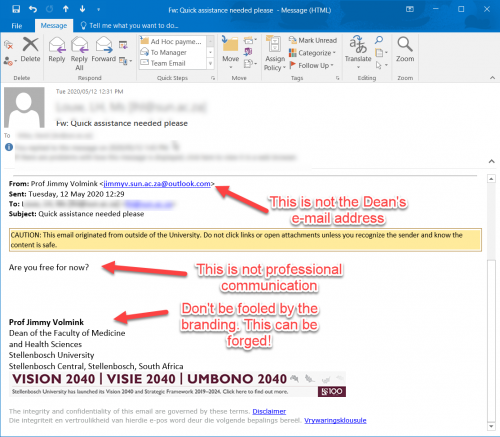
- Notice that although it looks like Prof Volmink sent it, the email address is not correct.
- ¬†Secondly Prof Jimmy is a very approachable person, but he is always professional in his communication so he would never say “Are you free for now”. Nor would he say something like this: (if you did respond to his mail)
“I am currently in a meeting and I don’t know when the meeting will round off. I would have called you but phone is not allowed. I will want you to handle something for me right away and I will be glad if you can do that for me as soon as possible”.
This is a spear-phishing attack where an institution is directly attacked by impersonating prominent or public figures within the university (like the Dean) to gain access to the university network. This is an especially effective means of attack with everybody at home in lock down, where our guard is down and we are more relaxed. There was a very similar attack in September 2019, using the same tactics.  
Prof Volmink’s account has not been compromised. Phishers are just trying to fool us into thinking that prominent members in our leadership are emailing us asking for assistance, but they are not. It is a scam.
Over the next few days be on the lookout for similar mails that look like they coming from other people within the university.
If you do get mail like this be sure to report it to IT ASAP so they can block the attack and help people who have become victims.
Please immediately report such phishing scams and spam by reporting it on the ICT Partner Portal.‚Äč‚Äč
Go to https://servicedesk.sun.ac.za/jira/servicedesk/customer/portal/6/create/115.‚Äč‚Äč
Fill in your information and add the email as an attachment. Your request will automatically be logged on the system.‚Äč‚Äč
If you have accidentally clicked on the link and already given any personal details to the phishers it is vitally important that you immediately go to the USERADM page (either http://www.sun.ac.za/password  or www.sun.ac.za/useradm ) and change your password immediately. Make sure the new password is completely different, and is a strong password that will not be easily guessed, as well as changing the passwords on your social media and private e-mail accounts, especially if you use the same passwords on these accounts.