The only thing that must be more annoying than us constantly warning you of e-mail scams, is the persistence that is shown by the criminals and scam artists to attempt to con you, and steal your personal data and money.
The problem is they will continue to send phishing mails because they continue to catch people, even within an academic institution like the University.
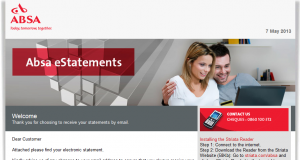 Recently another ABSA eStatement landed in our e-mail box, this time a little more sophisticated, but armed with a few basic tips you will be able to spot the scam quickly.
Recently another ABSA eStatement landed in our e-mail box, this time a little more sophisticated, but armed with a few basic tips you will be able to spot the scam quickly.
Keep an eye out for these mails in your mailbox and delete then or add then to your Junk-Mail filters to block them in future.
Here’s how you spot can them:
1. Did you give your @sun.ac.za work address as your primary contact for Internet Banking?
2. Do you bank with (in this case) ABSA?
3. Is the salutation addressed to you personally, or is it just “Dear Customer”?
4. Is there a .pdf or an .html file attached? (phishers almost always use .html – a forged web-page)
5. Is the Subject of the e-mail “important” sounding? (In this case “Absa Cheque Account Statement”)
6. If you click on (or open by mistake) the attachment, does the web page look like the bank’s normal login page but does it LACK the https:// text at the front of the address and is the normal http://?
Answering these questions, it will be easy to establish whether an e-mail is clearly a phishing scam and can be deleted. Be vigilant and alert. Anyone can be caught out – even you.
[ARTICLE BY DAVID WILES]


 Once of the most common questions we get asked by users is – How do these spammers get my e-mail address? Previously we looked at Rumpelstiltskin attacks, bots, trojans and zombies. This time around we focus at a third method – by using Subscribe/Unsubscribe newsletter services.
Once of the most common questions we get asked by users is – How do these spammers get my e-mail address? Previously we looked at Rumpelstiltskin attacks, bots, trojans and zombies. This time around we focus at a third method – by using Subscribe/Unsubscribe newsletter services. We’ve been having plenty of stormy weather over the past few days, so in keeping with the theme, did you know you even get e-mail storms?
We’ve been having plenty of stormy weather over the past few days, so in keeping with the theme, did you know you even get e-mail storms?