The international law of data protection has changed and the General Data Protection Regulation (GDPR) came into effect on the 25 May 2018. There is a great deal of information on GDPR. Unfortunately, a lot of it is legal jargon, which can be overwhelming if you are not a legal expert.
The South African equivalent to GDPR is the Protection of Personal Information Act (POPIA); which has not been finalised yet. This article will explain GDPR, compliance requirements and the key benefits and challenges involved in its implementation.
Quick overview
GDPR is a law that governs data usage, user privacy rights, data risk management and data security systems within private and public organisations. It highlights the rights of individuals, which are
- to control how personal data is collected and managed; and
- to place new obligations on organisations to be more accountable for data protection.
Complying with GDPR is not a simple task, and neither will be complying with South Africa’s own Protection of Personal Information Act (POPIA). However, it is unavoidable and cannot be ignored. Managing data privacy is a serious issue. Until the South African Regulations are finalised and enforced, local companies are encouraged to look to the GDPR for guidance. Whilst there are some differences between POPIA and GDPR in requirements, the principles are similar.
How does an organisation comply?
Decision makers and key people in the organisation need to be aware that the law has changed to include GDPR, and need to understand its impact on data management.
An information audit, which includes any personal data held by individuals within the organisation, has to be done. The audit will establish which information the organisation has, who it’s shared with and where it came from.
Review your privacy notices and governance, identify gaps and prepare for the changes required when implementing GDPR.
Make sure procedures cover each individual’s rights, including deleting personal data and providing data electronically in all commonly used formats.
Update data management procedures, prepare for handling requests from consumers within the new time-frame and provide additional information.
- Legalities when processing personal data
Understand the different data processing types, the way the organisation performs and identify the legal basis for carrying out and documenting it appropriately.
The way the organisation seeks, obtains and determines consent may need to be reviewed and changed.
- Protecting children’s data
Systems to verify ages and can seek parental/guardian consent for a data processing activities should be designed and developed.
Procedures for both the customer and regulator need to be in place to detect, report and investigate a personal data breach.
- Data protection by design
Assessments and control frameworks have to be developed with guidance from the regulator. Processes need to be developed and have governance for their use.
Data Protection Officers or a similar role should be appointed to take responsibility for data protection compliance. The organisation has to decide who fits this role best.
If the organisation works internationally, it is important to establish which data protection authority is most appropriate and where processors and controllers are located.
Some benefits of GDPR compliance
- Greater consumer confidence
GDPR compliance will prove to customers that your organisation is a good custodian of their data.
GDPR compliance lays the groundwork for improved data security.
- Reduced data maintenance costs
GDPR can help your organisation cut costs by prompting you to retire any data inventory software and legacy applications which are no longer relevant to your business.
- Increased alignment with evolving technology
GDPR compliance requires that your organisation moves toward improving its network, endpoint, and application security.
Thanks to the GDPR, your organisation’s data will become more consolidated, ensuring it’s easier to use and you have a greater understanding of its underlying value.
Challenges of GDPR compliance
- Endless consent prompts for every data process can be time-consuming.
- High cost to reach GDPR compliance (e.g. in terms of upgrading security systems).
- More work for developers in terms of upgrading security systems.
- Massive fines for non-compliance, which amounts to 4% of the organisation’s annual turnover.
GDPR integration in SU IT Department
In many ways, Stellenbosch University’s Information Technology Department has been implementing data and security laws and regulations such as GDPR and POPIA for years.
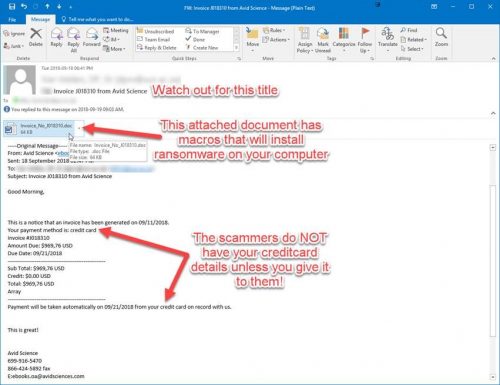
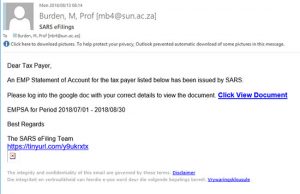
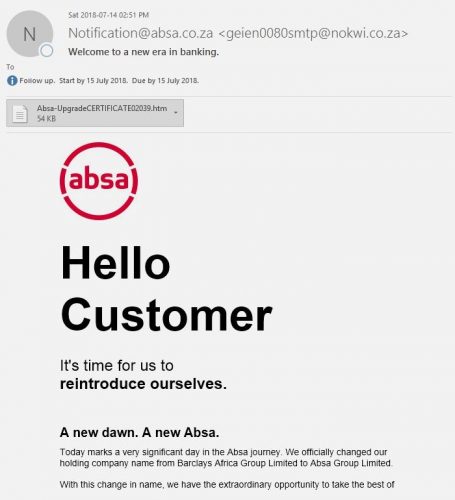
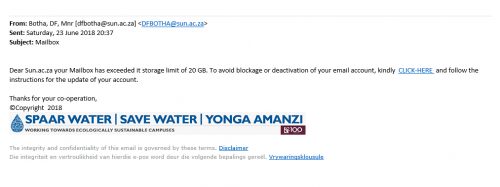
We are constantly reminding users on our blog and social media to keep their passwords protected and not leave their PC’s unlocked and unattended. We are the first to alert users via email with regards to phishing attacks and send out warnings on a regular basis. We have also moved toward cloud storage and are happy to say, Microsoft is GDPR compliant. Users have been encouraged to use OneDrive for data storage as it is more secure.
Information security is important, therefore we will continue to convey the importance to our users. There is also an Information Security Awareness Training Course available on SUNLearn.
In conclusion, GDPR is beneficial to South African organisations in many ways. Since South African organisations deal with large and sensitive amounts of data, GDPR compliance is required and may reduce security threats and data loss to a large degree. Although this law appears to solve and manage data management issues, there is still limited information regarding their long-term sustainability and among South African users.
More detailed information on EU GDPR guidelines for South African Universities can be found in this document compiled by Universities South Africa (USAf), an association of South Africa’s public universities.
[ARTICLE BY MILLY VAN WYHE]