Many of our staff and students use FortiClient to obtain VPN access to the Stellenbosch University network when they are not on campus. To maintain a safe and secure network, we have to put measures in place for our services to minimise the potential exposure to the University from damages which may result from unauthorised use of university resources. This is particularly important when it comes to access via VPN to our network.
From 6 August 2018 new VPN users have to register for VPN usage. If you have used VPN (FortiClient) since 1 January 2018, you are considered a registered user by default and don’t have to reapply for access. However, if you are a new VPN user, please follow the process described below.
If you need VPN access to the SU network via FortiClient, the following simple process is applicable:
- The head of your department needs to send an email to help@sun.ac.za motivating why you require VPN access for work purposes.
- You will receive an email confirming your registration with instructions on how to install the FortiClient needed for VPN usage.
A VPN (Virtual Private Network) is a way of connecting your off-site computer directly to the University network and allows you to access internal resources such as other computers, network storage, websites, journals using the applications already installed on your off-site computer. VPN provides an encrypted connection which helps to ensure that sensitive data is safely transmitted and prevents unauthorized people from eavesdropping on the traffic, allowing the user to conduct work remotely.
A secure VPN connection to the SU network with FortiClient is not necessary for standard, web-based services. These include email, library resources, SUNLearn or the SUN-e-HR website. All of these services are already accessible via the internet without a VPN connection.
More information on the use of VPN and FortiClient at SU is also available on our service catalogue.



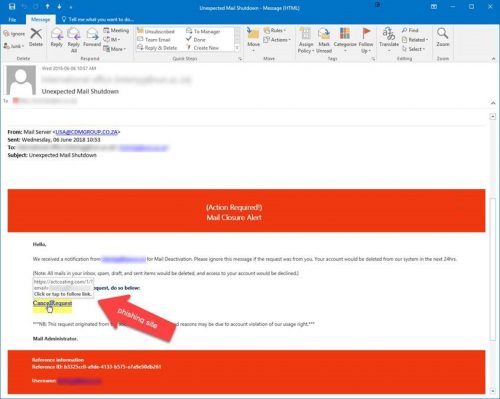
 Hi <your name>,
Hi <your name>,