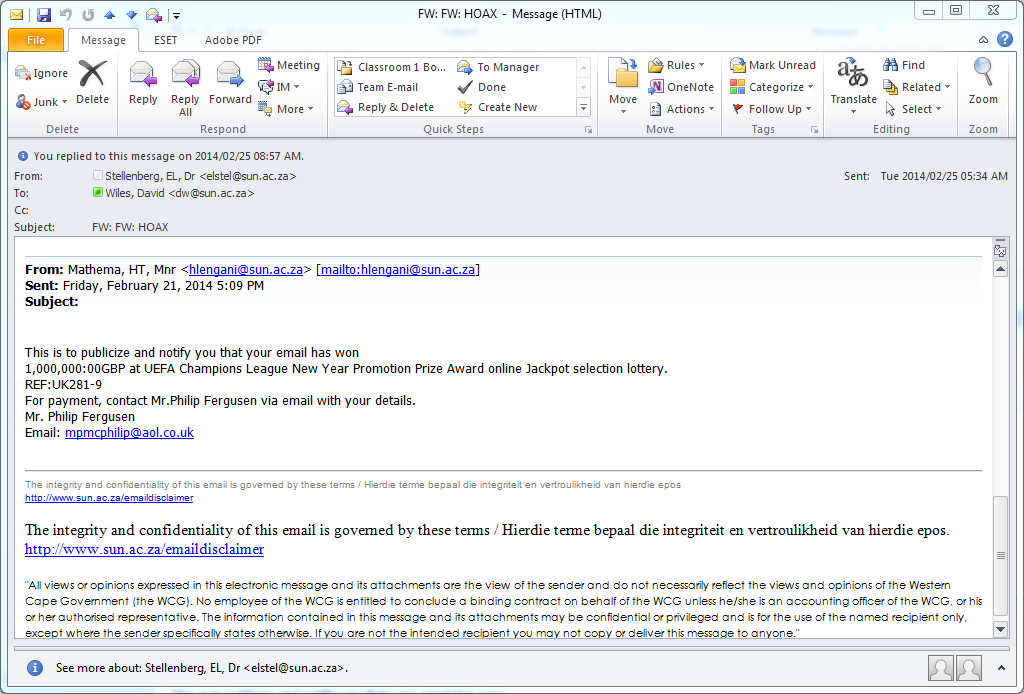
Below is an example of an phishing scam that has been sent out seemingly by a legitimate University-based e-mail account. Unfortunately this time, the e-mail message has been sent to other institution’s addresses and the university is being wrongly criticised for “allowing” this.
Remember: The only purpose of a phishing scam is to get victims to provide their personal information and thereby gain access and control of passwords, bank account numbers and personal details.
Information Technology will be investigating this incident but keep this in mind:
- Many times an automatic program is used to “spoof” or forge a phony e-mail address to disguise the real sender The address is often pulled from a database of “stolen addresses”.
- This university e-mail account owner might be a victim themselves of a phishing scam, and have provided their details to scammers, resulting in their address or computer being “hijacked” by the phishers.
- In some cases an e-mail address owner is employed by the phishers to operate and send out phishing mails on their behalf with the promise of earning money for their services. (Earn $10 000 per month and work from home) in this case it is unlikely, but nevertheless a risk.
In the screen grab below note the “honeypot”:
…There is no Subject line
…It seems to come from a university employee but the reply to address is some other address
…It promises that you have won a large amount of money. That always attracts people.
[ARTICLE BY DAVID WILES]


 Apparently bears find honey irresistible and in the same way hackers can’t resist the challenge to gain access to a computer or system.
Apparently bears find honey irresistible and in the same way hackers can’t resist the challenge to gain access to a computer or system. Thought it’s only you who felt the need to lose weight after last night’s McDonald’s happy meal? Your computer feels the same way, but for different reasons.
Thought it’s only you who felt the need to lose weight after last night’s McDonald’s happy meal? Your computer feels the same way, but for different reasons.