For some lucky people, it is time for the tax returns from SARS. The criminals know it too and every year at this time, users will get emails allegedly from SARS promising tax returns and asking you to click on a link, log in and provide your bank account details and password so they can pay you money!
This is a scam, and you should never respond or go to the site or open up the attached file, as this could compromise your banking security.
- SARS has your banking details on record and these are stored in secure and encrypted form. They do not need you to confirm or enter your banking details.
- SARS would always either SMS or send you a registered letter in the post to inform you of tax returns, etc. They would never contact you via unsecured e-mail, and furthermore they have enough of your data to address the mail to you PERSONALLY and not via some vague “Dear Taxpayer” salutation.
- There is no returnfund@sars.co.za address
- The attached file is usually a html (webpage) file that gives you a forged webpage sitting on the criminals server somewhere overseas.
- The amount that they promise to pay you is always something like R9,250.75
- Unless you have added your university e-mail address as the primary contact address on the SARS system you should never get mail on your university account.
If you do go to this site and you do enter in your banking account details, credit card details, passwords etc, this will allow the criminals to log into your bank account via the internet, and take control over your bank account. They will create themselves as beneficiaries and then transfer all your money to their account, and then delete all the evidence pointing to their account.
These scam e-mails will never stop. It is always difficult to block them too because scammers change their addresses, details and methods on a daily basis. So it is always best to dump these mails in the junk mail folder, blacklist the sending domain and delete the mail immediately.
Why do these criminals continue to send their mail? Because they catch people regularly. In 2012 South Africa was the 5th most phished country in the world behind India, Canada, the USA and the UK, with estimated figures of R14 million being stolen from South Africans last year alone.
[ARTICLE BY DAVID WILES]


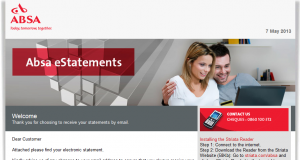 Recently another ABSA eStatement landed in our e-mail box, this time a little more sophisticated, but armed with a few basic tips you will be able to spot the scam quickly.
Recently another ABSA eStatement landed in our e-mail box, this time a little more sophisticated, but armed with a few basic tips you will be able to spot the scam quickly. Once of the most common questions we get asked by users is – How do these spammers get my e-mail address? Previously we looked at Rumpelstiltskin attacks, bots, trojans and zombies. This time around we focus at a third method – by using Subscribe/Unsubscribe newsletter services.
Once of the most common questions we get asked by users is – How do these spammers get my e-mail address? Previously we looked at Rumpelstiltskin attacks, bots, trojans and zombies. This time around we focus at a third method – by using Subscribe/Unsubscribe newsletter services. Once of the most common questions we get asked by users is “How do these spammers get my e-mail address?”
Once of the most common questions we get asked by users is “How do these spammers get my e-mail address?”