On the 17 April this year we sent out a warning to you about a phishing scam warning you “YOUR EMAIL HAS BEEN COMPROMISED” and giving you a link to “Certify your email HERE”
The mail was sent from a student account that has ALREADY really been compromised, by the criminals and they might already be using the account to launch further attacks.
Just because mail seems to come from a university address, doesn’t mean to say that it is legitimate.
The subject line is all in capital letters and is meant to frighten you into clicking on a link and filling in your details. This was probably how the original student account was compromised.
This is a typical phishing scam. Do not respond or click on any of the links. Many thanks to all our observant students and personnel who picked it up and pointed it out to me.
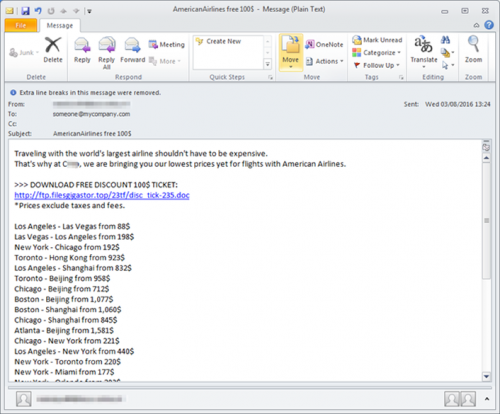
Below is an example of the mail (with the dangerous bits removed)
David Wiles
From: Compromised, Student account <12345678@sun.ac.za>
Sent: 2017/06/13 15:51 (GMT+02:00)
To: fake@email.address
Subject: YOUR EMAIL ACCOUNT HAS BEEN COMPROMISED
Certify Your email HERE
—
[ARTICLE BY DAVID WILES]