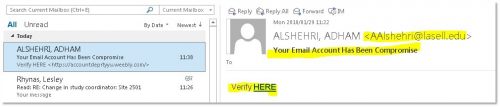
Several observant colleagues and some students have reported a number of phishing emails being sent (usually in pairs)Â from a university account in the United Kingdom. The subject is “IT ADMIN” with no salutation or any other information other than “You have a pending message click here to read”.
With some students still on their autumn break and many colleagues only returning this week from the short school holiday, mailboxes have filled up full, voicemails and Skype 4 Business voice messages might have been left and some might be fooled into thinking that a message from “IT ADMIN” *might* be important.
This is a common tactic used by phishing scammers to attempt to con their victims into giving their usernames and passwords.
Many phishing emails use short and cryptic messages to instil a sense of urgency to scare users into doing the attackers’ bidding. In this case, a short mail about a mysterious “pending message” requires the victims to click on a link in order to retrieve the message. In actuality, the link leads to a fake login page designed to collect the user’s login credentials and deliver them to the attackers.
You should always inspect all URLs carefully to see if they redirect to an unknown website – this scam links to weebly.com. Also look out for generic salutations, grammar mistakes, and spelling errors scattered throughout the email. There are several in this mail.
It is no coincidence that a compromised UK university email address has been used. Large institutions like universities, with large numbers of students and personnel, are always a challenge to protect and are choice targets for phishing attacks.
In the same way, some Stellenbosch University students and personnel are fooled by the scam and give the scammers their passwords and login details by filling them in on the fake login page. The original email account is discarded by the scammers and compromised Stellenbosch University accounts might be used. This has happened several times before.
So, do not be surprised if later this week there is a fresh breakout of these “pending message” mails from “IT ADMIN” but this time coming from Stellenbosch University student or personnel accounts. It is very important to report this to the IT Cyber Security team.
If you have received mail that looks like this, please immediately report it by sending the spam/phishing mail to help@sun.ac.za
and sysadm@sun.ac.za.Â
Attach the phishing or suspicious mail on to the message if possible.
1. Start up a new mail addressed to sysadm@sun.ac.za (CC: help@sun.ac.za)
2. Use the Title “SPAM” (without quotes) in the Subject.
3. With this New Mail window open, drag the suspicious spam/phishing mail from your Inbox into the New Mail Window. It will attach the mail as an enclosure and a small icon with a light yellow envelope will appear in the attachments section of the New Mail.
4. Send the mail.
[Article by David Wiles]