[:en]
Please be wary of receiving so-called “Bank Account Statements” or alleged payment/transaction notifications that arrive in your mailbox from one of South Africa’s banks. In most cases, they are phishing scams designed to fool you into willingly giving the criminals your bank account details and password/PIN code.
The warning signs are obvious, but the amount of email that we all get every day and the day-to-day stress of the workday, often make us miss the warning signs.
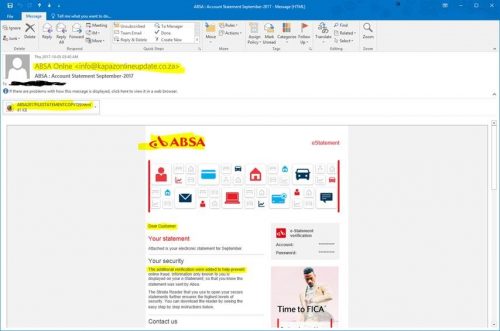
Below is a typical phishing scam some university accounts received this morning. It could just as well be FNB or Standard Bank, therefore it’s important that you note the warning signs:
- Do you have a bank account with the bank? If not why are they sending you an account statement?
- Unless you are directly responsible for your department’s finances and your department has a bank account with ABSA or your official university e-mail account is the contact address for your bank correspondence, you shouldn’t be getting emails from any bank.
- There is no personal salutation. Banks have your contact details and they will always address you personally, never as “Dear Customer”.
- The grammar and spelling are usually poor. This is because the scammers are often from countries where English isn’t the main language.
- There is always an attached file or link you should click on or open and type in your details including passwords to “verify” your identity. Email is NOT secure and revealing any details with this medium is very risky.
- Branding (e.g. logos and templates) of banks can easily be copied from the bank websites and forged. Just because the bank’s logo is in the e-mail it doesn’t make the mail is official.
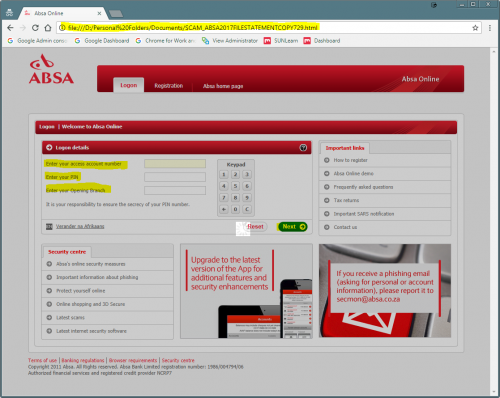
- The website you are taken to will not be the official address. Often these are compromised websites which have been hacked by criminals and used for identity theft. See the example below. The address in the address bar is clearly not ABSA’s address.
The phishing website looks like this – very similar to the login page of the ABSA website:
[ARTICLE BY DAVID WILES]
[:]
Tags: phishing

