[:en]
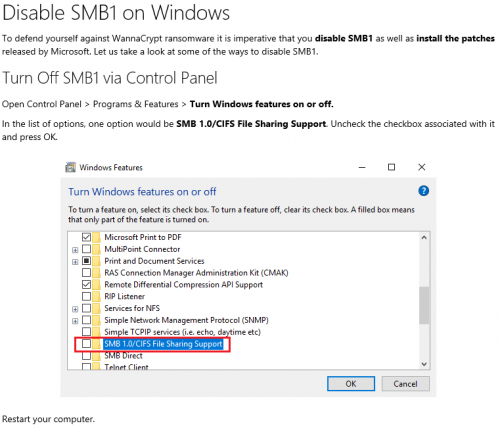
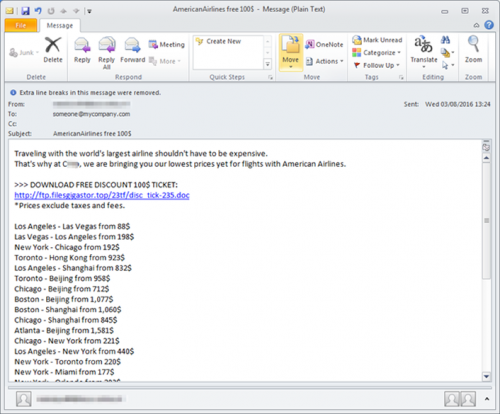
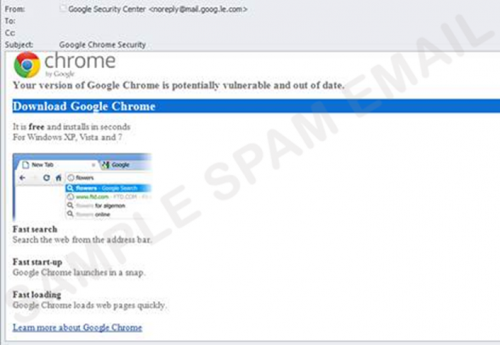
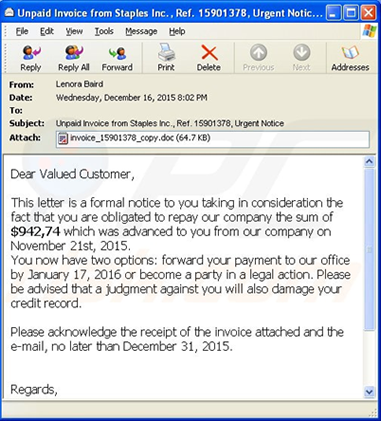
The destructive Petya ransomworm caused destruction and major interruptions of services around the world last week. Unfortunately, it’s becoming progressively more difficult to avoid these attacks as cybercriminals become more clever and inventive in their methods. While there are ways to prevent that you fall prey to such an attack, there’s one thing you can do which will ensure that you are safe. And it’s not technical or difficult to do.
Once a week, backup all your data. Yes, this is a menial, boring administrative task – and we all hate those, but by ensuring that your data is safe and sound elsewhere, it won’t matter if your PC is infected by ransomware or any other malware. If you do lose your data, you will have another version available.
Here are a few quick tips to help you:
- Choose one day a week which suits you and make an appointment in your diary to do a weekly backup.
- Try not to overwrite your previous backup. Rather make consecutive copies in various folders on your external hard drive or on your network space and name each with the particular day’s date. If any of the documents become corrupt for some reason, you can always fall back on a previous version.
- Regularly check that the medium on which you made your backup is still in working order and you’re able to access your documents.
- Use more than one backup medium, for example, your network space AND an external hard drive.
Where should you backup data?
- Each staff member has access to his/her own network space (usually the h-drive) where you can save an allocated amount of data for free. You have 1GB at your disposal to backup your most critical documents. At an extra cost of R10-00 per 1GB this space can also be increased. This network space is also available via the web at storage.sun.ac.za if you find yourself away from the SU network.
- On your departmental network space (usually the g-drive). The departmental drive can be used for files used by more than one person and 15GB is allocated to each department. SharePoint can also be used by groups for sharing documents.
- OneDrive allows each staff member 5TB of storage space. This is available via the Office365 suite. https://portal.office.com/
- If you choose to have your data close at hand, get yourself an external hard drive. Never save important data on a flash drive – its sole function is for transporting data from one device to another and is not a dependable medium for backup. Just ensure that these devices are stored somewhere else (not also in your office) or in a safe. If confidential, SU documents are kept on an external hard drive, files have to be protected with a password or encrypted. Keep in mind that if you lose the password, not even IT can salvage your data.
- Alternatively, you can save data in the cloud. We’ve already mentioned OneDrive, but GoogleDrive or Dropbox are also examples of this. It is extremely important that cloud storage is only for personal use, not for any academic information or sensitive data. Also keep in mind that if you use more than one device, you have to sync data across devices and this will incur costs.
More tips on backups, as well as activating Windows’ automatic backup function on www.backblaze.com.
[:af]
Die vernielsugtige ransom-wurm Petya het laasweek verwoesting regoor die wêreld gesaai en vele kritiese dienste onderbreek. Ongelukkig raak dit toenemend meer moeilik om hierdie tipe aanvalle te vermy, aangesien kuberkriminele slimmer raak en al meer inisiatief aan die dag lê. Hoewel daar maniere is om te voorkom dat jy in die ransomware-slaggat trap, is daar een ding wat jou sonder twyfel sal beskerm. En dis nie te tegnies of te moeilik om te doen nie.
Rugsteun jou data eenmaal ʼn week. Ja, dis ʼn vervelige, sieldodende, administratiewe taak en ons almal haat admin ewe veel – maar deur net dit te doen, verseker jy dat jou data veilig is. Selfs al word jou rekenaar oorgeneem deur ransomware of enige ander malware, het jy ekstra weergawes daarvan beskikbaar elders.
Hier is ʼn paar vinnige wenke om jou te help:
- Kies een dag in die week wat jou pas en skeduleer ʼn afspraak in jou dagboek om ʼn weeklikse rugsteun te doen.
- Probeer om nie oor vorige rugsteundokumente te skryf nie. Maak eerder opeenvolgende kopieë in verskeie vouers op jou eksterne hardeskyf of netwerkspasie met elkeen se datum as beskrywing. Indien enige van die dokumente korrup word, sal daar altyd ʼn vorige weergawe beskikbaar wees.
- Gaan gereeld jou rugsteun-medium na en maak seker dat dit nog in ʼn werkende toestand is en jy toegang tot jou dokumente kan kry.
- Gebruik meer as een rugsteun-medium, byvoorbeeld jou netwerkspasie EN ʼn eksterne hardeskyf.
Waar moet jy jou data rugsteun?
- Elke personeellid het toegang tot sy/haar eie netwerkspasie (gewoonlik die h-skyf) waar jy ʼn vasgestelde hoeveelheid data gratis kan stoor. Jy het 1GB tot jou beskikking om die mees kritiese dokumente te stoor. Die spasie kan ook vermeerder word teen ʼn ekstra koste van R10-00 per 1GB. Jou netwerkspasie is ook beskikbaar via die web by storage.sun.ac.za indien jy nie op kampus is nie.
- Departementele netwerkspasie (gewoonlik die g-skyf). Die departementele netwerkspasie kan gebruik word vir leêrs wat deur meer as een persoon gebruik word en 15GB word aan elke departement toegeken. SharePoint kan ook deur groepe gebruik word om dokumente te deel.
- OneDrive bied 5TB stoorspasie per personeellid. Hierdie diens is beskikbaar via die Office365 suite. https://portal.office.com/
- Indien jy verkies om jou data naby te hou, kry vir jou ʼn eksterne hardeskyf. Moet nooit belangrike data op ʼn flitsskyf stoor nie – die enigste doel daarvan is om data van een toestel na ʼn ander te skuif. Dis nie ʼn betroubare rugsteun-medium nie. Maak ook seker dat jou rugsteun-mediums elders gebêre word of in ʼn kluis (nie in jou kantoor nie). Indien jy US-dokumente op ʼn eksterne hardeskyf stoor, MOET dit met ʼn wagwoord beveilig word of enkripteer word. Hou ook in gedagte dat indien jy die wagwoord verloor, IT nie jou data weer sal kan opspoor nie.
- Laastens kan jy ook jou data in die wolk stoor. OneDrive is een voorbeeld van wolkberging, maar GoogleDrive of Dropbox is ander opsies. Wolkberging is slegs vir persoonlike gebruik en nie vir enige akademiese of sensitiewe data nie. Onthou ook dat, indien jy meer as een toestel het, jou data op alle toestelle sinkroniseer moet word en kostes noodwendig betrokke is.
Vir meer wenke en hoe om Windows se outomatiese rugsteun-funksie te aktiveer, lees gerus op www.backblaze.com.
[:]