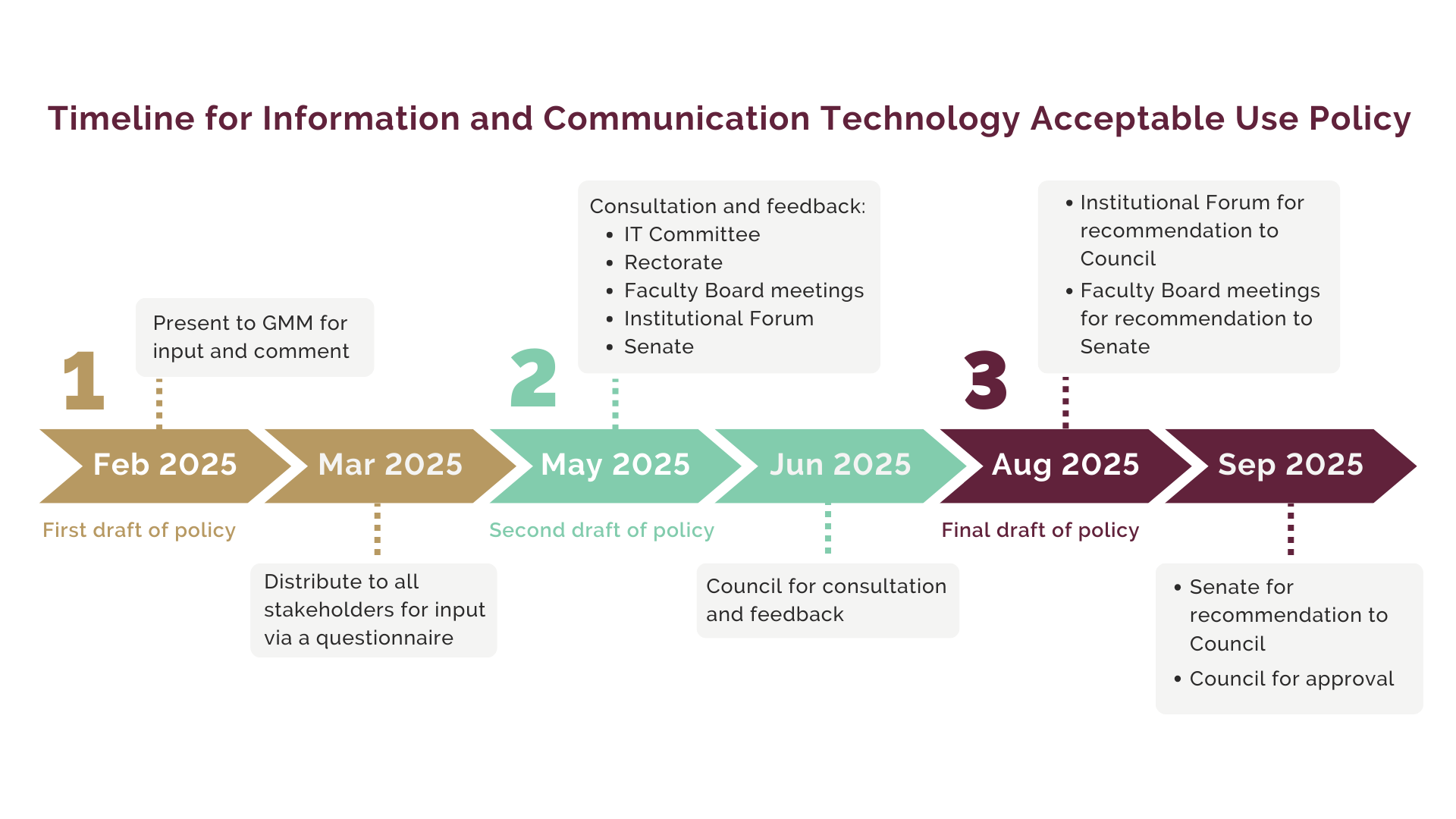
Stellenbosch University’s Information Technology Division is rolling out upgrades to Windows 11 to ensure all university devices remain secure, up to date and optimised for performance. With Microsoft ending support for Windows 10, it is critical that devices transition to Windows 11 to continue receiving security updates and technical support.
The IT configuration team has now made the Windows 11 upgrade available to all compatible Windows 10 devices. If your device is eligible, you can complete the upgrade at a time that suits you.
How to upgrade
If your device is compatible:
1.Click on Start > Settings > Update & security > Windows update.
2. Look for Windows 11, version 24H2 under View optional updates.
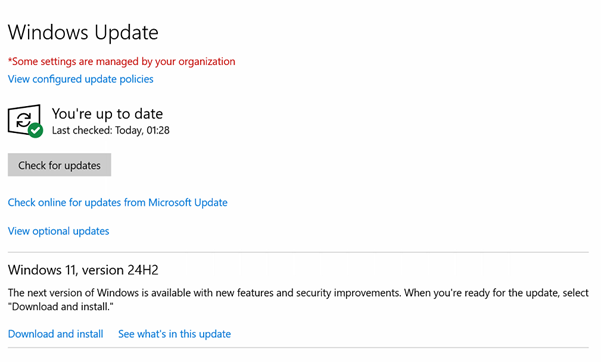
3. Select Download and install to begin the upgrade.
4. You can continue working while the installation takes place. You’ll be prompted when a restart is required.
If you do not see the Windows 11 upgrade listed, your device may require assessment. Please log a request via the ICT Partner Portal, select “Upgrade my computer” and complete the form. A technician will then contact you to assess your device and advise on the next steps.
Why upgrade?
- Enhanced security: Windows 11 includes advanced security features and improved integration with Microsoft Defender for Endpoint, providing better protection against modern cyber threats.
- Improved performance: Experience faster start-up times, better power management and optimised performance – particularly on newer hardware.
- Modern software compatibility: Windows 11 is designed to support cloud-based platforms, AI-enhanced applications and modern productivity tools, all in line with SU’s governance and compliance standards.
What happens if you don’t upgrade?
- Increased security risks: Without critical updates, Windows 10 devices become vulnerable to malware, ransomware and data breaches.
- Compliance concerns: Using unsupported software can lead to non-compliance with SU’s cybersecurity policies.
- Reduced efficiency: Older systems often slow down and are harder to maintain, leading to productivity loss and increased support needs.
What if my device isn’t compatible with Windows 11?
Some older devices may not meet Windows 11’s hardware requirements. If your device is ineligible, it may be time to upgrade. You can request a quote for a Windows 11-compatible device by logging a “Get new hardware” request via the ICT Partner Portal.
Don’t delay – upgrade today
Upgrading to Windows 11 isn’t just a visual update – it’s a critical step towards a more secure, efficient and future-ready digital workspace. While transitions can bring short-term inconvenience, the long-term benefits far outweigh the risks of staying on outdated software.