You’ve received a suspicious email, what should you do with it? Firstly, don’t click on any links. But just as important, send it to us so we can prevent more staff and students falling prey to the scam. We encourage our customers to submit potential phishing examples for review. Using these submissions, the Cyber Security Incident Response Team (CSIRT) can learn from the analysis of these messages. This collectively helps to improve the level of virus and spam detection.
What is phishing?
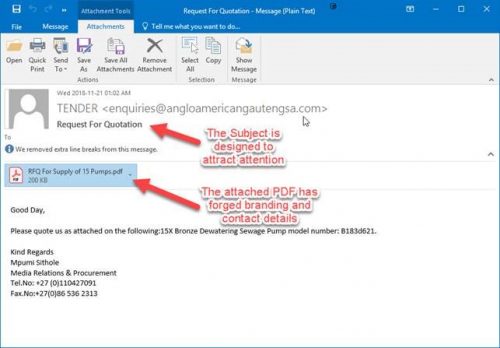
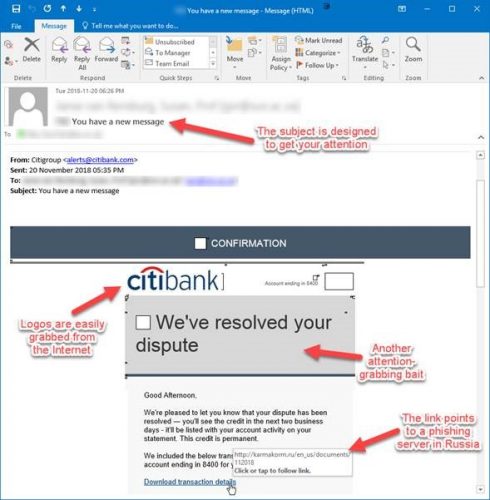
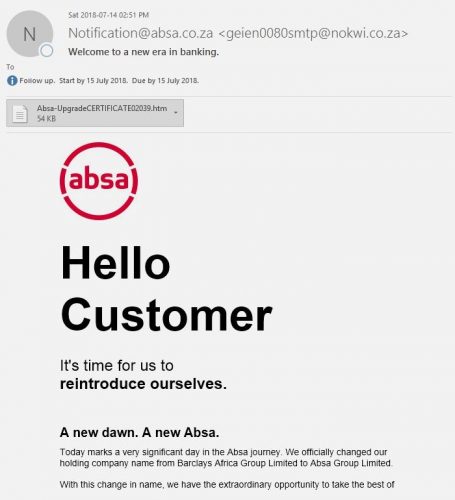
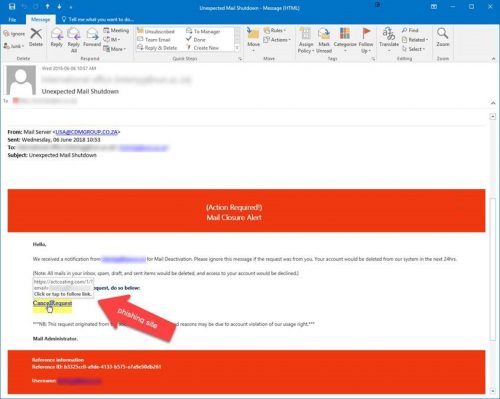
Phishing attacks are designed to steal a person’s login and password details so that the cyber criminal can assume control of the victim’s social network, email, and online bank accounts. Seventy percent of internet users choose the same password for almost every web service they use. This is why phishing is so effective, as the criminal, by using the same login details, can access multiple private accounts and manipulate them for their own good.
More on how to recognise a phishing email.
Report phishing
On the ICT Partner Portal:
- Go to https://servicedesk.sun.ac.za/jira/servicedesk/customer/portal/6/create/115
- Fill in your information and add the email as an attachment. Your request will automatically be logged on the system.
*Spam or phishing examples must be sent in either.EML or .MSG format as an attachment and must not be forwarded. This ensures the original email can be analysed with its full Internet message headers intact. Alternatively, use the mail application to save the email (usually located under File | Save As) as an .EML or .MSG format to a folder location, and attach the saved file to a new email.