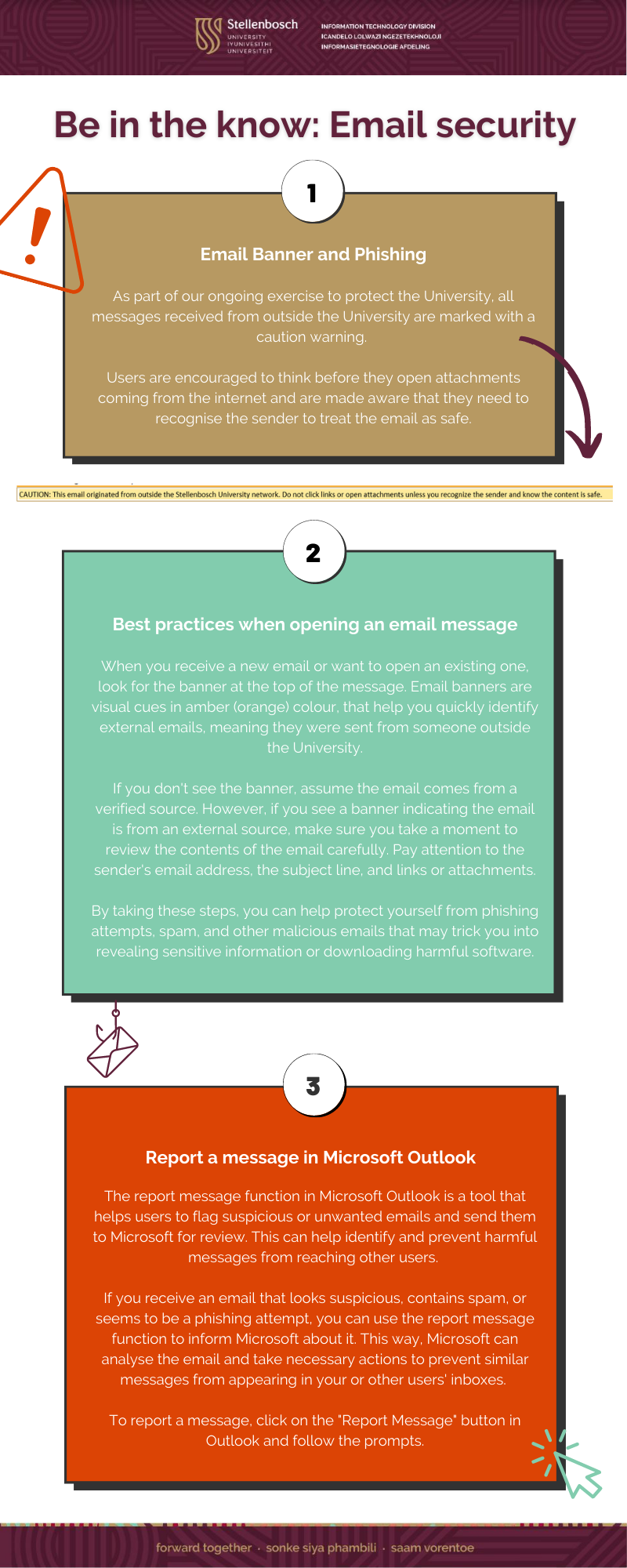
Why Windows Updates are crucial for your device’s health
This article was compiled by Elnita Jacobs, Computer Technician 1: IT General Support Services, and Bradley van der Venter, Senior Configuration Specialist: IT General Support Services.
In today’s world with the ever-changing threat landscape, keeping our devices up to date is essential for ensuring they run smoothly and securely. Windows Updates is one of the most critical updates we need to keep up with.
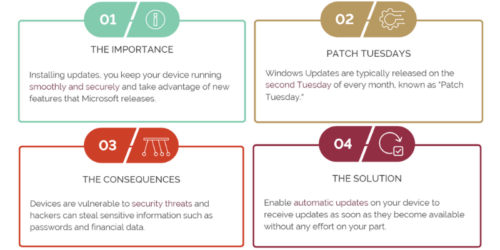
1 – The Importance
Firstly, let’s talk about why installing Windows Updates is so important. These updates are designed to fix bugs and vulnerabilities in the operating system, improve performance, and add new features. This means that by installing updates, you can keep your device running smoothly and securely and take advantage of new features that Microsoft releases. Windows Updates can also help to protect your device from malware and other security threats, making them a critical part of your device’s overall security.
2 – “Patch Tuesdays”
It’s also worth noting that Windows Updates are typically released on the second Tuesday of every month, known as “Patch Tuesday”. This means that by default, Windows Updates are enabled to install automatically, and you can expect your device to receive updates shortly after this date each month. Additionally, if you fail to restart your device after updates have been installed, Windows will force a restart after seven days to ensure compliance.
Please note that this is not enforcement from Stellenbosch University (SU) but from Microsoft.
This is important to keep in mind, as it ensures that your device stays up-to-date and secure, even if you forget to restart after installing updates. For example, suppose you restart your device immediately after updates are installed. In that case, you minimise the risk of, for example, being in a meeting and then Windows notifying you that it will restart in approximately 20 minutes.
This will only happen if you haven’t restarted your device for more than seven days after installing the Windows Updates.
3 – The Consequences
Now, let’s consider the consequences of failing to install Windows Updates. First, when you fail to update and restart your device, you leave it vulnerable to security threats. Hackers can exploit the operating system’s vulnerabilities to gain access to your device and steal sensitive information such as passwords and financial data. Malware can also infect your device, causing it to slow down, crash, or render unusable. Additionally, failing to update your device can result in poor performance, as bugs and other issues can accumulate over time, making it harder to use your device efficiently.
One of the most significant risks of not updating your device is the possibility of data loss. If your device becomes infected with malware or crashes due to bugs, you may lose important data such as documents, photos, and videos. This can be devastating, particularly if you have not backed up your data. Additionally, if you use your device for work, you may risk losing valuable business data, which can be catastrophic for your business.
4 – The Solution
What can you do to ensure that you are keeping your device up to date? The simplest solution is to enable automatic updates on your device (Stellenbosch University Windows Asset devices joined to the domain have this enabled by default). This will ensure that your device receives updates as soon as they become available without any effort on your part. Alternatively, you can manually check for updates by going to the Windows Update in the Settings option on the Start Menu. Restarting your device regularly after installing updates is also important, as this ensures that they are fully installed and can take effect.
In conclusion, installing Windows Updates is crucial for ensuring your device runs smoothly and securely. By keeping your device up to date, you can take advantage of new features, improve performance, and protect yourself from security threats. Failing to update and restart your device for updates can lead to poor performance, data loss, and security vulnerabilities. So, ensure you enable automatic updates or manually check for updates regularly, and always restart your device after installing updates.
Reference: