[:en]
 With a fast internet connection and unlimited, “free” internet, it’s possible to download movies and series to your heart’s content. Unless you use a pay streaming platform it’s also illegal. Additionally, if you use the university’s network and/or devices it’s also a breach of the university’s Electronic Communications Policy – a policy all students and staff agree to when they annually activate their network access. Therefore your network access can be revoked if you are caught downloading and hosting illegal content.
With a fast internet connection and unlimited, “free” internet, it’s possible to download movies and series to your heart’s content. Unless you use a pay streaming platform it’s also illegal. Additionally, if you use the university’s network and/or devices it’s also a breach of the university’s Electronic Communications Policy – a policy all students and staff agree to when they annually activate their network access. Therefore your network access can be revoked if you are caught downloading and hosting illegal content.
Up to a few years back television networks and film companies weren’t geared to trace and stop downloading and distribution of illegal movies. It was just too difficult and not cost-effective. This is no longer the case – even in South Africa. Everything you do online can be tracked and traced.
Information Technology receive regular notifications from companies such as Warner Bros. and Columbia Pictures indicating that illegal, copyrighted material is being downloaded and seeded (distributed) from IP addresses within the university’s network. These emails include the specific IP address which we can trace to the user, the material downloaded and distributed and at which times. When we receive these notifications, we immediately send an email to the user of the address with a written warning. If they do not comply, these companies will take legal action.
The distribution or seeding of copyrighted material without a licence is both a criminal and civil offence in South Africa, even if distribution takes place from BitTorrent. Just because it’s available via a torrent, it doesn’t mean it’s legal.
In South Africa, under the Copyright Law of 1978, you can be sentenced for up to 5 years in prison and a fine of up to R10,000 for each item you distribute. Between 2010 and 2012, 200,000 people have been sued for uploading and downloading copyright material via BitTorrent.
So before you download the latest episode of your favourite series or stream movies from an illegal file sharing site, consider the consequences. There are many legal options to watch media online, from Netflix to Showmax, so rather be safe and legal.
MORE INFORMATION:
How does BitTorrent and seeding work?
http://en.wikipedia.org/wiki/BitTorrent
http://www.bittorrent.com/help/guides/beginners-guide
Example of a warning letter:
We are writing this letter on behalf of Columbia Pictures Industries, Inc. (“Rights Holder”) who own certain rights under copyright law in the title White House Down.
You are receiving this notice because your Internet account was identified as having been used recently to copy and/or distribute illegally the copyrighted motion pictures and/or television shows listed at the bottom of this notice. This notice provides you with the information you need in order to take immediate action that can prevent serious legal and other consequences. These actions include:
1. Stop downloading or uploading without authorization any motion pictures or TV shows owned or distributed by Rights Holder; and
2. Permanently delete from your computer(s) all unauthorized copies you may have already made of these movies and TV shows.
If this notice is being received by an Internet Service Provider (ISP), please forward the notice to the individual associated with the activities.
The unauthorized distribution or public performance of copyrighted works constitutes copyright infringement under the Copyright Act, Title 17 U.S Code Section 106(3)-(4). This conduct may also violate the Berne Convention for the Protection of Literary and Artistic Works and The Universal Copyright Convention, as well as bilateral treaties with other countries that allow for protection of Rights Holder copyrighted works even beyond U.S borders.
Below is the detail for your reference:
– ————- Infringement Details ———————————-
Title: White House Down
Timestamp: 2013-09-19T23:18:28Z
IP Address: 146.232.***.**
Port: *****
Type: BitTorrent
Torrent Hash: *************************************
[SOURCE: http://mybroadband.co.za]
[:af]
 Met `n vinnige internetkonneksie en onbeperkte, “gratis” internet is dit vandag moontlik om die nuutste flieks en reekse af te laai. Indien jy nie `n betaal stroomplatform gebruik nie, is dit ook onwettig. Verder, as jy die universiteit se toerusting en/of netwerk gebruik, is dit `n oortreding van die Elektroniese Kommunikasiebeleid – `n beleid wat elke student en personeellid onderteken wanneer hulle jaarliks netwerktoegang heraktiveer word. Gevolglik kan jou netwerktoegang ook opgehef word as jy onwettige materiaal aflaai en aan ander gebruikers verskaf.
Met `n vinnige internetkonneksie en onbeperkte, “gratis” internet is dit vandag moontlik om die nuutste flieks en reekse af te laai. Indien jy nie `n betaal stroomplatform gebruik nie, is dit ook onwettig. Verder, as jy die universiteit se toerusting en/of netwerk gebruik, is dit `n oortreding van die Elektroniese Kommunikasiebeleid – `n beleid wat elke student en personeellid onderteken wanneer hulle jaarliks netwerktoegang heraktiveer word. Gevolglik kan jou netwerktoegang ook opgehef word as jy onwettige materiaal aflaai en aan ander gebruikers verskaf.
Tot `n paar jaar gelede het TV-netwerke en filmmaatskappye nie te veel moeite gedoen om die aflaai en verspreiding van onwettige flieks en reeks te kniehalter nie. Dit was eenvoudig te moeilik en nie koste-effektief nie. Dis egter nie meer die geval nie.
Informasietegnologie ontvang gereeld e-posse van maatskappye soos Warner Bros. en Columbia Pictures wat aandui dat onwettige, kopiereg materiaal afgelaai en versprei word vanaf IP-adresse binne die universiteit se netwerk. Hierdie e-posse sluit die presiese IP-adres wat die onwettige materiaal afgelaai het, sowel as die naam van die materiaal wat afgelaai en versprei is, in. IT word gevolglik genoodsaak om die persoon aan wie die adres behoort te kontak en `n skriftelike waarskuwing te gee.
Die verspreiding (seeding) van kopieregmateriaal sonder `n lisensie is beide `n kriminele en siviele oortreding in Suid-Afrika, selfs al is die verspreiding oor BitTorrent. In Suid-Afrika, onder die Kopiereg Wet van 1978, kan dié oortreding jou in die tronk laat beland vir tot 5 jaar en `n boete van tot R10,000 vir elke item wat jy versprei.
Tussen 2010 en 2012, is 200,000 mense gedagvaar vir die oplaai en aflaai van kopieregmateriaal deur BitTorrent.
So, voordat jy die nuutste episode van jou gunsteling reeks gou aflaai, oorweeg eers mooi of jy die kans wil waag. Dis dalk veiliger om van `n wettige diens soos Netflix of Showmax gebruik te maak.
MEER INLIGTING:
Hoe werk BitTorrent en “seeding”?
http://en.wikipedia.org/wiki/BitTorrent
http://www.bittorrent.com/help/guides/beginners-guide
[:]

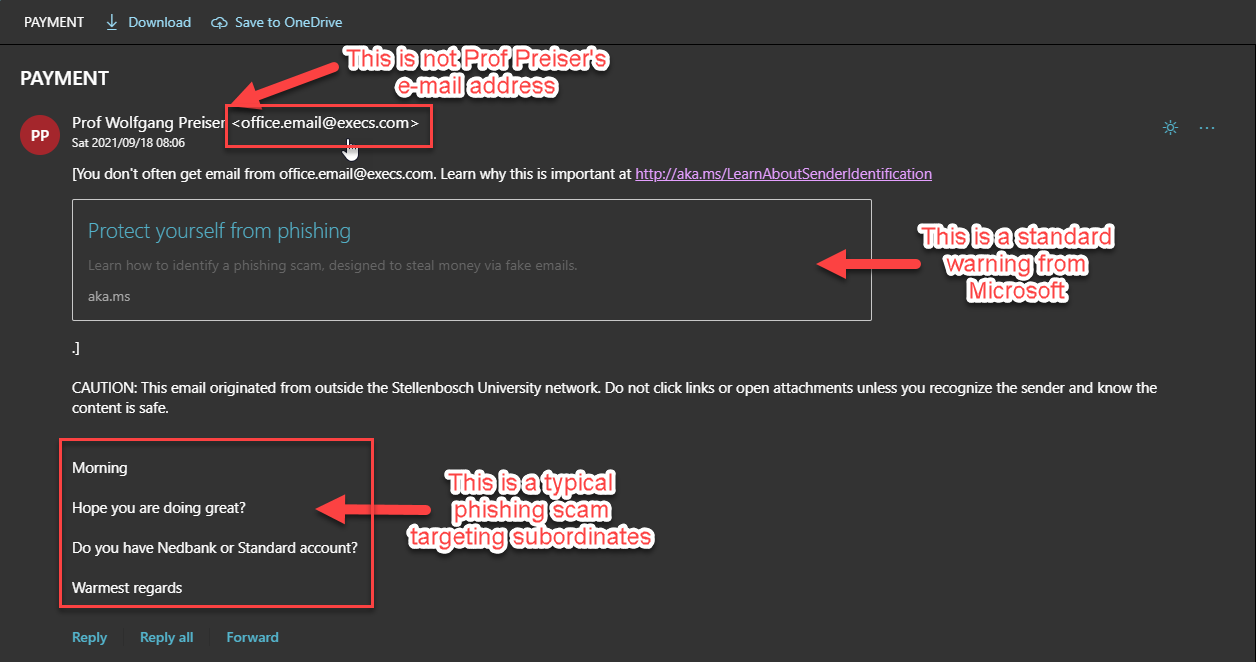

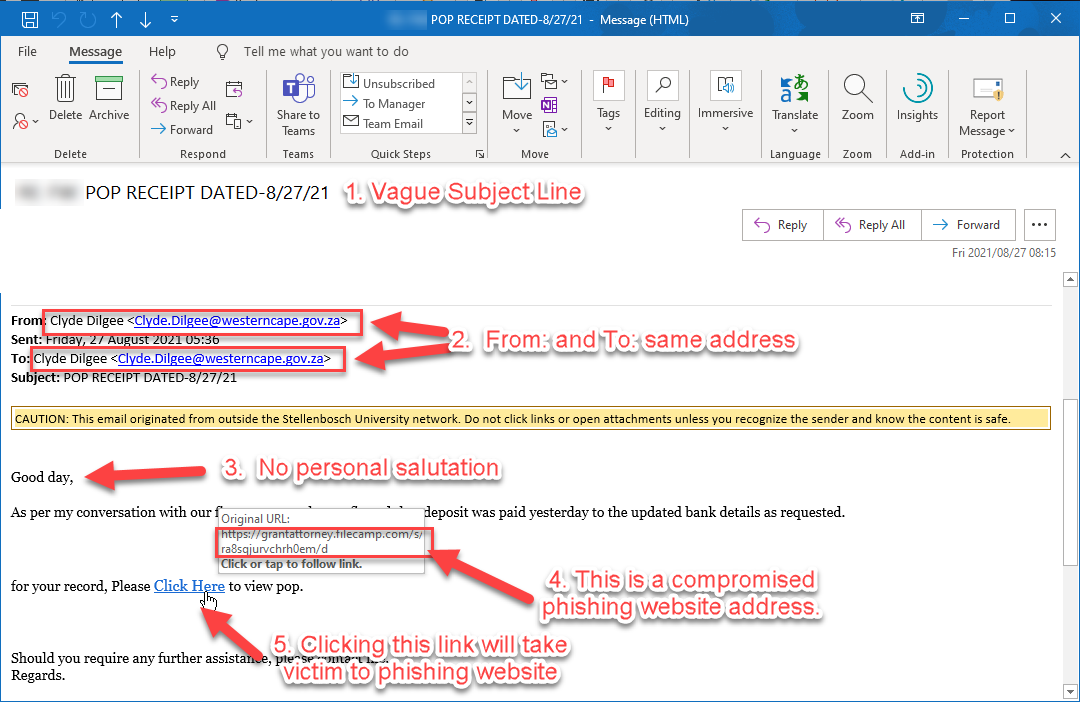

 The Protection of Personal Information Act (4 of 2013) (POPIA) is in full effect from 1 July 2021. A brief summary of the POPIA Act is available
The Protection of Personal Information Act (4 of 2013) (POPIA) is in full effect from 1 July 2021. A brief summary of the POPIA Act is available  With a fast internet connection and unlimited, “free” internet, it’s possible to download movies and series to your heart’s content. Unless you use a pay streaming platform it’s also illegal. Additionally, if you use the university’s network and/or devices it’s also a breach of the university’s
With a fast internet connection and unlimited, “free” internet, it’s possible to download movies and series to your heart’s content. Unless you use a pay streaming platform it’s also illegal. Additionally, if you use the university’s network and/or devices it’s also a breach of the university’s