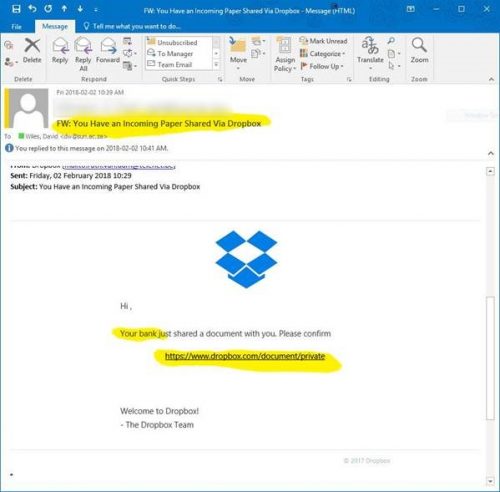
Several staff are receiving a ŌĆ£threateningŌĆØ e-mail with the subject ŌĆ£<your email address> DO NOT IGNORE THE WARNINGŌĆØ
Your e-mail address will be inserted at the begining of the message, and then proceeds to inform you about your account being used for ŌĆ£spam activitiesŌĆØ and that it will be blacklisted and permanently suspended.
Here is an example of the mail (with all the dangerous stuff removed)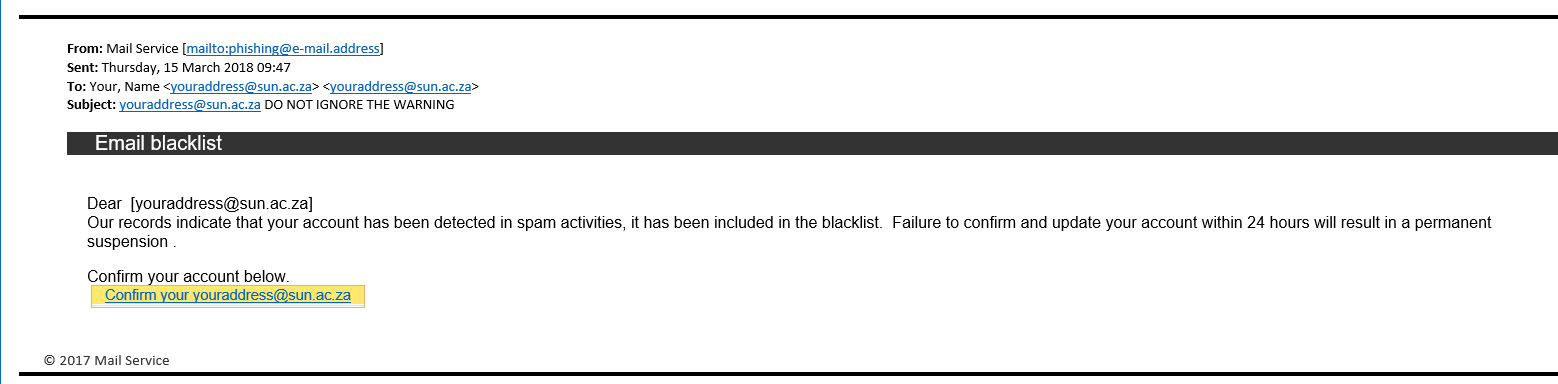
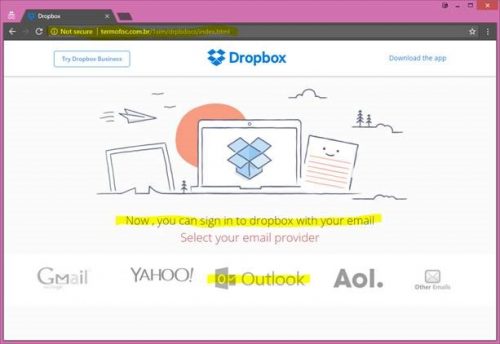
If you are fooled into clicking on the link, you will be taken to a website (based in Zimbabwe) and your e-mail address will be automatically inserted in the field, and you will be asked to type in your password, and then the scammers will have gained access to your network account!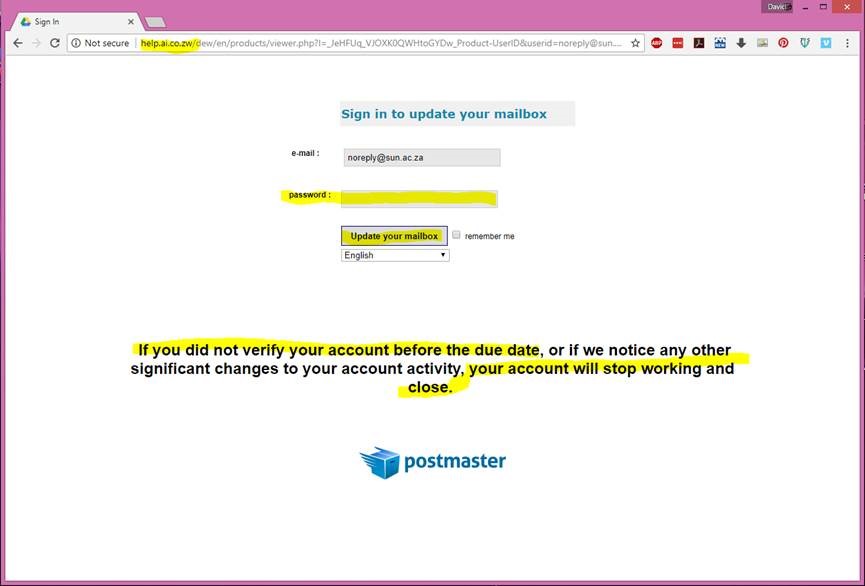
This is a typical tactic employed by phishers targeting university e-mail accounts. They use your contact details and intimidating language to cause you to panic and ŌĆ£click on the link they provide.
When spotting phishing scams remember:
- DonŌĆÖt trust the display name.
- Look but donŌĆÖt click.
- Check for spelling mistakes.
- Analyse the salutation.
- DonŌĆÖt give up personal information – ever.
- Beware of urgent or threatening language in the subject line.
- Review the signature (remember the universityŌĆÖs own centennial celebration and ŌĆ£water-wiseŌĆØ branding is being used in *some* external phishing attacks)
- DonŌĆÖt click on attachments.
- DonŌĆÖt trust the header from an email address.
- DonŌĆÖt believe everything you see.
Phishers are extremely good at what they do. Just because an email has convincing brand logos, language, and a seemingly valid email address, does not mean that itŌĆÖs legitimate. Be sceptical when it comes to your email messagesŌĆöif it looks even remotely suspicious, donŌĆÖt open it.
If you have received mail that looks like this, please immediately report it to the Information Technology Security Team using the following method:
Send the spam/phishing mail to the following addresses:┬Āhelp@sun.ac.za┬Āand sysadm@sun.ac.za.┬Ā
Attach the phishing or suspicious mail on to the message if possible. ┬Ā
- Start up a new mail addressed to sysadm@sun.ac.za (CC: help@sun.ac.za)
- Use the Title ŌĆ£SPAMŌĆØ (without quotes) in the Subject.
- With this New Mail window open, drag the suspicious spam/phishing mail from your Inbox into the New Mail Window. It will attach the mail as an enclosure and a small icon with a light yellow envelope will appear in the attachments section of the New Mail.
- Send the mail.
[Article by David Wiles]