There are reports that some students and personnel have already received this mail in their mailboxes. It is a typical phishing scam but uses a different tactic to trick the recipient into divulging personal details like passwords and should not be responded to in any way. That mail was sent by a “throwaway” outlook.com mail account. It started making its appearance in June last year in Yahoo!Mail accounts.
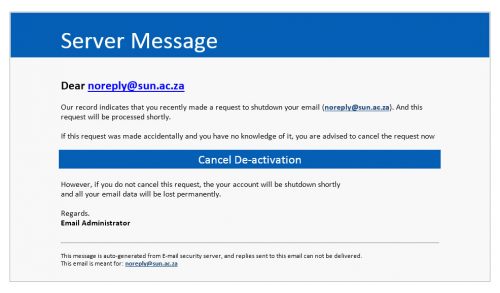
According to this e-mail, which claims to be a “Server Message”, telling the potential victim that they recently initiated an action to shut down their e-mail account. The e-mail advises that, if they did not initiate the supposed shut down action, they should click a ‘Cancel De-activation’ link to restore your account to its normal settings.
However, the e-mail is not from the university, and no account shut down action has been initiated. The e-mail is just a crude phishing scam designed to steal your university account login details. The scammers hope that at least a few recipients will click the cancel link in the mistaken belief that they must do so to save their account.
If you do click the link, you will be taken to a fraudulent web page that has been built to emulate a genuine login screen. A form on the page asks you to enter your e-mail address and account password and click a button labelled ‘Sign in to Cancel De-activation”. After signing in on the fake page, you will be automatically redirected to the university webmail website.
Meanwhile, the scammers can collect the login details you entered and use them to hijack your university e-mail account. Once they have gained access to your account, they can use it to send out spam and scam e-mails in your name. (as has been happening in recent weeks)
E-mail phishing scams like this one are very common. Be very wary of any e-mail that claims that you must click a link or open an attached file to rectify a supposed account problem. It is always safer to log into all of your online accounts by entering the address into your browser’s address bar or via an official app.
Here is an example of the mail that is in circulation with the dangerous parts removed.
[ARTICLE BY DAVID WILES]


 How the Junk E-mail filter works
How the Junk E-mail filter works