About a year ago a new version of the ABSA Bank phishing email hit the university email server. What was new about this version was that the email was in Afrikaans. Although the Afrikaans was not perfect with some spelling and grammar mistakes, it still could have fooled many people, because of the “familiarity” component.
Stellenbosch University still uses a lot of Afrikaans as its primary official communications medium, and many automated systems like the Financial system use Afrikaans to inform users of payments etc. While there is nothing wrong with this, phishing scammers have latched onto this and are now attempting to fool people into divulging their personal details using Afrikaans in their phishing e-mails.
We were warned early this morning about an email that was originating from UCT with dangerous content, and almost immediately the UCT phishing emails started arriving.
Here is what to look out for:
Mail will arrive from a forged or compromised “UCT address” that will look like this:
From: Anna Huang [mailto:forged_address@myuct.ac.za]
Sent: 19 July 2017 10:53 AM
To: Recipients <forged_address@myuct.ac.za>
Subject: Re: betaling aan jou rekening
Goeiemore,
Vind aangehegte betalingsbewys.
Dankie
Disclaimer – University of Cape Town This e-mail is subject to UCT policies and e-mail disclaimer published on our website at http://www.uct.ac.za/about/policies/emaildisclaimer/ or obtainable from +27 21 650 9111. If this e-mail is not related to the business of UCT, it is sent by the sender in an individual capacity. Please report security incidents or abuse via csirt@uct.ac.za
The disclaimer from the University and the Afrikaans could fool some people if they are not careful.
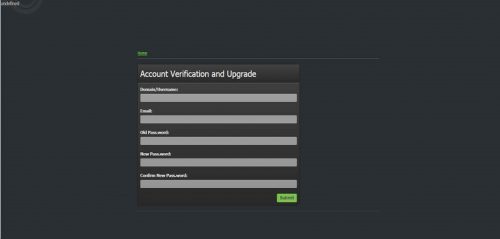
The dangerous part is actually an attached html files (sometimes it might look like a PDF) that will present you with a login page where you will be asked to give your e-mail address and your password to “view this payment”
The login page will look like this, in this version:
The actual server’s address is also hidden by encoding it, so to the untrained eye, nothing will look suspicious. This is a typical phishing scam, but with the “sender” coming from a neighbouring academic institution, and the language being Afrikaans, we need to be even more alert.
[Article by David Wiles]