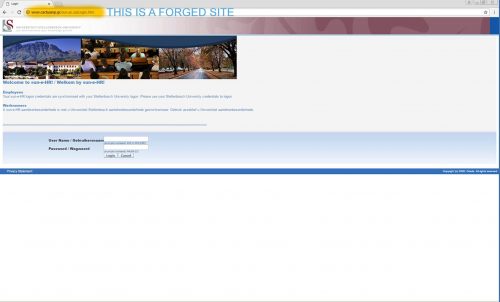
Weak and reused passwords continue to be a common entry point for account or identity takeover and network intrusions. Simple steps and tools exist to help you achieve unique, strong passwords for your accounts.
 A password is often all that stands between you and sensitive data. It’s also often all that stands between a cyber criminal and your account. Below are tips to help you create stronger passwords, manage them more easily, and take one further step to protect against account theft.
- Always: Use a unique password for each account so one compromised password does not put all of your accounts at risk of takeover.
- Good: A good password is 10 or more characters in length, with a combination of uppercase and lowercase letters, plus numbers and/or symbols — such as pAMPh$3let. Complex passwords can be challenging to remember for even one site, let alone using multiple passwords for multiple sites; strong passwords are also difficult to type on a smartphone keyboard (for an easy password management option, see “best” below).
- Better: A passphrase uses a combination of words to achieve a length of 20 or more characters. That additional length makes it’s exponentially harder for hackers to crack, yet a passphrase is easier for you to remember and more natural to type. To create a passphrase, generate four or more random words from a dictionary, mix in uppercase letters, and add a number or symbol to make it even stronger — such as rubbishconsiderGREENSwim$3. You’ll still find it challenging to remember multiple passphrases, though, so read on.
- Best: The strongest passwords are created by password managers — software that generates and keeps track of complex and unique passwords for all of your accounts. All you need to remember is one complex password or passphrase to access your password manager. With a password manager, you can look up passwords when you need them, copy and paste from the vault, or use functionality within the software to log you in automatically. Best practice is to add two-step verification to your password manager account. Keep reading!
- Step it up! When you use two-step verification (a.k.a., two-factor authentication or login approval), a stolen password doesn’t result in a stolen account. Anytime your account is logged into from a new device, you receive an authorization check on your smartphone or another registered device. Without that second piece, a password thief can’t get into your account. It’s the single best way to protect your account from cyber criminals.
Resources
- Check out http://twofactorauth.org to see a list of services that offer two-step verification.
- Learn more about passwords and securing your accounts from the National Cyber Security Alliance.
- Consider whether a password manager is the right choice for you.
- Explore Five Ways to Upgrade your Password this Password Day, which is observed in May each year.
- Find more videos and a quiz at http://passwordday.org.