We are working on a modern website that is user-friendly, informative and reflective of our SU identity. Thank you for your patience.

We are working on a modern website that is user-friendly, informative and reflective of our SU identity. Thank you for your patience.

SEPTEMBER 2024
As per the annual calendar, Information Technology will conduct its quarterly scheduled maintenance on IT infrastructure components from Friday, 6 September, at 21:00 until Monday, 9 September, at 07:00.
Although every attempt will be made to limit interruptions, various IT services and systems will be affected and can become unavailable during this time – partly or entirely.
For inquiries, please log a request on the ICT Partner Portal.
JUNE/JULY 2024
As per the annual calendar, Information Technology will conduct its quarterly scheduled maintenance on IT infrastructure components from Friday, 28 June, at 21:00 until Monday, 1 July, at 07:00.
APRIL 2024
As per the annual calendar, Information Technology will be conducting its quarterly scheduled maintenance on IT infrastructure components from Friday, 5 April, at 17:00 until Monday, 8 April, at 07:00.

SUNid announcement: Transitioning to a new platform | August 2024
SUNid will soon be upgraded to a new and improved platform, enhancing security and management of third-party access. Detailed instructions and an overview of the new features will be shared over the next few weeks.
We understand that transitioning to a new platform can be difficult. The following resources will be made available throughout the transition:

Changes to Microsoft 365 storage plans from 1 August 2025
Globally, Microsoft announced a change in their storage plans for the Enrollment for Education Solutions (ESS) upon contract renewal. This includes Stellenbosch University (SU). Similar to Google’s recent storage updates, these changes are designed to enhance security, minimise environmental impact and promote educational innovation.
These changes were initially set to take effect on 1 August 2024. However, following a successful business case presentation, SU has received an extension until 1 August 2025. This means the changes will not immediately impact you as a user, but we would like to encourage you to collaborate with IT to manage your storage efficiently in the interim.
Please see the guide: Microsoft 365: Use your storage effectively
OneDrive and SharePoint file versions

File versioning in SharePoint and OneDrive keeps a detailed history of changes, including the date/time and the user who made the change. Users with appropriate permissions can view, delete and restore specific versions if they have the correct permissions. SharePoint automatically saves versions when you click “Save” or autosave every few minutes.
Your files are automatically saved as versions, allowing you to track changes and revert to older versions if needed.
For security reasons, file versioning for OneDrive and SharePoint will be limited to five versions (to restrict access to a limited number of files). You will be notified when this limit is reached.
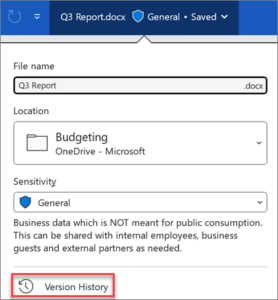
How to view previous versions of a file
Open the file you want to view.
Click the title of your file and select Version history.
Select a version to open it in a separate window.
If you want to restore a previous version you’ve opened, select Restore.
*Source: Microsoft Support

MS Teams recordings will now be retained for 60 days by default. After this period, recordings will automatically be deleted. We recommend that minutes be taken as soon as possible after the meeting and that recordings be deleted as soon as the minutes have been approved.
Other things to note:

An Outlook online archive mailbox can store older email messages where they won’t occupy space in your primary mailbox. This specialised mailbox appears alongside your other mailbox folders in Outlook. Emails older than one year will be moved automatically to Outlook’s Online Archive (no user action is required).
Operating system: Outlook for Windows
Operating system: Outlook for Mac
Your Online Archive folder will appear in Outlook for Mac if you have a Microsoft 365 account.
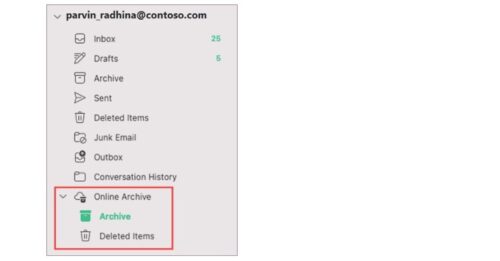
Note: New Outlook for Mac supports only the mail module. If you moved folders, calendar items, contacts, tasks, or notes to your archive in any other version of Outlook, such as Outlook for Windows, you won’t be able to view them in the online archive mailbox using the new Outlook for Mac.

Exciting updates are on the horizon for Microsoft 365 users, bringing improvements to enhance your digital workspace experience. In this blog post we delve into the recent changes impacting the number of file versions that are automatically stored.
File versioning in SharePoint and OneDrive keeps a detailed history of changes, including the date/time and the user who made the change. Users with appropriate permissions can view, delete and restore specific versions if they have the correct permissions. SharePoint automatically saves versions when you click “Save” or with autosave every few minutes.
Your files are automatically saved as versions, allowing you to track changes and revert to older versions if needed.
For security reasons, file versioning for OneDrive and SharePoint will be limited to ten versions (to restrict access to a limited number of files). You will be notified when this limit is reached.
How to view previous versions of a file
Open the file you want to view.
Click the title of your file and select Version history.
Select a version to open it in a separate window.
If you want to restore a previous version you’ve opened, select Restore.

*Source: Microsoft Support
Refer to the infographic below for more information on navigating these changes. Stay informed and connected with Microsoft 365’s evolving landscape.
© 2013-2025 Disclaimer: The views and opinions expressed in this page are strictly those of the page author(s) and content contributor(s). The contents of this page have not been reviewed or approved by Stellenbosch University.