When COVID-19 struck, the various teams working on the ground to ensure that Stellenbosch University (SU) runs seamlessly on all technological fronts suddenly faced enormous challenges.
Almost overnight, the technological needs in all sectors of the university – from System Administration to IT services, Student Support, and End User Support – had to shift to accommodate remote working.
Post-COVID, all these divisions have had to adapt to a new normal of hybrid working, teaching and learning. And, in true SU style, despite the unprecedented rollercoaster ride, all these teams have risen to the occasion ŌĆō and are optimistic about the campusŌĆÖs technological future.

Mario Randelhoff, Manager of System Administration, described the past two years as ŌĆ£one of the most challenging times of my lifeŌĆØ. He and his 10-strong team of system and database administrators run all the critical computing systems which the university uses relating to emails, the human resources system, and the learning management system, etc.

ŌĆ£ItŌĆÖs our task to manage the configurations to ensure emails are sent securely from users on campus to external users. In terms of managing the learning management system, which is all on-premises in our data centre, we look after the machines, do installations, and manage security updates. We ensure the overall learning management system platform is always up to date and available. Managing the Human Resources system means we have to ensure all the technology for leave requests, salary payments, performance assessments, pension information etc., is up and running,ŌĆØ he said.
MarioŌĆÖs department faced numerous challenges during COVID, many of which remain. ŌĆ£One thing was non-negotiable – the business of the university had to go on during lockdown,ŌĆØ Mario said. ŌĆ£From being spoilt with everybody being onsite in the universityŌĆÖs buildings and knowing where all the problems and hotspots were, everybody became separate ŌĆ£companiesŌĆØ that had to be serviced.
ŌĆ£When everybody started working remotely, we had to move fast to set up the technology to allow users to access the systems from where they were. We had to cater for very large numbers of users trying to access the systems and ensure they did this securely when accessing our more sensitive systems. This could not be done via the open internet without security.┬Ā
ŌĆ£Gearing our learning management system for 100 percent remote work was a massive task. We had to obtain more servers as well as build capacity to ensure the system worked fast and efficiently. We didnŌĆÖt want students to click on a page and then wait ten minutes to log in.┬Ā
ŌĆ£The fact that everybody was working remotely brought many issues to the fore ŌĆō we had to put cybersecurity measures in place to ensure people didnŌĆÖt click on phishing emails and to protect them from viruses.
ŌĆ£We also had to roll out laptops.┬ĀBecause of the culture of the university, many people working from their offices or the computer labs on campus didnŌĆÖt necessarily have devices they could use from home.┬Ā
ŌĆ£It was stressful all over, getting to the new normal of working remotely while ensuring users had the same experience they would have had if they were working in the office. One of our biggest challenges as an operations team was that we couldnŌĆÖt meet face-to-face. We had to adapt to online meetings. Then loadshedding would interrupt meetings, so we had to roll out UPS to team members so they could at least have a sustainable internet connection while working remotely.ŌĆØ┬Ā
Mario continued: ŌĆ£With COVID, lockdown, and loadshedding, it was a very stressful time. I had to coordinate everything from the systems side, and I also had to motivate my team to implement the changes in a short time.ŌĆØ
Mario, a father of two, said he never lost sight of the numerous personal struggles and work pressure he, his staff and all the university members were facing. What got him through, he said, is the fact that he does not get stressed out. ŌĆ£When others are stressing, thatŌĆÖs when I perform at my best.ŌĆØ
A challenge his department faces now is that having gotten through COVID, remote work has become ŌĆ£a hindranceŌĆØ. ŌĆ£It is hard to keep a group dynamic going if everybody is working remotely. We do at least go in to work on Mondays for a face-to-face meeting. We also need to rebuild the interactions with the other technological teams.ŌĆØ
Another challenge, he said, is that the division currently has five vacancies, ŌĆ£but, in the post-COVID era, people have got used to working remotely and are not actually going for jobs where they need to be on site. This is a new problem that we are really experiencing firsthand.
Asked what new tech and other innovations are in the pipeline in his division, Mario said: ŌĆ£Technology has evolved so much we have to start onboarding more cloud services. We will start looking at migrating certain systems, such as our learning management system, to a cloud provider so we can scale it to many more people.
ŌĆ£From a team perspective, we have to work hard to change the mindset from traditional system administrators to thinking about being cloud architects and looking at deployment architecture and how to componentise the systems we look after. ThatŌĆÖs where the mind shift needs to happen.ŌĆØ┬Ā
Allister Lesar, Head of ICT Student services,┬Āand his team are tasked with assisting students in all their ICT requirements to study, research, learn and achieve their goals at the university.
During COVID, he and his team of seven people had to quickly evolve and assist with quickly helping students and staff become capable of accomplishing their tasks remotely and enable remote learning from anywhere. They also had to roll out laptops to 2500 students overnight.
 ┬Ā
┬Ā
ŌĆ£We worked round the clock to ensure they received their laptops. Then we had to assist the students remotely with repairs and ensure the repaired laptops were couriered to them so their studies were not interrupted. We sent laptops to students in cities as well as in remote areas in Northern Cape and Limpopo.
ŌĆ£We also had to roll out WIFI hotspots as far as we could across the campus so that those students who were unable to go home could study safely on campus, in venues with limited numbers of people at a certain time. We shifted from a walk-in service for IT queries and repairs to an appointment basis only and we had to enable our remote workforce ŌĆō who were accustomed to walk-in, face-to-face service – to assist students remotely.ŌĆØ
Allister said that, in the post-COVID era, students want to maintain the services of loaned laptops and remote working. ŌĆ£TheyŌĆÖve got used to studying in their rooms or at home, in uncrowded areas and are still asking for these resources. For instance, some students feel unsafe walking to the computer labs at night. While it is not financially viable to maintain this, we are trying to leverage programmes to assist them in that regard.ŌĆØ
Asked whatŌĆÖs in the technological pipeline in his division, Allister said they are looking at mobile device management solutions to enable remote services for students. We intend to secure all our endpoints so staff and students can use any device to study. For this to happen, we need to be able to pick up issues before theyŌĆÖve even happened.ŌĆØ┬Ā
The COVID and post-COVID period have been tough, Allister said. ŌĆ£I worked till three in the morning and got up at seven to ensure the students got the help they needed. As a team, we galvanised each other by putting ourselves in the studentsŌĆÖ shoes and imagining their strain. We drew on whatever energy we had. ThatŌĆÖs what got us through. We focused on how to best help them through the situation.ŌĆØ

Ronel Reynecke, Head: End User Support┬Āand her 15-strong team, of whom some are based at the IT student centre and the rest at the main IT building, oversee the technical support for staff on campus.
“During COVID, the division had to instantaneously change from supporting users onsite to supporting users remotely to the best of our ability. That brought challenges on its own, as more remote support meant more licenses on the software we used to help our users, which of course, had a cost implication for IT. But, on the bright side, our users quickly became familiar with this software and we sometimes had to smile when, without even asking for the user ID, the users would start giving the ID almost before we could say good morning.

“Teams and Zoom (to a lesser extent) quickly became the default meeting platform, and specialised equipment followed in the lecture halls. It involved a great deal more work for the team and they had to do a lot of ŌĆśhand holdingŌĆÖ to some staff to manage webinars and online meetings and to lecturers to implement the hybrid mode of teaching.
ŌĆ£Many things shifted for us. In terms of the devices we service, previously, there was a good divide between desktops and laptops, but during COVID, it immediately changed to laptops. We had large orders coming through for laptops, leading to insufficient storage space for all the devices while configuring the devices.┬Ā
“Then there was also the global semi-conductor shortage which led to a shortage of chips to make for example, laptop screens. COVID didnŌĆÖt help and, while our delivery is normally two to three weeks, in some cases, it took almost a year, to get laptops.”
Further challenges included that ŌĆ£technicians who were accustomed to providing end-user support had to become Jacks of all trades. They also had to assist users with their home setups, and deal with internet connectivity issues, third-party software and printing issues at home. We had to connect everyone who had never worked from home or used VPN (virtual private networks) to access secure systems; and we had to migrate users who were still working on old VPN clients. We also had to explain to users that Anti-Virus updates had to run before VPN could connect and that it is enabled for MFA (multifactor authentication) which all contributed to better network security.ŌĆØ
Ronel said her team experienced a real ŌĆ£generational divideŌĆØ, with the younger generation being better equipped for the technological changes than the older generation.
“Then there was also a digital divide, where some students did not have the funds to purchase laptops and data for connectivity. She said her team experienced first hand the fall-out of having to learn and teach new technologies. They had work to complete with deadlines and the new technology was strange and frustrating for them. So, apart from doing the normal IT tasks, they also calm the users down! We were almost like psychologists because people got so upset.┬Ā ┬Ā
“In the end, this took a huge toll on my staff, as some of them were even verbally abused by staff as they wanted to be helped instantaneously, never thinking that we might have had a rollover of calls.”
Ronel said several changes have already taken place in her department, and some are still to come. “The developments in the pipeline to improve customer experience include implementing Microsoft Intune (Microsoft cloud-based unified endpoint management service) to help manage the software of onsite and offsite devices; the hybrid joining of devices to Azure Active Directory to enable use of the full functionality of the Microsoft stack; and, the possible use of Windows as a service ŌĆō a method of testing and releasing Windows features faster – to simply the work of IT support staff.”
When asked to look back on the challenges of COVID, and what was achieved, Ronel said: ŌĆ£COVID brought so many hardships and such heartache, but it pushed the boundaries in terms of our digital strategy. Tech experts predicted it could take up to seven years to get to where we are now and that all happened in the past two years. We had to push the boundaries and get into an entirely new digital era.┬Ā
“My team and I learnt so much. In fact, I feel so empowered, having learnt so much and I know that we can do even more when we work together as a team. We should learn from our experience and embrace the change.ŌĆØ

Petro Uys, Head: IT Service Desk,┬Āand her team of six people are tasked with first-level troubleshooting with all IT-related queries.
ŌĆ£We receive a very high volume of calls ŌĆō especially since COVID meant that many people are working from home. This development added numerous requirements among users.┬Ā
ŌĆ£A key part of our work is to pick up trends, for instance, if people start calling in and say they canŌĆÖt access SUNlearn – our learning management system – my team must immediately inform me so that we can deal with the issue. We immediately inform the second and third levels of the trends. It is vital for us to pick up trends and escalate them to get to the root cause. ŌĆ£Before COVID, when everyone was on campus it was easy to, for instance, change your password. Now that users are based at home, they cannot change their password and connect without issues. They must take additional steps for their new password to be recognised on their laptop. It was a huge challenge just to get people connected from home.ŌĆØ
ŌĆ£Before COVID, when everyone was on campus it was easy to, for instance, change your password. Now that users are based at home, they cannot change their password and connect without issues. They must take additional steps for their new password to be recognised on their laptop. It was a huge challenge just to get people connected from home.ŌĆØ
Petro said the technological needs dealt with by her team had shifted substantially during COVID. ŌĆ£Our first challenge was to set up our team to be able to work from home. Some only had ADSL and limited connectivity from home.┬Ā
ŌĆ£On the customer side, they were frantic – they didnŌĆÖt know how to connect from home; for instance, a VPN is needed for specific purposes, such as working with the financial or HR system. We spent a lot of time just calming the users down and telling them it was not that bad!
ŌĆ£Other challenges were to get our information out to users in good time. From an IT side, it takes time to get the right information to the people because you need to test it and ensure itŌĆÖs the correct information. For example, people have different cell phones. We introduced multifactor authentication just to verify our staff members, but it was challenging because people struggled to verify themselves.
ŌĆ£So, testing and verifying information and getting it to our people was vital. We had to ensure our service catalogue was up to date every day.ŌĆØ
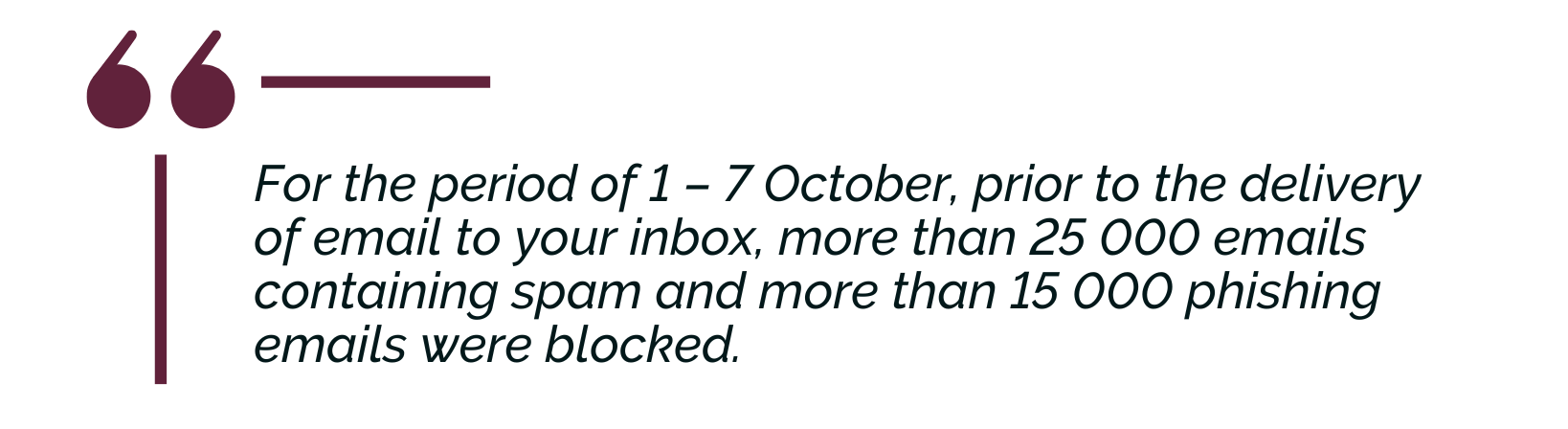
Petro added that the IT Service Desk has been receiving numerous security-related service requests.┬ĀŌĆ£This includes SPAM and spoofing emails. Users must be empowered with information from IT to be able to deal with these in the correct way. They must not open these emails and click on the links in the emails, or provide their credentials, as this can result in their accounts being compromised.
ŌĆ£The IT Service Desk acts as a gatekeeper and must have sufficient knowledge to protect users from doing the wrong thing, especially if they donŌĆÖt know what to do.ŌĆØ
Asked whatŌĆÖs in the pipeline in terms of new directions and new technologies, Petro said a key task among her staff members is ŌĆ£to get them to really understand what the university is about, and to motivate them to strive to work towards the universityŌĆÖs vision and mission, so we all work towards the same goal”.┬Ā
ŌĆ£In terms of technology, I am pushing to start using chatbots and AI to enable self-service for users with queries. I also hope to implement extended service hours in our division. Currently, we work from 8 am to 4.30 pm, Monday to Friday. ThatŌĆÖs not good enough in the modern world. We must look at our service hours, especially with all the loadshedding.ŌĆØ
Asked how she dealt with the challenges, Petro said: ŌĆ£IŌĆÖm an in-the-moment person. I make the best of every moment and donŌĆÖt overthink things. That really got me through the pandemic. I knew that I had to just carry on and to motivate the people we were dealing with. I just made sure I was present for my team and for those I served.ŌĆØ