 As we enter into the new academic year, there are a lot of expectations, concerns, excitement and opportunities that await. Thanks to the pandemic, SUNLearn has become the central platform for Learning, Teaching and Assessment, exactly as it was originally envisaged.
As we enter into the new academic year, there are a lot of expectations, concerns, excitement and opportunities that await. Thanks to the pandemic, SUNLearn has become the central platform for Learning, Teaching and Assessment, exactly as it was originally envisaged.
That said, a system or ecosystem of platforms and tools, is only as good as the people who use it and support it. The Learning Technologies team is located in both the Centre for Learning Technologies and in Information Technology. These two teams ensure that both the systems (IT) and end-users (CLT) are supported to meet the needs of the different modes of delivery for Learning and Teaching at SU.
Allow us to give you a brief overview of who we are and what we do.
Learning Technology Systems: Academic IT
This team is managed by Lianne Keiller who performs her duties as Relationship Manager for the Learning and Teaching Responsibility Centre. Her role is to ensure that the faculties and Division for Learning and Teaching Enhancement are supported in accessing IT services and that IT responds to the needs of these environments.
Within this team, Mphonyana Wessels works directly with vendors and suppliers who provide 3rd party software solutions for Learning and Teaching. Her role is primarily to facilitate the discussions between Faculty Blended Learning Coordinators, the End-User Support Team, and Academic IT. Mphonyana also serves as a direct line manager to the Extended Learning Spaces (ELS) support teams. The ELS project allows in-class live streaming for students who are not physically on campus.
Lucky Liremi is the resident technical guru in the LTS team. His work is to ensure all back-end investigations, systems and testing are done. Lucky works collaboratively with our internal and external partners to respond as quickly as possible to any requests that staff and students make for assistance with SUNLearn, SUNStream and a number of other systems.
Aphiwe Ngunge can be found on campus, moving between the IT Hub and the IT building. Aphiwe is available to answer student queries on the use of SUNLearn, and/or provide one-on-one training to students to ensure that they are getting the most out of their SUNLearn experience.
Learning Technologies Support Desk: Centre for Learning Technologies
Morris Samuels manages this team as an Advisor in the CLT environment. With his team of four (4) members, they strive to provide a range of services that enables teaching and learning through the use of technology to be efficient, and where possible, enhanced. On a daily basis, the 5-member support team provides support for a variety of queries. Two additional staff members have recently been appointed to assist specifically with Hybrid Learning Queries.┬Ā With over 30 000 active users on SUNLearn, it is often a challenge to respond as quickly as the requests and queries come in. The majority of queries are responded to within 1 hour and it is their aim to continue to improve on our turnaround time on support queries.
All queries can be made via:
https://learnhelp.sun.ac.za┬Āor by calling 021 808-2222
What the service desk offers:
- Telephonic support desk function
- Basic SUNLearn training for Staff
- Departmental training
- Individual consultations
- Telephonic and Service Desk Support for e-assessment
Types of queries the service desk are able to assist with:
|
Component
|
Description
|
|
SUNOnline
|
SUNOnline course queries by Facilitators and participants
|
|
Assessment
|
Setting up assessments, request for assessment monitoring, student queries
|
|
SUNLearn Teams support
|
Activation requests for module Team spaces
|
|
Streaming and Class Capturing
|
SUNStream
Techsmith Relay
|
|
Camtasia Studio
|
Training, License requests, Troubleshooting
|
|
3rd Party Feature Support
|
Cengage, Matlab, Mcgraw-Hill, Software, Faculty e-books
|
|
Respondus
|
Respondus, Exam view, Lockdown browser & Monitor
|
|
SUNLearn Feature Requests
|
Moodle plugin and new feature requests
|
|
Turnitin requests
|
Turnitin assignment settings, paper removal requests, general troubleshooting
|
|
Lecturer Support
|
Advisory, Guidance & Training
|
|
Clickers
|
SUNLearn clicker tool, Booking of clicker devices
|
Queries the Learning Technologies support team are unable to assist with:
- Password expiring ŌĆō Please contact help@sun.ac.za for these queries.
- SUN access and use ŌĆō Please contact help@sun.ac.za for these queries.
- Short course registration or issuing of certificates ŌĆō Please contact the short course division for these queries.
- BYOD (Bring Your Own Device) server issues and support – Please contact your faculty CUA (Computer User Area) manager for these issues
- Final upload of theses ŌĆō Please contact scholar@sun.ac.za
- They are also not responsible for library related access or use and are therefore unfortunately unable to accommodate requests of this nature.
[ARTICLE BY LIANNE KEILLER]
 Due to critical maintenance by TENET, our internet service provider, internet services will be down on Sunday, 27 February from 00:00 am to 03:00 am.
Due to critical maintenance by TENET, our internet service provider, internet services will be down on Sunday, 27 February from 00:00 am to 03:00 am.


 As we enter into the new academic year, there are a lot of expectations, concerns, excitement and opportunities that await. Thanks to the pandemic, SUNLearn has become the central platform for Learning, Teaching and Assessment, exactly as it was originally envisaged.
As we enter into the new academic year, there are a lot of expectations, concerns, excitement and opportunities that await. Thanks to the pandemic, SUNLearn has become the central platform for Learning, Teaching and Assessment, exactly as it was originally envisaged.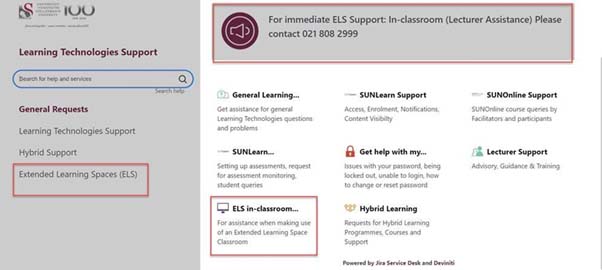


 A new multi-language management feature was recently implemented on the REDCap platform for researchers.┬Ā
A new multi-language management feature was recently implemented on the REDCap platform for researchers.┬Ā