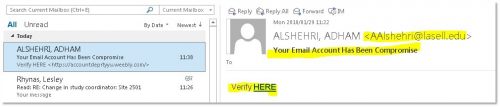
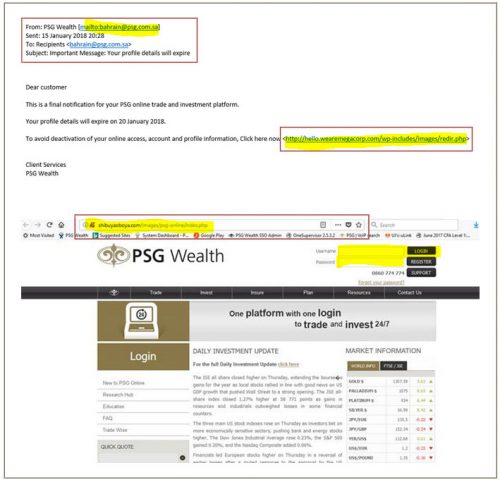
Several students and personnel have informed us of a “new” mail making its rounds on our campuses.
The sender is “Postmaster” with the subject of “Email Expired”. This phishing scam tells you that your e-mail account will shortly expire and uses scare tactics to convince you to “click” on a link to activate your email.
Information Technology will never send you this type of email, ask you to click on a link or provide your username or password. Do not respond to these emails or click on links.

If you have received mail that looks like this please immediately report it to the Information Technology Security Team using the following method:
Send the spam/phishing mail to the following addresses
help@sun.ac.za and sysadm@sun.ac.za.
Attach the phishing or suspicious mail on to the message if possible. There is a good tutorial on how to do this at the following link (Which is safe) : http://stbsp01.stb.sun.ac.za/innov/it/it-help/Wiki%20Pages/Spam%20sysadmin%20Eng.aspx
- Start up a new mail addressed to sysadm@sun.ac.za (CC: help@sun.ac.za)
- Use the Title “SPAM” (without quotes) in the Subject.
- With this New Mail window open, drag the suspicious spam/phishing mail from your Inbox into the New Mail Window. It will attach the mail as an enclosure and a small icon with a light yellow envelope will appear in the attachments section of the New Mail.
- Send the mail.
IF YOU HAVE FALLEN FOR THE SCAM:
If you did click on the link of this phishing spam and unwittingly give the scammers your username, e-mail address and password you should immediately go to http://www.sun.ac.za/useradm and change the passwords on ALL your university accounts (making sure the new password is completely different, and is a strong password that will not be easily guessed.) as well as changing the passwords on your social media and private e-mail accounts (especially if you use the same passwords on these accounts.)
IT has set up a website page with useful information on how to report and combat phishing and spam. The address is: https://blogs.sun.ac.za/it/en/2017/11/reporting-spam-malware-and-phishing/
[Article by David Wiles]