There have been reports of personnel and students getting numerous “spam” messages from DirectAxis Financial Services offering financial loans at 5% interest. This email is sent from a number of “throwaway” e-mail addresses like outlook.com, Hotmail and webmail.co.za.
Some students and personal are struggling to manage their finances and these “offers” can be very tempting.
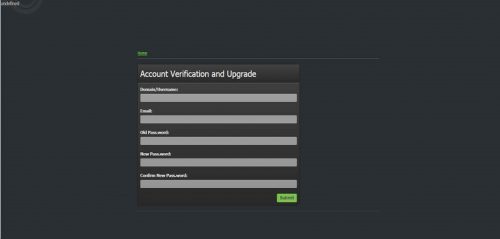
There are usually attached PDFs with each message where the company advertises loans and abnormally low-interest rates, and although currently there is no embedded malware or links to servers where you would be asked to give your user name and password, the spammers nevertheless ask you for your ID NUMBER, Full Names, Occupation, Monthly income and Contact details, which can be used for identity theft.
Although DirectAxis is a legitimate South African microlender, in the past, their company letterhead has been forged and used by criminals to commit fraud. Secondly, this particular Company has a number of charges against it by the Direct Marketing Association of South Africa for using ”spam databases” to spam millions of South Africans with their adverts. This puts them in violation of the “Protection of Personal Information Act” [http://www.justice.gov.za/legislation/acts/2013-004.pdf]
Don’t be fooled by companies offering you loans at a ridiculously low-interest rate (Here are some handy tips to spot frauds)
- Any company that says it doesn’t care about your credit history has no intention of lending you money. A legitimate lending institution wants to know whether you pay your bills on time and in full. It needs some assurance that you’ll repay what you borrow.
- Search the business’ website for an address where it legally does business. Lenders and loan brokers must be registered in the country where they conduct business.
- One should never pay to get a personal loan. Many scammers ask borrowers to provide a prepaid debit card for insurance, collateral or fees.
- Make sure a padlock icon appears somewhere on the web pages where you’re asked to type in personal information. Don’t override any warning saying a site’s security certificate has expired and pay attention to the URLs you click on.
- When you find a lender online, go through the site to determine its physical location. Do they provide a street address? However it may be a fake! If you don’t find any indication of their location, you should avoid the lender.
- Some websites appear to offer different types of personal loans but aren’t actually lenders, but sell your personal information to other loan companies. Many “microlenders” merely collect your personal and financial information for other companies.
- Don’t fall for the “Act Now” urgency plea. Many criminals often give you a deadline and say their offer won’t exist tomorrow.
[Article by David Wiles]