Archiving – it doesn’t exactly sound like a fun weekend activity, does it?
But unfortunately our mailboxes can’t always deal with too many┬Āe-mails, especially those with large attachments, we receive regularly. Unless you clean up your mailbox and delete e-mails frequently, you’ll run out of mailbox space sooner than you think. This is where archiving comes in handy.
In this article we will show you how easy it is to create and maintain archives on your computer.
- HOW TO CREATE YOUR ARCHIVE FILE
Open MS Outlook
- Select the Home tab
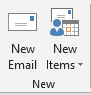
- Use the dropdown menu next to New Items
- Click on More Items
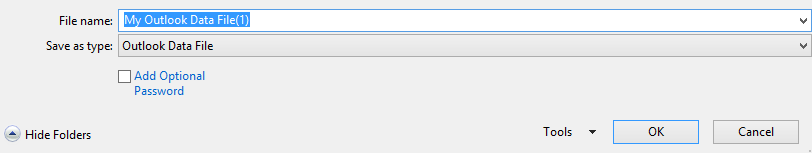
- Select Outlook data file
This will create the file for your new archive.
Important:
- Please name it properly as to prevent confusion when creating new archives later on.
- Please do not put a password on the archive file as this causes confusion and mail loss at the end of the day when you get a new computer or if the case may be that data recovery must be done.
This also must be under ŌĆ£My Documents\Outlook FilesŌĆØ.
When clicking on OK┬Āyou will return to your Outlook Home screen.
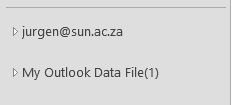
As shown below (when the mailbox is collapsed) you will be able to see your new Outlook archive.
2. NOW FOR THE ARCHIVING
Click on File in the left top corner
Under Info you will find Cleanup Tools
When clicking on the button you will find Archive as the third option.
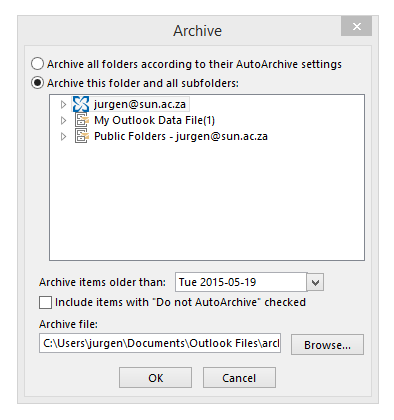
The next window you will be presented with is seen below.
The most important thing you need to do now is check that the correct archive file will be used for archiving.
To check┬Āthis you need to click on the browse button and make sure it is pointing to the correct file in ŌĆ£My Documents\Outlook FilesŌĆØ.
Secondly:
- Choose a date ŌĆō all e-mails before the input date will be archived to your folder. This may take a while if you have not archived before.
Thirdly:
- Select your mailbox (not only parts of it, but the Collapsed view as seen in the screenshot) and then click on OK.
You have now successfully started your first archive!┬Ā Feel free to archive instead of delete as keeping your records is quite important.
TIPS:
- VERY IMPORTANT ŌĆō┬Āno password on the archive file.
- Keep archives small, for example ŌĆō year by year. This is to prevent them from getting too big and slowing down your machine.
- With this way of archiving your folder structure stays the same thus making it easier to actually go back and find the files you are looking for from previous years.
For ┬Āmore information on various Outlook functions, please have a look at our self help site.


 At Stellenbosch University colleagues have been using it successfully in the biological, mathematical and physical sciences, and also in economic and management sciences for both teaching and research.┬Ā It is therefore really worthwhile exploring whether it is suitable for your academic work too.
At Stellenbosch University colleagues have been using it successfully in the biological, mathematical and physical sciences, and also in economic and management sciences for both teaching and research.┬Ā It is therefore really worthwhile exploring whether it is suitable for your academic work too.