January 2025
Dear Students
This message informs you of a new-look SUNLearn for 2025 and what to expect.
Faculty-based SUNLearn instances
Over the last few months of 2024, SUNLearn, as you came to know it, was migrated to a new faculty-based learning platform in preparation for the 2025 academic year. You will find your 2025 modules for which you are registered according to the faculties that present them at the following addresses:
|
EMSLearn (EMS & MillSci) |
|
|
FMHSLearn (FMHS) |
|
|
SocSciLearn: (Edu, FASS, Law, Theol) |
|
|
STEMLearn: (Agri-Sci, Eng & Sci) |
Please note that starting in 2025, going to SUNLearn (https://learn.sun.ac.za), as usual, will also give you access to all the other faculty-based instances.
The new-look SUNLearn learning environment
To guide you into what to expect from and how to work in the new SUNLearn multi-faculty environment, we want to draw your attention to the following:
- The new faculty-based instances have a unified view (i.e., all instances can be accessed from any of the instances).
- You will have to use MFA (Multi-factor authentication) to log in.
- SUNLearn will have a new look theme. To introduce you to the new-look environment, you are invited to engage with:
-
- An infographic that highlights all the essential information on the new environment.
- Overview video that shows you step-by-step how to access and start to use the new platform (Tip: view the video in full-screen mode).
If you have any questions or want to tell us about a problem, don’t hesitate to get in touch with us via:
- Helpdesk: https://learnhelp.sun.ac.za
- Email: learn@sun.ac.za
- Phone: 021 808 2222
Warm regards,
The Integrated Learning Technologies Team
November 2024

Dear Staff and Students
We are happy to report that, thanks to the efforts of our IT and Centre for Learning Technologies colleagues, the plan for a stable SUNLearn platform is well underway. The process of migrating all academic modules from SUNLearn to the four new faculty-based SUNLearn instances with their unified view is ongoing. All modules should be migrated to their new homes by the beginning of December 2024. This will allow staff to organise their modules on the new platform for a successful start to the new year. We thank all academic staff working on the migration on top of the daily demands of their jobs.
We acknowledge the frustration SUNLearn caused during the first half of 2024 and want to thank everyone for their understanding and patience during trying times. The migration of FMHSLearn in July-August showed that the plan for creating different instances is working. Overall, SUNLearn and FMHSLearn worked well during the third and fourth terms. This gives us confidence that the new faculty-based instances of SUNLearn will provide a robust and reliable system for 2025 and beyond.
In preparation for the migration, we asked all staff to do extensive housekeeping on their modules, cleaning up and streamlining the content. This made a difference, and we want to thank all staff who supported the migration process in this way. We have also asked staff to start thinking about reviewing their SUNLearn modules to create more student- and system-friendly learning experiences. In the coming weeks we will be communicating further guidance to navigate the new SUNLearn instances. We thank all staff who indicated they want to start with a fresh module look for next year. We hope more academics will also consider using the template that we provided to organise their modules.
We believe the SUNLearn platform offers an opportunity to start a new phase in the use of our learning management system for effective teaching and learning. The Centre for Learning Technologies in the Learning and Teaching Enhancement Division is committed to providing support on the optimal utilisation of the LMS. We will communicate further in this regard next week.
With many thanks to all.
Prof Lis Lange
Acting Senior Director DLTE
&
Dr Antoinette van der Merwe
Chief Director IT
September 2024
Dear Deans and Vice-Deans
As I communicated on Thursday, 5 September 2024, IT rolled out Azure Multi-Factor Authentication (MFA) for SUNLearn and FMHSLearn during the IT Maintenance Weekend (6 – 9 September 2024). The message also indicated that the Computer User Areas would be excluded from the roll out not to affect assessments.
Early this week, it became clear that the rollout of MFA cannot be done as expected. Antoinette, her team and the Centre for Learning Technologies staff met to discuss this and we concluded that we need to roll back to the original configuration. We would like to engage further with you regarding MFA, specifically for assessments on SUNLearn and FMHSLearn in Computer User Areas. As soon as possible, we will call a meeting with the Vice-Deans: Teaching and Learning to discuss this and the implications it is likely to have on changes to the yearbook.
Kind regards
Lis and Antoinette
(An update from Prof Lis Lange, Acting Senior Director: Division for Learning and Teaching Enhancement)
Please note that SUNLearn and FMHSLearn may be unavailable from Friday, 6 September, at 21:00 to Monday, 9 September, at 07:00.
During the upcoming IT Maintenance Weekend from 6 to 9 September 2024, we will implement Azure Multi-Factor Authentication (MFA) on our Learning Management Systems (LMS). This update is crucial to ensure accurate monitoring of user access through the Azure administration portal, as well as maintaining the security and integrity of both SUNLearn and FMHSLearn.
After this upgrade, all users will be required to use the Microsoft Authenticator App as a second layer of security when logging on to SUNLearn and FMHSLearn. NB: MFA will not be implemented in Computer User Areas and it will therefore not have an impact on assessments conducted in these areas at this stage.
Many thanks for your ongoing cooperation.
JUNE 2024

SUNLearn has experienced disruptions and instability over the last year. The intensification of these problems at the start of the 2024 academic year required that IT and the Division for Teaching and Learning Enhancement (LTE) implement an emergency plan to optimise the performance of SUNLearn. This was done by distributing the storage and load across Faculty-specific LMS platforms. The first of these was FMHSLearn. The Medicine and Health Sciences Faculty has successfully used FMHSLearn since March 2024. This was followed by the creation of EMSLearn (EMS and Military Faculties), STEMLearn (Science, AgriScience and Engineering Faculties), and SocSciLearn (Arts, Education, Law and Theology Faculties).
Where are we now?
Further migration to additional LMS environments was halted in May 2024 to ensure stability and continuity during the first semester of the academic year. The team supporting the FMHSLearn, SUNOnline, SUNLearn and Student Feedback platforms focused on ensuring that there was limited disruption to campus activities. We are very grateful for the cooperation of academics in “cleaning up” the system by reducing module sizes and duplications. This process is still underway within faculties.
What is the plan of action for Semester 2 this year?
- Archiving and LMS preparation: IT will utilise the remainder of the academic year to archive and remove all content on the SUNLearn database, up to and including 2022 content. The team will continue to prepare and test the LMS environments as indicated above to test and demonstrate the so-called “unified view” where students could have modules over LMS environments.
- Engagement with Academic Affairs Council: We will also engage with the Academic Affairs Council to assist us in preparing orientation material for students. After the December 2024 graduation, modules will be further migrated to EMSLearn, SocSciLearn and STEMLearn. This is in preparation for the 2025 academic year, at which time each of the LMS platforms will be live and available to staff and students as their new online Teaching-learning-assessment platforms.
- Support from the Division for Learning and Teaching Enhancement and Centre for Learning Technologies: The DLTE, through the Centre for Learning Technologies (CLT) will continue to support staff and students via the SUNLearn support desk, including monitoring and support for assessments hosted on SUNLearn where needed. CLT will draft and circulate guidelines for instructional design to faculties for dissemination to lecturers. This will aid in reducing the size of large modules, while retaining the educational value of the blended learning approach followed at SU.
This plan of action requires that there is a close monitoring of SUNLearn during assessment period. For the IT/CLT team to do this effectively, we need faculties to ensure that all their assessments are captured on the Assessment calendar. All high-stakes assessment dates and times (especially those happening in CUAs, and those that use special plugins like Coderunner) need to be captured on the Assessment calendar by sending a meeting request to learn@sun.ac.za.
Further constructive feedback from students and staff remains important so that we can improve the learning environment. We are committed to reacting with urgency to resolve issues and provide a reliable learning environment.
Many thanks for your ongoing cooperation.




 As we enter into the new academic year, there are a lot of expectations, concerns, excitement and opportunities that await. Thanks to the pandemic, SUNLearn has become the central platform for Learning, Teaching and Assessment, exactly as it was originally envisaged.
As we enter into the new academic year, there are a lot of expectations, concerns, excitement and opportunities that await. Thanks to the pandemic, SUNLearn has become the central platform for Learning, Teaching and Assessment, exactly as it was originally envisaged.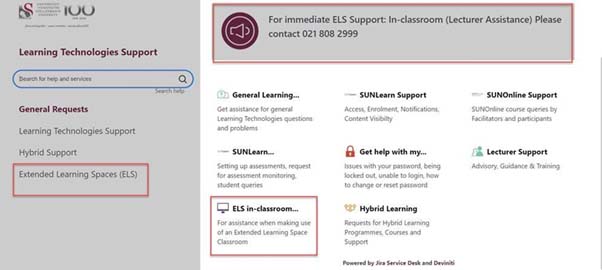


 A new multi-language management feature was recently implemented on the REDCap platform for researchers.
A new multi-language management feature was recently implemented on the REDCap platform for researchers.