Students
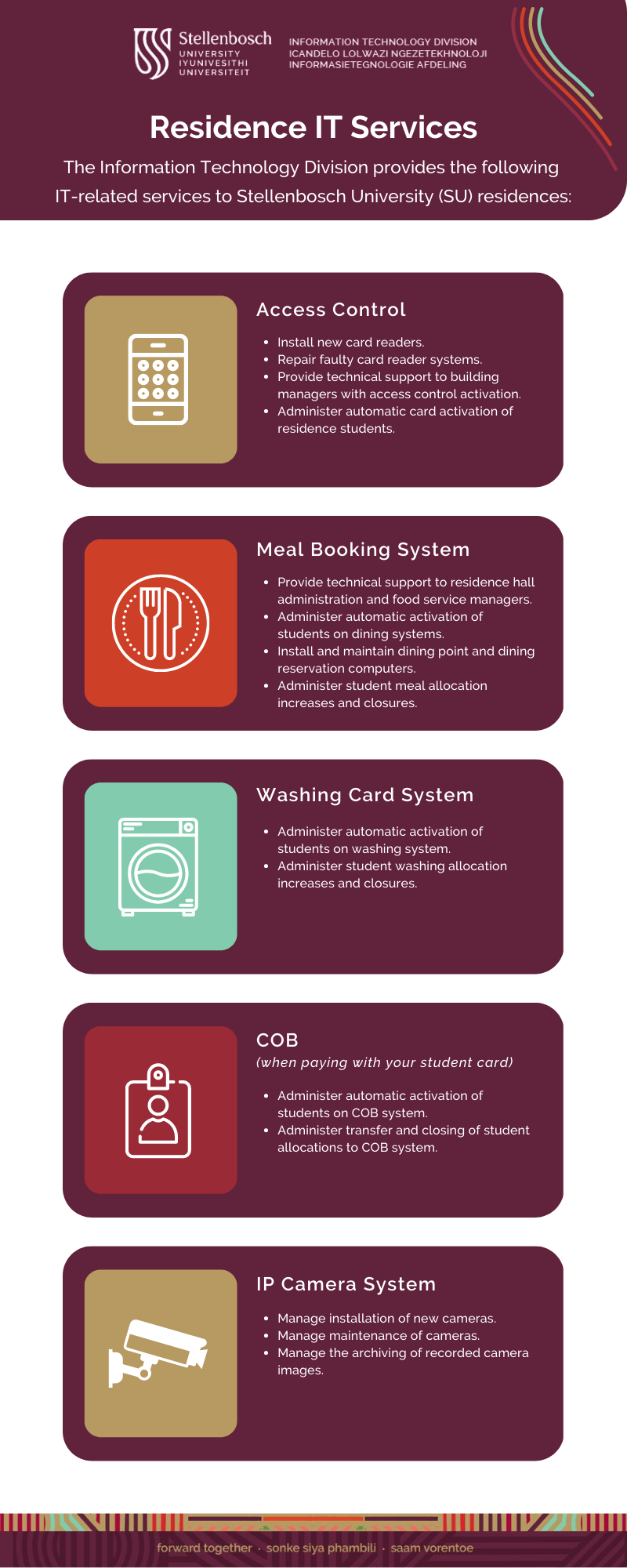
Residence IT Services
Wednesday, February 22nd, 2023Getting to know SUNLearn
Wednesday, February 22nd, 2023The first few weeks of being a first-year student at Stellenbosch University (SU) can be overwhelming. Getting to know how SUNLearn, the university’s electronic learning management system works – and familiarising yourself with the terminology that goes with it, can be daunting. We want to encourage you to stay calm and to reassure you that help and support are at hand!
SUNLearn has been in operation since 2014 and, through the years, it has been improved to make it increasingly accessible and user friendly for both staff and students to navigate. On top of that, the SUNLearn learning technology support team is in place to help students with all their queries.
In this article, we asked the people responsible for SUNLearn to take students on a welcome journey to understand the system so that they are able to use it and are better prepared for their academic year. We picked the brains of Dr Lianne Keiller – Manager: Learning Technology Systems and Morris Samuels – E-Learning Technical Officer at SU to answer some of the most frequently asked questions related to onboarding.
According to Dr Keiller and Mr Samuels, an important thing students need to note is that only students who have completed their registration process will have access to SUNLearn.
“We have found that sometimes students forget to complete their registrations at the beginning of the year; and then they start classes and realise they cannot get into SUNLearn and cannot access their content or their modules. So you have to be registered first before you will have access to SUNLEearn,” Dr Keiller said.
Below are some of the more common questions asked by first-year students at Stellenbosch University.
What, in a nutshell, is SUNLearn?
LIANNE KEILLER: SUNLearn is the name of the learning management system we use at Stellenbosch University. A learning management system (LMS) is an online space where a student can manage their learning and their interactions with their lecturers and with each other.
SUNLearn is where lecturers will upload all the content for a lecture, or they might even conduct a lecture on SUNLearn if they are doing it virtually. SUNLearn also allows the creation of spaces where students can talk to each other on discussion boards and can send private messages within the LMS. If a student is registered for a module, there is a SUNLearn space for it and the lecturer is the one who decides how to put things onto the module.
A number of lecturers make use of the SUNLearn system for tests or exams for the students to do online.
From an IT perspective, the SUNLearn system is supported by a small team which is dedicated to making sure that the student and lecturers’ experiences are as simple and easy as possible.
What is your message to students who are feeling overwhelmed at the thought of using the SUNLearn system?
MORRIS SAMUELS: Students should not be overwhelmed. Using SUNLearn is as easy as accessing any web page on the internet.
How do students access SUNLearn?
MORRIS SAMUELS: SUNLearn can be accessed via any web browser on a computer, mobile phone or tablet. In the address bar of the browser, type in learn.sun.ac.za and press ‘ENTER’. On the SUNLearn homepage, click on the ‘Log in’ link that is located in the top righthand corner to navigate to the ‘Single Sign-on login page where you will need to enter your username (student number) and the password set for it.
Alternatively, you can also access SUNLearn via the MY.SUN entry page by typing in my.sun.ac.za in the address bar of the browser. When the page opens you will be prompted to enter your network login credentials. Once you are logged in, locate the shortcut link for SUNLearn and click on it to open the SUNLearn Dashboard page where you should see all your registered modules. Most students access SUNLearn and other university systems via the MY.SUN entry page.
What should students do if they need support in using SUNLearn, or if they encounter problems?
MORRIS SAMUELS: The important thing for students to understand is that the IT help desk is there for general IT information and support, but, in terms of SUNLearn, there is a dedicated support team which falls under my leadership.
The SUNLearn learning technology support team deals with any queries related to SUNLearn. For example, if a student finds that a registered module is not listed on their course overview page or if, for some reason, they cannot access a module on SUNLearn, then the SUNLearn learning technology team is your port of call to report that.
How do students access the SUNLearn learning technology team to get help with a problem?
MORRIS SAMUELS: The correct way to get support is to log a ticket on the SUNLearn service desk. This should by using the portal at www.learnhelp.sun.ac.za. Alternatively, you can call the support desk on 021 808 2222.
If, for some reason, students struggle to log a ticket via the learnhelp.sun.ac.za portal, they can also send an email to learn@sun.ac.za to automatically log a ticket on our service desk.
What do students do if they’ve logged into SUNLearn but there is no content in the module or there are no notes or any activities in the module?
MORRIS SAMUELS: Lecturers are responsible for uploading the content and for the visibility of content in their modules on SUNLearn. Students with this problem should first contact the lecturer directly about uploading notes if there is nothing there and they expected to see something.
What does a student do if they are unable to log into SUNLearn; in other words, they are registered but unable to log in to SUNLearn.
MORRIS SAMUELS: If this happens, there may be a problem with your password or it needs to be updated on www.sun.ac.za/password.
On which of my devices can I access SUNLearn?
MORRIS SAMUELS: You can access SUNLearn on any device – your mobile device, your laptop or your tablet. There is also an app for the learning management system you can download from the Apple app store or Google Play store. SUNLearn is zero-rated. This means that it doesn’t use any of your mobile data to access the Moodle app (the system SUNLearn is built on) or the LMS via your mobile browser.
In a final word of advice to students, Mr Samuels had this to say: “First-year students, don’t call your mother, call us! We’ve had a few phone calls from mothers or fathers on behalf of students, who are sitting in class, struggling with SUNLearn. Don’t ask your parents to call us – rather call us yourselves. Our support services are easy to use and we are here to help.”
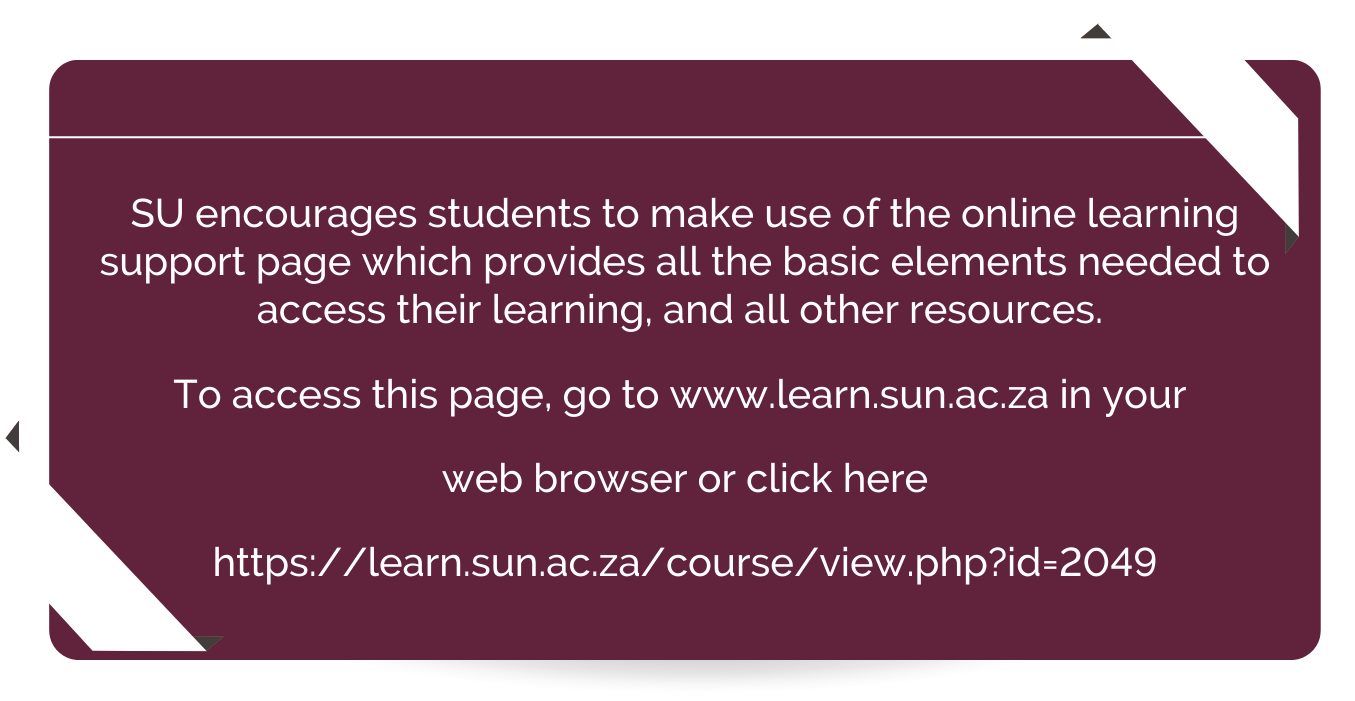
The online learning support page contains the full range of tips on logging in, loading print credits and other tips.
Also on the technology onboarding page, students can find information on how to connect to wifi on campus. Here is the direct link to that information: https://tech.sun.ac.za/faq/#step-11-apps-to-download. It is located under the frequently asked questions (FAQ) section on that page.
Internet down Sunday morning
Friday, February 25th, 2022 Due to critical maintenance by TENET, our internet service provider, internet services will be down on Sunday, 27 February from 00:00 am to 03:00 am.
Due to critical maintenance by TENET, our internet service provider, internet services will be down on Sunday, 27 February from 00:00 am to 03:00 am.
During these three hours there will be no access to the internet. We apologise for the inconvenience. Any enquiries can be logged on servicedesk.sun.ac.za.
SUNLearn latest update
Wednesday, February 16th, 2022
LATEST UPDATE 22/02 16:47
In an effort to ensure that all students have access to their registered modules, a decision was taken to urgently do manual uploading of all registered students into their respective modules.
For this to be executed as speedily as possible, we need to restrict access for all users between 19:00 and 22:00 tonight (Tuesday, 22 February)
We sincerely apologise for the inconvenience.
——————————————————————————————————————————————————————————–
UPDATE 16/02
We have been experiencing severe problems with SUNLearn since Monday, 14 February. This includes database access issues, as well as incomplete or erroneous student module registration information.
This is treated as a high priority incident. However, to resolve these problems we need to switch off the feed of student module information from the student system and will also stop manual module registrations on SUNLearn until tomorrow (17 February 2022) afternoon at 14h00.
This will allow the technical team to analyse the problem in-depth without new registrations putting additional strain on the system.
We apologise for the inconvenience. We are aware of the impact the situation is having on students and staff and are doing our utmost to ensure that the system is entirely functional as soon as possible
Connect to WiFi on campus
Thursday, January 27th, 2022
The Wi-Fi network used to connect to the internet access is called eduRoam. Here we explain what it is, how to register and why it is necessary.
What is eduRoam?
eduRoam (education roaming) is the secure, world-wide roaming access service developed for the international research and education community. eduRoam allows students, researchers and staff from participating institutions to obtain internet connectivity across campus and when visiting other participating institutions by simply opening their laptop.
To connect to eduRoam and start using Wi-Fi on campus follow these steps.

