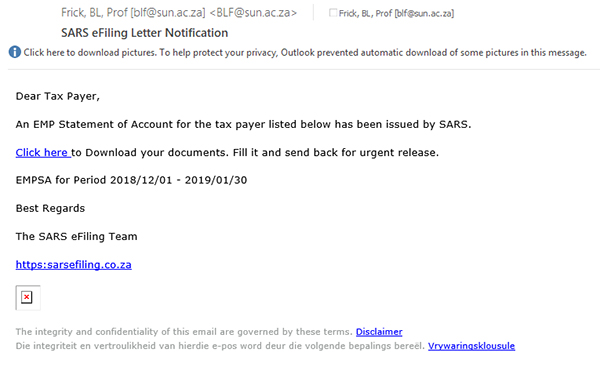
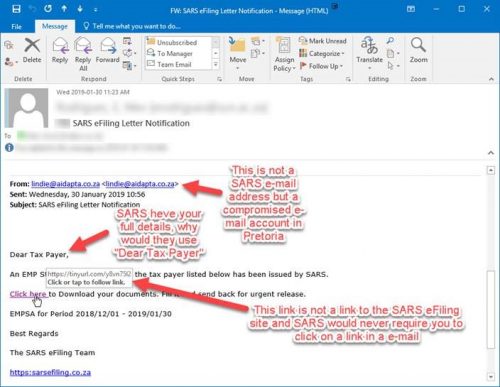
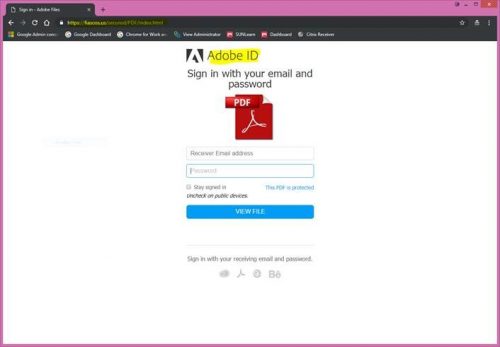
SANReN has implemented the latest version of Filesender, a web-based application that allows authenticated users to securely and easily send web-based large files to other users.Â
Below are the guidelines for accessing the service and what values it adds to your day to day operations.
What problem does the service solve?
You need to send a file larger than a couple of megabytes to someone and the e-mail comes back: “attachment too big” or “mailbox too full”, that’s where FileSender comes in handy.
How do I use the service?
Upon logging in, you are presented with a user-friendly interface. You can set the file to be available for download for a certain period so that it automatically gets removed when the file reaches its expiry date. You have an option to drag and drop your file when uploading it to the application. You also have an option to get a link to the file after uploading it or send it to a recipient as an e-mail.
The service is integrated with the South African Identity Federation (https://safire.ac.za/), which provides a pool of institutions you can authenticate from to use the service. If your institution is not registered on SAFIRE as yet, you can log in with a social media account if you are from an eligible institution.
Where do I access the service?
You can access the service on https://filesender.sanren.ac.za
Drop us an e-mail on sysadmin@sanren.ac.za for any queries regarding the service.