In the past, the IT Service Desk was your first stop when you forgot your password (we know, it happens to us too!) or had to change your password. Unfortunately, due to various security risks, as well as the very strict new data protection acts, the Service Desk is no longer allowed to change or reset your password for you. (You can read more about the university’s own Data Privacy Regulation here)
We would like to encourage staff and students to use the Password Selfhelp website in future. We realise that this might be inconvenient, but for your and our own protection, we will have to follow this procedure.
The Password Selfhelp website (www.sun.ac.za/password) offers two options:
- Change Password for users who know what their password is and want to change it.
- Reset Password for users who forgot their password.
To use the online Password Selfhelp, your cellphone number or an alternative email address has to be on the HR records, otherwise, you will not be able to change your password. You can update this information by logging onto SUN-e-HR though the staff portal, http://my.sun.ac.za or contacting your department’s HR contact person.
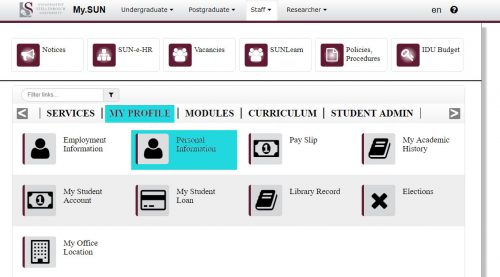
Select the My Profile link – Personal Information
Log on to SUN-e-HR.
Select Basic Details – Update, Other, Personal Email Address
or
Select Phone Numbers – Update
During the password change process a PIN code, consisting of 8 numbers, will be SMSed or emailed to the user (depending on which option he/she selected) Please use this PIN to change your password on the self help website. As soon as the password has been changed, the user will be notified by means of SMS or email.
If you have not requested a password change, please notify the IT Service Desk immediately at 808 4367.


 Personal information has value—to the individual, to researchers, to the University, and to malicious attackers. The first step towards appropriately securing personal information involves building a proper understanding of the value of the personal information you use for institutional processes and research projects.
Personal information has value—to the individual, to researchers, to the University, and to malicious attackers. The first step towards appropriately securing personal information involves building a proper understanding of the value of the personal information you use for institutional processes and research projects.
