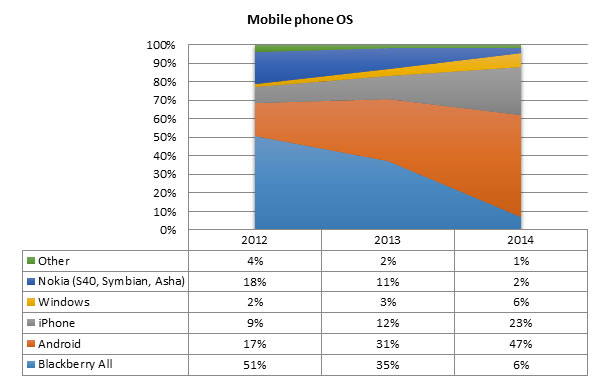
Android and Apple mobile phones look likely to dominate share amongst students within a year while Blackberryâs share is dwindling rapidly. The picture has changed significantly since 2012:
This is just one example of the results of a recent mobile technology survey conducted by the Information Technology division to track trends in students’ mobile devices. The purpose of these surveys (the first was conducted in September 2012) are to identify trends so that relevant university mobile services and strategies can be implemented in future. Understanding the mix of devices that students possess and how rapidly the picture is changing, is crucial for informed planning and decision-making.
Another unexpected trend is the slow penetration of tablets on campus. Since the vast majority of students have daily access to a laptop, ultrabook or notebook, the tablet seems to be an optional âthirdâ device, which 47% of students can’t afford and 25% prefer not to use. Only 28% of respondents have a tablet, almost half of which are Apple iPads, closely followed by Android tablets. Students indicate that the take-up is likely to increase but accelerate slowly.
Unfortunately awareness of the national Student Technology Programme, which provides students with the opportunity to purchase heavily discounted tablets, laptops and notebooks, is also still lacking.
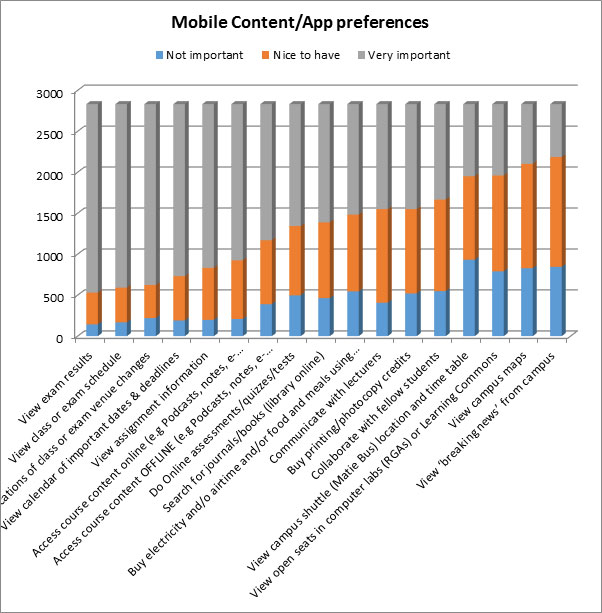
On the positive side students consistently rate mobile services and content related to learning and academic events and schedules as the most important. It is possible that as more learning content, including e-textbooks, becomes available via mobile devices, for offline consumption as well, that the penetration of tablets may accelerate.
More surveys will be conducted in the foreseeable future to discern trends and changes over time and students are encouraged to participate.
One lucky respondent, BComm student, Pierre-Etienne Rossouw, was the winner of an Incredible Connection gift voucher to the value of R1500.
 2832 students out of 32266 invitees responded.
2832 students out of 32266 invitees responded.
Â
[PHOTO: Ralph Pina (director of development) with winner Pierre-Etienne Rossouw]


 A task team (Johann Kistner, drs Antoinette van der Merwe & JP Bosman and ms Marinda van Rooyen) facilitated the evaluation, including consulations with academic, administrative and support services staff. The success of systems, as well as the scale on which they were used by other universities, were also looked at. In the end a decision was made based on a set of predefined, weighed criteria. The following was taken into account:
A task team (Johann Kistner, drs Antoinette van der Merwe & JP Bosman and ms Marinda van Rooyen) facilitated the evaluation, including consulations with academic, administrative and support services staff. The success of systems, as well as the scale on which they were used by other universities, were also looked at. In the end a decision was made based on a set of predefined, weighed criteria. The following was taken into account:
 The abbreviation sounds like a reference to a Central African country and although DRM has to do with management, it’s about managing something less tangible and with less defined borders.
The abbreviation sounds like a reference to a Central African country and although DRM has to do with management, it’s about managing something less tangible and with less defined borders. Until now free internet access to the US Library Services’ subscription based electronic resources were managed by a setting in users’ browsers.
Until now free internet access to the US Library Services’ subscription based electronic resources were managed by a setting in users’ browsers.