In a previous article written for the Cyber-Security Awareness Month I talked about “spear-phishing“. Spear-phishing attacks target the university specifically instead of just sending out random “shot in the dark” emails that someone will hopefully fall for. Spear-phishing has been notoriously successful because scammers focus on university employees and student internet activity and send requests that look like the real thing, claiming to be from entities within the environment that you actually deal with.
In the past couple of years we have had a couple of large-scale spear-phishing attacks that resulted in a number of student and personnel accounts being compromised and in several instances some of the victims suffered financial loss.
In April 2017, a number of personnel got an e-mail from “Stellenbosch Payroll” with the subject of “NOTIFICATION: Your 13.69% Salary Increase.”
The e-mail said that there were two attached documents that needed to be downloaded that would detail the salary increase. The mail was sent at a time when salary increases and performance bonuses were being granted.
The bait was the mention of a 13.69% salary increase which would certainly attract the attention of anybody, and many people would overlook the lack of a personal salutation, and the occasional grammar and spelling mistakes, lulled into a false sense of security because it seemed to come from the university, had all the university logos, was speaking about the annual salary increases and offered a sizable salary increase!
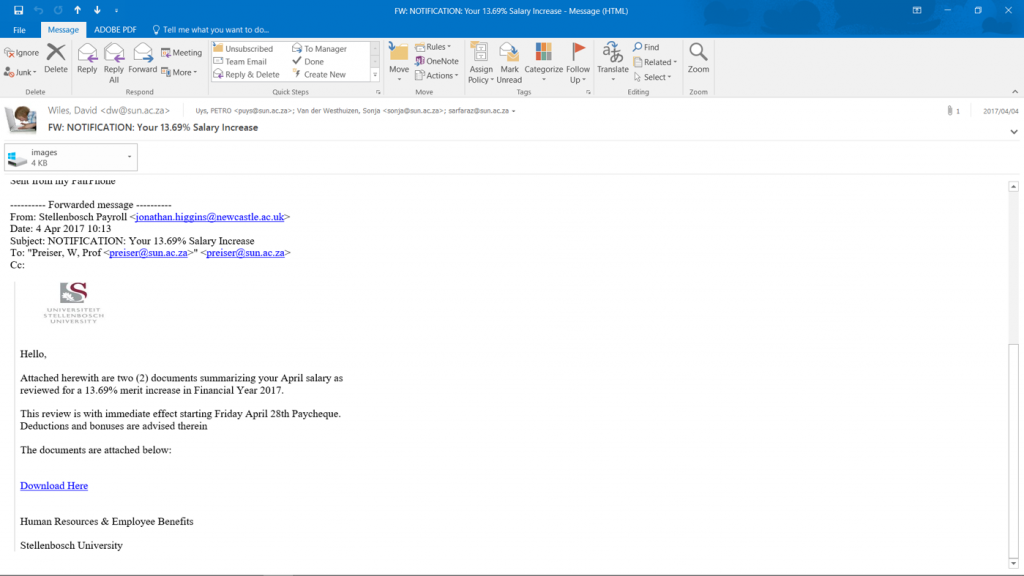
Once tricked by this initial bait, the intended victims – university personnel – would click on the links and would be taken to a forged website that looked identical to the real login page of the university Human Resources division.
Here the victims entered their usernames and passwords in order to see the documents for their salary increase. The password did not work, but the only thing that had happened was that the scammers that had set up this server, captured the user names and passwords and thus gained access to the REAL HR website using the stolen details. The forged website had fulfilled its task of stealing the victim’s usernames and passwords.
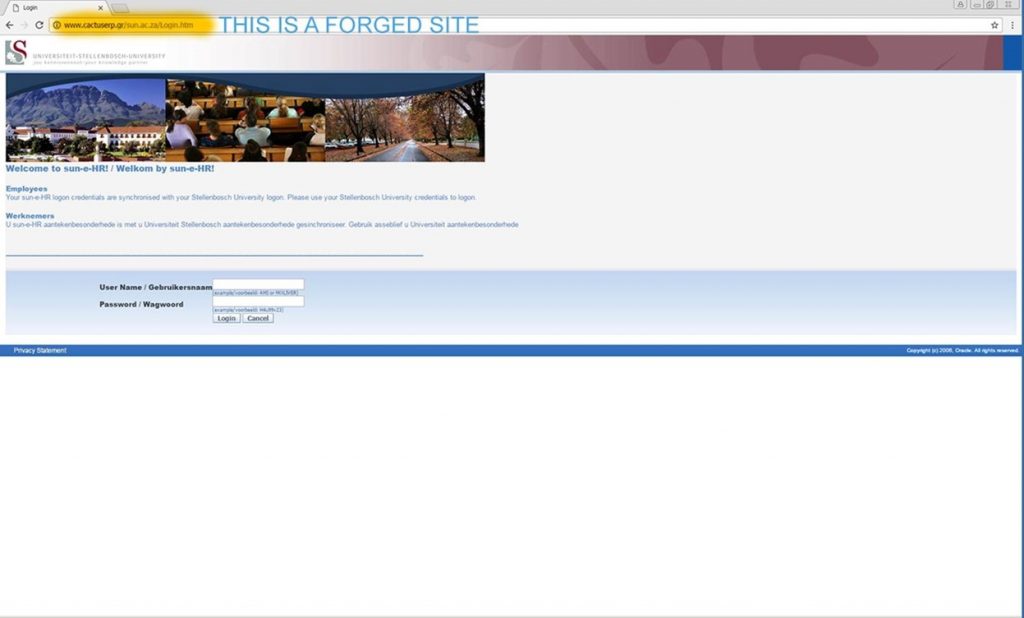
Having then gained access to the victim’s account on the HR website, the scammers then changed the victim’s banking account details to their own, so that they could get the victim’s salary paid into their own account. Furthermore they would have also recorded the original bank account details and targeted them for further exploitation. The warning signs were there all along. The forged website address was not in the university domain but very few people would spot that detail.
A second spear-phishing attack occurred a year later in May 2018:
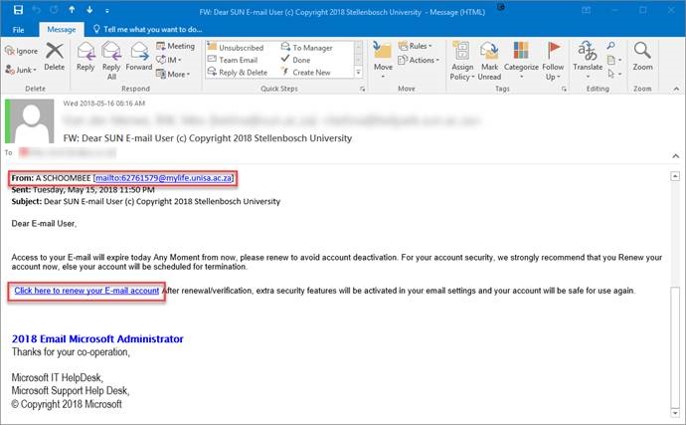
It started with an e-mail from a UNISA email account. (Already been compromised and was being controlled by the scammers) The mail warned the intended victims that their email account was due to be deactivated and that they should click on a link to renew their account. The Subject said “Dear SUN E-mail User (c) Copyright 2018 Stellenbosch University” which many victims saw as legitimate. and the signature was from the “2018 Email Microsoft Administrator”.
A note here about how cleverly the spear-phishing scammers researched their intended target. The email used words and other details like SUN, Stellenbosch University & IT HelpDesk that would convince many people that the mail was legitimate.
The link took the victims to another forged website. This time it was a perfect copy of the university’s own “Single Sign-On” page that students and personnel used to access important services within the university, like e-Learning and the personnel portal.
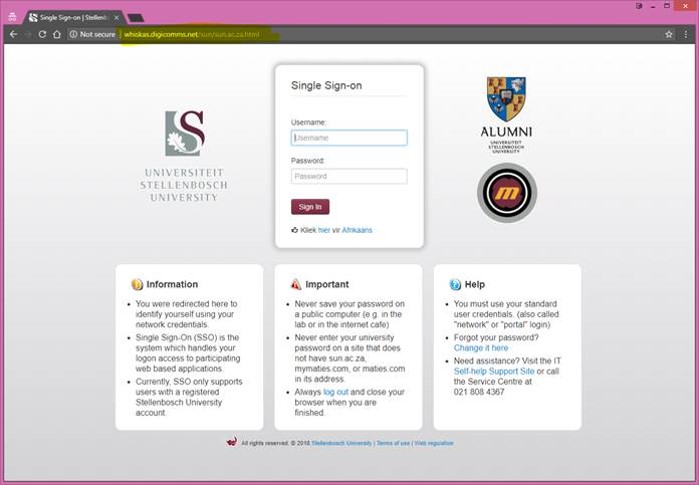
The website address was also not in the university domain, but all the rest of the details looked right, even down to the branding and the inclusion of a link “Kliek hier vir Afrikaans“.
Once the victims had entered their user names and passwords on the forged site, the scammers had then gained control over the users accounts and then could send out further e-mail messages from within the university to catch more victims who would see that the sender came from within the university, and would think that the mail and the website was real!
What could we have done to spot and prevent these attacks?
Unfortunately, in my opinion, there is a general institutional attitude that it is Information Technology’s job to prevent and protect its users against such attacks. This is not true. It is not just their job! Everybody who is a user of an institutional network, or a private user, for that matter, has a common responsibility to be aware of the dangers that we face in cyberspace, to sensitize themselves to the warning signs and to become “informed” users, and to help Information Technology by watching out for suspicious e-mails to report them and not using weak or easily-guessable passwords.
For instance here are some common-sense checks that every user can learn:
- Don’t trust display names. These can be anything a scammer wants them to be.
- Check for fake email domains. These will often be slightly different versions of the real thing.
- Look at the university logo and other images. Are they commonly available on the internet?
- Review links carefully by hovering over the link text (without clicking). A link that is different from the one in the link text is a sign that it is a malicious link.
- Look for the sun.ac.za domain name in the link. If the domain is different it is probably a malicious link.
- Look out for bad spelling and grammar, as this can be a tell-tale sign that it’s not a legitimate message.
- Spear phishing emails and messages are highly focused and targeted. The criminal will spend a lot of time making e-mails and website look like the real site.
- If you have suspicions about an email or other message, never visit the site. Always verify it first, by checking with Information Technology. They will quickly be able to tell you if it is legitimate or not.
- User strong passwords and never use the same password (especially if it is a weak one) on multiple sites.
In the final article for the Cyber-Security Awareness Month, I will share a few thoughts on how to increase your awareness about cyber-security and give a few tips and suggestions about what the university could do to fight and prevent these attacks!
Keep safe out there,
David Wiles









