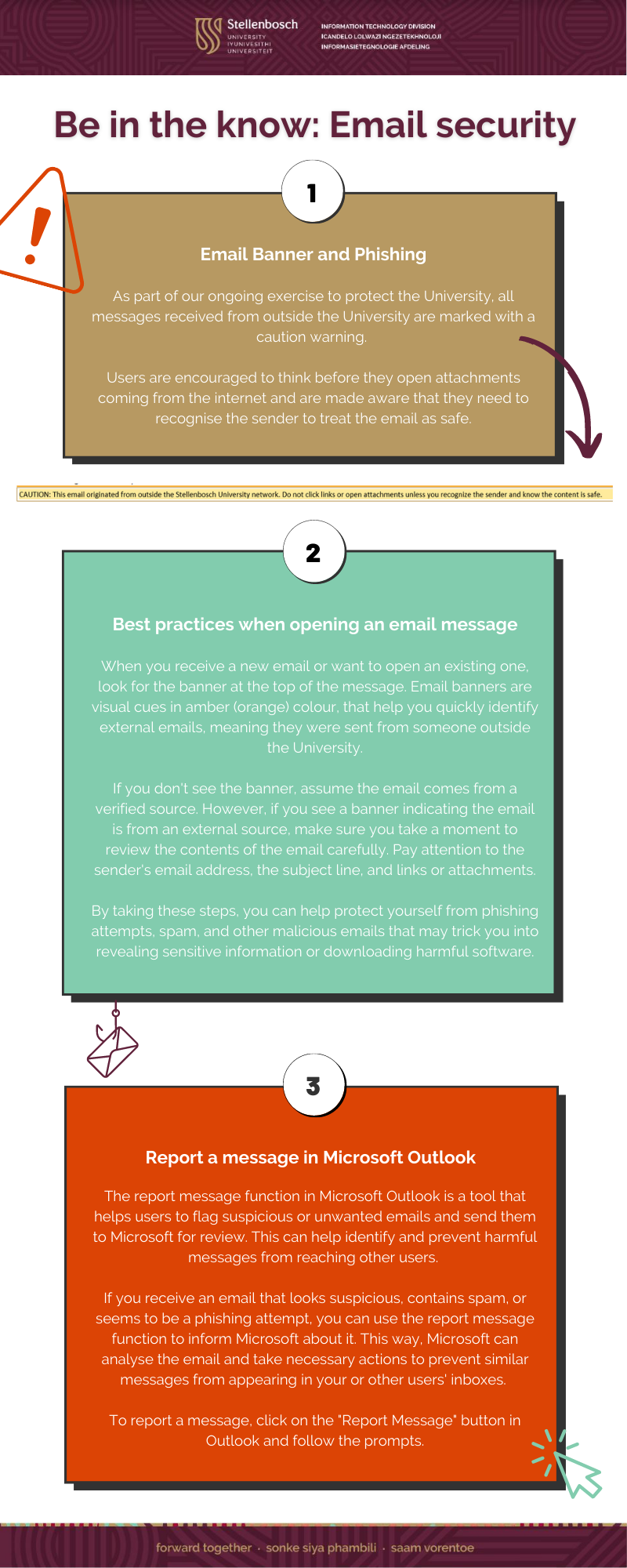
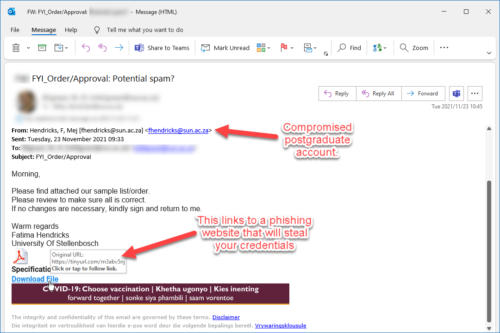
[:en]
We can’t warn you against every phishing e-mail– there’s a new variation every day. You are the only person who can protect yourself from phishing scams and identity theft. The only way to do this is to learn to recognise a harmful e-mail by paying attention and keeping an eye out for a few tell-tale signs.
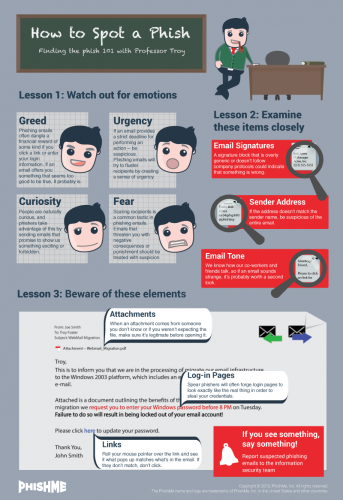 Typical characteristics
Typical characteristics
1. Well-known companies used as bait
These e-mails are sent out to thousands of different e-mail addresses and often the person sending them has no idea who you are. If you have no affiliation with the company the e-mail address is supposedly coming from, it’s fake. For example, if the e-mail is sent by ABSA, but you are a Standard Bank client. Also, see a list of types of companies generally used in phishing e-mails below.
2. Spelling and grammar
Improper spelling and grammar is a dead giveaway. Look for obvious errors.
3. Lack of client information
Phishers use a generic greeting. For example, the e-mail greets you as “ABSA customer” or “Dear user”, etc. If the company was sending you information regarding your faulty account, they would mention your account details or name in the e-mail. A company would go through the trouble to address a client by name and won’t ask you for your information. Banks have your information on their system.
4. Deadlines/Sense of urgency
Phishing e-mails demand an immediate response or stipulate a specific deadline, creating a sense of urgency and prompting you to respond before you’ve looked at the e-mail properly. For example, demanding that you log in and change your account information within 24 hours or your account will be closed.
5. Malicious links
Although many phishing e-mails are getting better at hiding the true URL you are visiting, often these e-mails will show a URL that is unrelated to the company. Move your mouse over the link and look at the display address. Is this the website address of the company who seems to be sending the e-mail? If not, it’s clearly a phishing e-mail.
6. Attachments
Phishing e-mails occasionally include an attachment which contains malware. When opened, it will run and install a small programme on your PC, which hackers use to gain access to your PC and information.
Typical phishing topics
• Account issues, such as accounts or passwords expiring, accounts being hacked, out-of-date accounts, or account information has to be changed.
• Credit cards expiring or being stolen, a duplicate credit card, credit card transactions, etc.
• Confirming orders, requesting that you log in to confirm recent orders or transactions before a delivery can be made.
• Winning a prize or getting something for free. Both Woolworths and Pick ‘n Pay’s have been used in fake campaigns to lure people into providing personal details.
Company names phishers generally use
• Any major bank. ABSA and Standard Bank are both popular choices in South Africa.
• Insurance companies, for example, Outsurance.
• Internet service providers
• Apple or Microsoft claiming your account has been suspended.
• E-mail providers, e.g. Gmail or Yahoo
• SARS. Especially at this time of year. (We’ve had a few of these.)
• DHL or any delivery company claiming they have a package for you.
• Your company’s medical aid, for example, Discovery
• Your company’s IT department
• Casinos and lotteries
• Online dating websites
• Popular websites such as Amazon, Facebook, MySpace, PayPal, eBay, Microsoft, Apple, Hotmail, YouTube, etc.
A few tips to keep you safe
• Never follow links in an e-mail you’re uncertain of. Rather visit the page by typing the address of the company in your browser. For example, instead of clicking on the “ABSA URL” in the e-mail, type http://www.absa.co.za in your web browser and log in at their official website.
• Never send personal information by e-mail. If a company is asking for your personal account information or claiming your account is invalid, visit the website and log in to the account as you normally would. If everything seems in order and there aren’t any urgent notifications from your bank, you should be fine.
• If you are still not sure about the status of your account or are concerned about your personal information, contact the company directly, either through an e-mail address provided on their website, over the phone or visit your local branch.
• Delete the e-mail and don’t click on links or fill in any information.
• If you’ve already divulged your information, immediately change your password or PIN and contact the institution to inform them of the breach.
• To report spam or phishing e-mails send an e-mail to sysadm@sun.ac.za with the subject SPAM with the suspect e-mail attached. IT system administrators will then be able to block the e-mail to protect other users.
[SOURCE: www.computerhope.com]
[:af]
Ons kan jou nie teen elke phishing e-pos waarsku nie – daar is bykans elke dag ʼn nuwe variasie. Die enigste persoon wat jou kan beskerm teen phishing-pogings en identiteitsdiefstal, is jyself. Maar, ʼn goeie begin is om te leer om ʼn gevaarlike e-pos uit te ken deur meer oplettend te wees. Kyk uit vir tipiese kenmerke en jou kans om ʼn slagoffer te wees, sal verminder.
 Tipiese kenmerke
Tipiese kenmerke
1. Bekende maatskappye as lokaas
Phishing e-posse word gelyktydig uitgestuur na duisende e-posse en dikwels weet die persoon wat dit stuur nie eers wie jy is nie. Indien jy geen verbintenis het met die maatskappy waarvandaan die e-pos kom nie, is dit waarskynlik vervals. Byvoorbeeld, as die e-pos deur ABSA gestuur is en jy is ʼn Standard Bank kliënt. Sien ook ons lys van maatskappye wat tipies gebruik word vir phishing onder.
2. Spelling en taalgebruik
Onvanpaste spelling en taalgebruik is gewoonlik ʼn duidelike aanduiding. Kyk uit vir voor-die-hand-liggende spelfoute.
3. Gebrek aan kliënte-inligting
Phishing e-posse se aanhef is altyd generies. Byvoorbeeld, die e-pos spreek jou aan as “ABSA customer” of “Dear user”, ens. Indien die maatskappy jou werklik wou inlig oor jou foutiewe rekening, sou hulle na jou rekening-inligting of naam in die e-pos verwys het. ʼn Maatskappy sou die moeite doen om hulle kliënt aan te spreek op sy naam en sou hom ook nie vra vir sy inligting nie. Hulle het reeds al jou data.
4. Spertye/Dringendheid
Phishing e-posse dring daarop aan dat jy dadelik reageer of gee vir jou ʼn kort spertyd. As gevolg van hierdie dringendheid, word jy onder druk geplaas om te reageer voordat jy behoorlik kans gehad het om die e-pos te bestudeer. By voorbeeld, dit dring aan dat jy binne 24 uur aanteken om jou bankdetails te bevestig of jou rekening word gesluit.
5. Vyandig-gesinde skakels
Deesdae is kuberkriminele al slimmer en steek hulle die werklike URL waarheen skakels gaan beter weg. Maar soms sal jy sien dat die URL wys na ʼn adres wat glad nie verwant is of lyk soos die maatskappy s’n nie. Beweeg jou muis oor die skakel en kyk na die adres wat gewys word. Is dit die maatskappy se regte webwerfadres? Indien nie, is dit ʼn phishing e-pos.
6. Aanhegsels
Phishing e-posse het soms ook aanhegsels wat malware bevat. Indien jy dit oopmaak, installeer dit ʼn klein programmetjie op jou rekenaar waarmee kuberkrakers toegang tot jou rekenaar en inligting verkry.
Tipiese phishing onderwerpe
• Probleme met rekeninge, byvoorbeeld ʼn rekening of wagwoord wat verval, gekraak is of inligting wat skielik verander het.
• Kredietkaarte wat verval, gesteel word, ʼn duplikaat kredietkaart of kredietkaarttranssaksies.
• Bevestiging van bestellings. Byvoorbeeld ʼn versoek om aan te teken en onlangse bestellings of transaksies te bevestig voordat dit afgelewer kan word.
• Kompetisies waar jy ʼn prys gewen het of iets gratis kry. Beide Woolworths en Pick ‘n Pay is al gebruik in phishing e-posse om hul kliënte te lok om persoonlike inligting te gee.
Maatskappye wat gebruik word vir phishing
• Enige bekende bank. ABSA en Standard Bank is beide populêre keuses in Suid-Afrika
• Versekeringsmaatskappye, byvoorbeeld Outsurance.
• Internet diensverskaffers
• Apple of Microsoft (wat beweer dat jou rekening opgeskort is)
• E-pos verskaffers, byvoorbeeld Gmail of Yahoo
• SARS. (Veral dié tyd van die jaar)
• DHL of enige afleweringsmaatskappy wat beweer hulle het ʼn pakkie vir jou.
• Mediese fondse, byvoorbeeld, Discovery.
• Jou maatskappy se IT-afdeling
• Casino’s en loterye
• Aanlyn-afspraak webwerwe
• Gewilde webwerwe soos Facebook, MySpace, PayPal, eBay, Microsoft, Apple, Hotmail, YouTube, ens.
ʼn Paar wenke om jou veilig te hou
• Moenie op ʼn skakel kliek as jy onseker is nie. Gaan eerder na die webwerf deur die maatskappy se webadres in te tik. Byvoorbeeld, tik http://www.absa.co.za in jou webblaaier en teken aan op die amptelike webwerf, in plaas van om te kliek op “ABSA URL” in die e-pos.
• Moet nooit persoonlike inligting per e-pos stuur nie. Indien ʼn maatskappy jou persoonlike inligting vra, gaan direk na hul webwerf en teken aan op jou rekening soos altyd. As daar ʼn probleem is, behoort daar ʼn kennisgewing van jou bank te wees.
• As jy nogsteeds onseker is oor die status van jou rekening of bekommerd is oor jou persoonlike inligting, kontak die maatskappy direk d.m.v. die e-posadres op hul webwerf, telefonies of besoek jou plaaslike tak.
• Vee die e-pos uit, moenie op die skakels kliek nie en moenie inligting invul nie.
•Indien jy reeds jou inligting ingevul het, verander dadelik jou wagwoord of PIN en kontak die instelling om hulle in kennis te stel.
• Om gemorspos of phishing e-pos aan te meld, stuur ʼn e-pos aan sysadm@sun.ac.za met SPAM as onderwerp met die e-pos aangeheg. IT stelseladministrateurs kan dan die e-pos blok en sodoende ook ander personeel daarteen beskerm.
[BRON: www.computerhope.com]
[:]