To ensure that staff and students aren’t exposed to malicious phishing or spam emails our system administrators and security team had to enable a stricter spam filter earlier this year as added protection.
To ensure that staff and students aren’t exposed to malicious phishing or spam emails our system administrators and security team had to enable a stricter spam filter earlier this year as added protection.
A spam filter assigns every message, received and sent, a spam confidence level based on the likelihood that the message is spam. Depending on its level an inbound message may be relayed directly to the user’s Junk Email folder. The filter looks at certain criteria contained in the email it rates, for example too many hyperlinks or a suspicious file attached. Tweaking the filter can be tricky ‚Äď we don’t want you to miss important emails, but at the same time it’s our responsibility to protect you and all our staff from harmful attacks.¬†
For this reason, it’s important that you regularly look in your Junk Email folder in case the spam filter might have relayed it there.¬†
The main purpose of Microsoft Outlook’s Junk Email Filter helps is to reduce unwanted email messages in your Inbox. Junk email, also known as spam, is moved by the filter away to the Junk Email folder. This is done at an institutional level by Microsoft (as mentioned above), but you can also flag or “un”flag messages from a person or company as Junk email.
How to change your spam filter’s preferences.
How to tag an email as junk mail.
How to report spam or junk email to Microsoft. (downloadable PDF-document) 
If you have any questions, please log a request on the ICT Partner Portal.


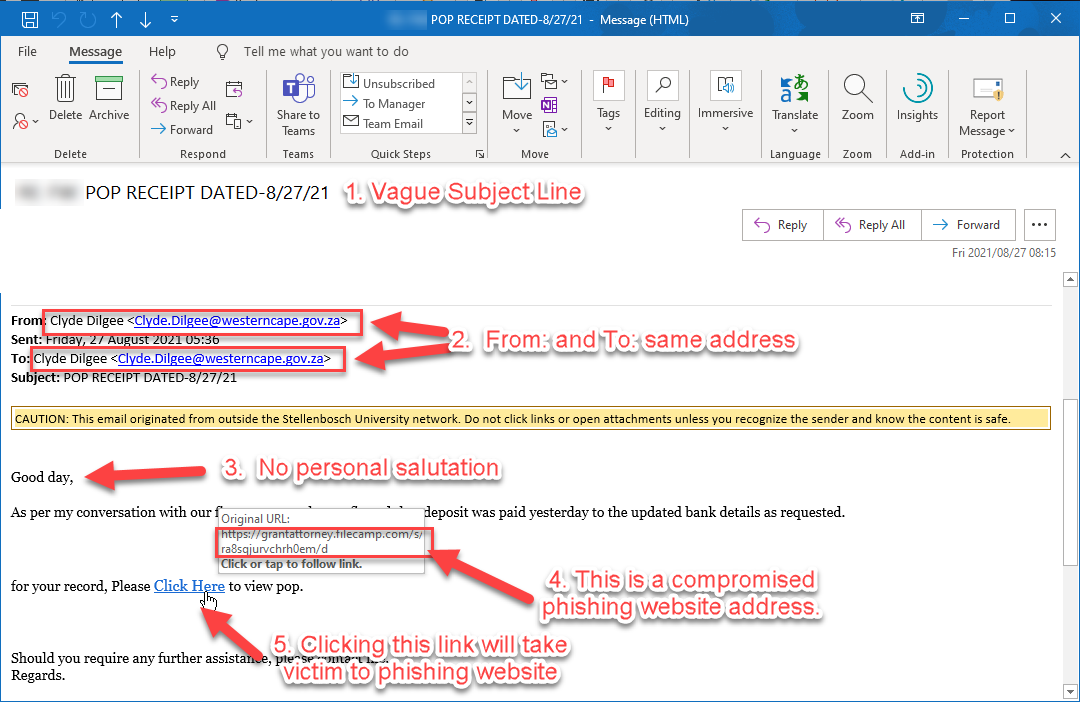
 Last month some university staff’s mailboxes were flooded with
Last month some university staff’s mailboxes were flooded with