There has been a resurgence of âsextortionâ phishing scams recently but with a slight twist.
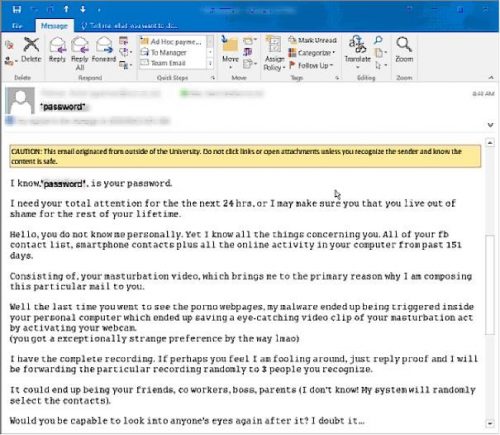
âExtortion phishingâ or âsextortionâ is an aggressive form of a phishing attack that targets potential victims in an e-mail demanding bitcoin in exchange for a promise of non-disclosure of an alleged sexual offence.
The aim of these sextortion e-mails is clear â to force their intended victims to pay up for their silence, or the footage will be shared on social networks. Ultimately this is a typically insidious scam that could easily snare an unsuspecting user.
This variant however has an added twist, in that the phishing scammers are displaying a stolen password (from other websites) that their victims use, to grab their victimâs attention.
It is usually those other websites (e,g,. hotmail, Instagram, Paycity or Facebook) that hackers use to gain access to our data, so changing those passwords are very important.
As in the example below we received earlier this week:
Several students and personnel say that they have also received similar phishing e-mails, and that password that they had used were displayed in the subject line. They were all concerned that their network account was under attack.
If you receive such a mail, there is little danger to you UNLESS you
- respond to the sender
- still use that same password for other non-university accounts and use a variation of that password.
If it is an old password that they are displaying, then the danger to you is relatively small, but if you are still using it on a different website or application please change and update immediately.
[ARTICLE BY DAVID WILES]