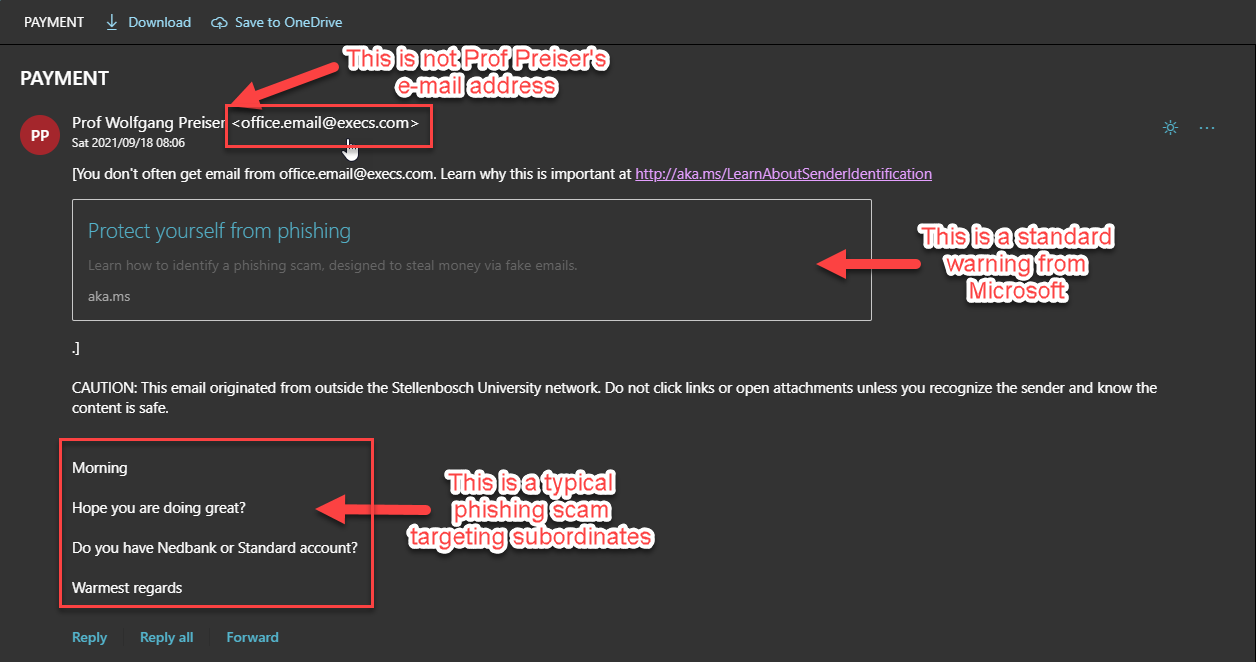
If you receive an e-mail from Prof. Wolfgang Preiser – Head of the Department of Virology asking about a “PAYMENT”, you might be tempted to quickly answer and offer your assistance.
However, this was a spear-phishing scam designed to fool its victims into thinking the mail was sent out by someone like Prof Preiser.
We are getting several reports from personnel within his department saying that they are getting e-mail from Prof. Preiser and were concerned if his e-mail account has been compromised and if this is a phishing attack.
Here is what the phishing scam looks like.
Please note that the name, has been forged and that a “throwaway” execs.com e-mail address has been used with forged details inserted. The Professor’s account has not been compromised.Â
The message below also serves as a warning and should give you an indication that this is not an email from an @sun address. Do not click links or open attachments unless you recognise the sender and know the content is safe.
CAUTION: This email originated from outside of the University.Â
Additionally there is a standard warning from Microsoft to also warn you.
This is a spear-phishing attack where an institution is attacked by impersonating prominent or public figures within the enterprise to gain access to the enterprise. The targets in this method of attack are usually subordinates of high-ranking personnel, to fool them into sending money or obtaining personal details of these personnel members.
Keep an eye open for this scam, and please report it to IT Cyber Security if you find it in your inbox by logging it on the ICT Partner Portal. Fill in your information and add the email as an attachment. Your request will automatically be logged on the system.​​
If you accidentally clicked on the link and already gave any personal details to the scammers it is vitally important that you immediately go to the USERADM page (either http://www.sun.ac.za/password or www.sun.ac.za/useradm) and change your password immediately.
Make sure the new password is completely different and a strong password that will not be easily guessed. Also change the passwords on your social media and private e-mail accounts, especially if you use the same passwords on these accounts.
Contact the IT Service Desk if you are still unsure.
[ARTICLE BY DAVID WILES]



 The Protection of Personal Information Act (4 of 2013) (POPIA) is in full effect from 1 July 2021. A brief summary of the POPIA Act is available
The Protection of Personal Information Act (4 of 2013) (POPIA) is in full effect from 1 July 2021. A brief summary of the POPIA Act is available  With a fast internet connection and unlimited, “free” internet, it’s possible to download movies and series to your heart’s content. Unless you use a pay streaming platform it’s also illegal. Additionally, if you use the university’s network and/or devices it’s also a breach of the university’s
With a fast internet connection and unlimited, “free” internet, it’s possible to download movies and series to your heart’s content. Unless you use a pay streaming platform it’s also illegal. Additionally, if you use the university’s network and/or devices it’s also a breach of the university’s