 Part of living in a connected world is understanding that our private information is more vulnerable. ID theft and data breaches are no longer isolated incidents, they happen every single day.
Part of living in a connected world is understanding that our private information is more vulnerable. ID theft and data breaches are no longer isolated incidents, they happen every single day.
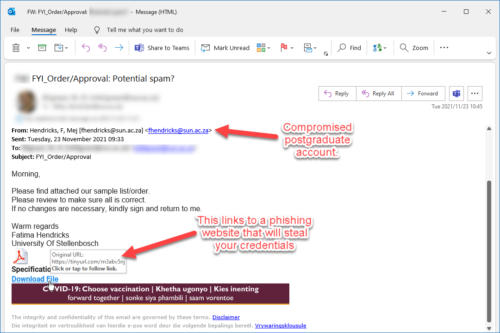
So why would a university be targeted?
Universities hold a great deal of information that could be exploited if it gets into the wrong hands. This information includes personal details and research data.
Consequences and why it matters:
Though not all data security incidents will lead to the loss or theft of information, they will expose information to unwanted risk.
A full data security breach will involve a known disclosure or inappropriate access to information, which is a more serious incident. Any data security incident could potentially be disastrous for both you and the institution.
In an effort to create awareness around some of the typical hacks that we all fall prey to, we have made an Information Security Awareness training programme available. This is a self-study programme with fun quizzes in-between. This is by no means a programme that you will need to have a pass record. This course is strictly informational so that you will have the necessary tools when it comes to Information Security.
To access the course, go to┬Āhttps://learn.sun.ac.za. When the SUNLearn main page opens, click on the “Information Security Awareness Training” link and log in with your network username and password. If you’re successfully logged in, scroll down and click on the “Enrol me” button to enrol yourself for the course and to access the training material.
If you are unable to log on to SUNLearn and you are certain that the network credentials you have entered are correct and active, please log a request via┬Āhttps://learnhelp.sun.ac.za┬Āfor SUNLearn support.

 Please take note that as a result of critical system upgrades and maintenance, the sun-e-HR system will not be available from Thursday 16:30, 15 December 2021 to Monday 08:00, 20 December 2021.
Please take note that as a result of critical system upgrades and maintenance, the sun-e-HR system will not be available from Thursday 16:30, 15 December 2021 to Monday 08:00, 20 December 2021.

 Part of living in a connected world is understanding that our private information is more vulnerable. ID theft and data breaches are no longer isolated incidents, they happen every single day.
Part of living in a connected world is understanding that our private information is more vulnerable. ID theft and data breaches are no longer isolated incidents, they happen every single day. The US government’s Cybersecurity and Infrastructure Security Agency has made a collection of tip sheets available for use. These downloadable PDF documents contain all the information you need to protect yourself from cyber security risks in a convenient, compact format.┬Ā
The US government’s Cybersecurity and Infrastructure Security Agency has made a collection of tip sheets available for use. These downloadable PDF documents contain all the information you need to protect yourself from cyber security risks in a convenient, compact format.┬Ā Before
Before