Cyber crime is a constantly evolving field. Even though the majority of viruses were created as pranks, it’s essential to stay informed of the various risks that exist on the internet if you want to stay safe online. Here’s a breakdown of the basics:
Malware, or malicious software, is a catch-all term for any type of malicious computer program. Malware is the most common type of online threat.
Ransomware is an emerging form of malware that locks the user out of their files or their device, then demands an anonymous online payment to restore access.
Adware is a form of malware that hides on your device and serves you advertisements. Some adware also monitors your behaviour online so it can target you with specific ads.
Spyware is a form of malware that hides on your device, monitors your activity, and steals sensitive information like bank details and passwords.
The world of cyber crime is very similar to that of technology. Every year, new trends, breakthroughs, and tools emerge.
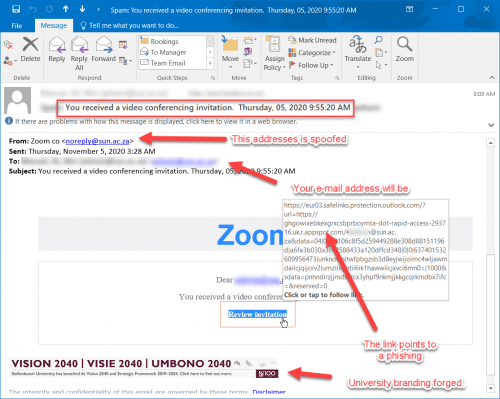
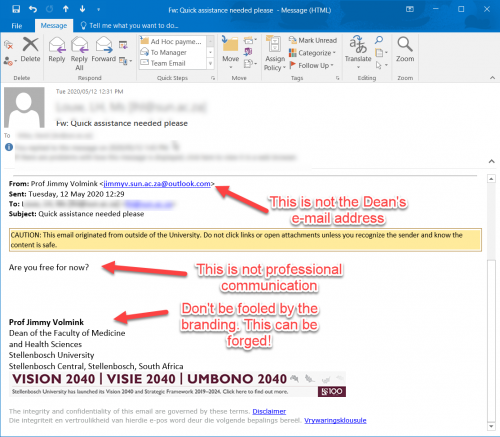
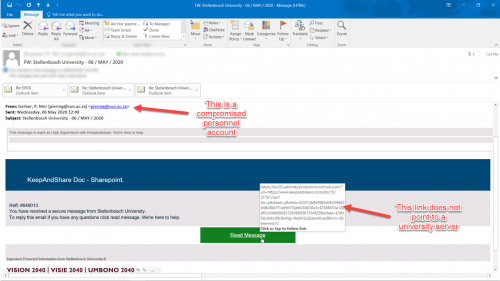
You’ve probably noticed a Malwarebytes Threat Scan icon on your desktop or laptop (Figure 1). Don’t worry, this isn’t a brand-new type of malware. Stellenbosch University’s IT department has added an extra layer of security to campus computers.
Figure 1

Malwarebytes Incident Response is the trusted standard in automated endpoint remediation. Unfortunately, with the current environment, some malware will return after removal and Malwarebytes will prompt you to initiate a restart (Figure 2).
Figure 2
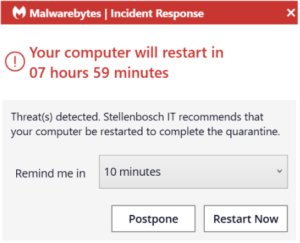
This is because the malware will sync to your browsers profile and will be synced back to your device after it has been removed. If you are experiencing such daily prompts for restarts by Malwarebytes, we suggest that you log a request on the ICT Partner Portal for a technician to assist with further remediation.
[ARTICLE BY BRADLEY VAN DER VENTER]