Spear-phishing is more subtle than conventional phishing. This scam is always attempted with far more tactical precision than ordinary phishing – in other words if phishing is like a shotgun, then spear-phishing is like a sniper rifle. Armed with illicitly gained personal information, the criminals send outwardly harmless emails that appear to be from trusted contacts. Unknown to the user, these emails typically contain malware attachments that install in the background when opened.
That malware then seizes control of your computer. The payloads can be anything from ransomware that hold your computer’s data hostage at a price to unlock to installing viruses, trojans, and worms to steal your most sensitive information. Spear-phishing can wreak all kinds of havoc and at an institution like the university, the safety of personal information should be paramount when faced with this threat. The personal and financial records of 30 000-odd students, sensitive research projects and academic records can be exposed during a successful spear-phishing attack, so spotting such insidious e-mails is a skill that more and more personnel and students must learn.
“…Spear phishing is a targeted form of email attack used to steal sensitive information through enticement, impersonation, or access-control bypassing techniques.
Unlike ordinary phishing, during a spear-phishing campaign, emails are sent to the specific targets. Apart from using the counterfeit links and compromised attachments, they can use the socially engineered content rather than payloads, asking the victim to share the information like password, finance related information, or other sensitive information which is not supposed to be shared without proper consent…”
How does spear-phishing work?
It is important to understand how the spear-phishing works, before identifying a spear-phishing email.
Spear-phishing is a targeted email attack against specific individuals, groups, or an organization. The attacker first collects the information about the intended victim in order to win the confidence of that victim. After acquiring enough information about the victim, the attacker uses a deceptive cover to send the emails to the target recipients. The outward legitimacy of the email address or the identity used in the email is what is so scary!
The spear phishing attack is often so sophisticated that the attacker is sometimes able to spoof the email address known to the recipient. The attacker gathers enough information to decide the most suitable time of the attack. Usually, the attack is launched when the recipient is expecting the email from the source that is spoofed or impersonated.
1. Check the sender's e-mail and name
Let’s face it, with information overload, we all tend to skim over details like the sender name. We are simply too busy to really check. Spear-phishing attackers can easily spoof the name of someone who you have contact with regularly. If you get an email asking you to share sensitive information that is not supposed to be shared via email or proper verification, do not just believe the sender name – check the email address as well. In the example below the name of the sender as well as some details from the public domain are used to disguise a spear-phishing e-mail. However the actual address is obviously spoofed.

2. Check the format of the e-mail
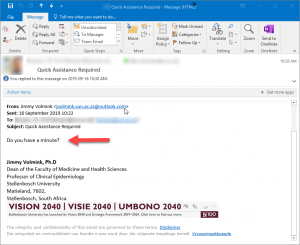
In an advanced spear-phishing e-mail attack, often both the name and e-mail address of someone you know can be spoofed. In such instances, the format of the e-mail will give you a hint of the legitimacy of the the email. If you see that the e-mail format does not match previous e-mails that you have received from that sender in the past, recheck the legitimacy of the email. Spear-phishing is anattempt to trick you to share the sensitive information. In the example below, the “sender” is trying to impersonate the Dean of the Faculty of Medicine and Health Sciences, but the words he uses do no match the normal way he deals with his colleagues:
3. Make a phone call
A spear phishing email attack can be so cleverly disguised that it does not give any hint that the sender is not legitimate. The attackers can be able to spoof the name, email address, and even the format of the email that you usually receive. If this is case, and the demand in the email can lead to a sensitive information leak, a phone call to the sender can help to confirm the legitimacy of the email and the information that is being demanded.
4. Check the links
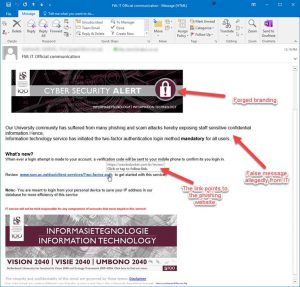
Spear-phishing attackers can trick you to click on a link shared via email. Even if you are sure about the sender’s email address and the name, make sure the link in the e-mail does not lead to a fraudulent website or malicious code. The simple trick to check the legitimacy of the link is by hovering over the link. It gives you a complete address of the link that you shall be redirected to after clicking. If you see the web address or the link path is suspicious, never click the links. One click can hijack your web browser, install malware in your system, and even get full control of your system and all the stored information. Sometimes, the address might look very familiar. In that case, make sure the page you are redirected to do not ask for the sensitive information like a username, password or similar actions. An attacker can even spoof a complete web pages of the university. In such case, make a call to confirm the authenticity of the email and the instructions mentioned in the email content. In the example below, a Information Technology “Cyber Security Alert” was forged that looked very genuine, but the link you were asked to click on pointed to a fraudulent website based in Brazil.
5. Scan the attachments
Spear-phishing attackers sometimes manage to bypass all the filters and trick users to download the email attachments and open them. These attachments may contain embedded malware, or they may require you fill in forms including sensitive information. In both cases, run online virus scan tools to make sure the attachments are free from any virus or harmful code. You should always scan any downloaded files before opening them. The types of files an attacker can emply are the obsolete versions of the documents like Microsoft Office .DOC or .XLS, PDF, or it can an executable file in the shape of .PNG,JPEG,GIF, or similar extensions.









