How many phishing e-mails have you received in the past week? Even with all the filtering and blocking mechanisms put in place by yourself or Information Technology, chances are that at least 5-10 have sneaked through in the past 7 days.
Phishing e-mails are almost as old as e-mail itself, and it seems that there is always at least one e-mail message that is trying to fool you into sending money to a total stranger, or giving up your login details and password or installing malware on your computer.
We are all aware of the classic “Nigerian 411” scam – they are so easy to identify – and while I haven’t seen such a scam in my mailbox for the past 10 months or so, 5 or 6 suddenly popped into my mailbox in rapid succession last week. This got me wondering if Information Technology had somehow changed something on the university’s mail server, and now these “primitive” phishing scams were sneaking through into my mailbox. My investigation revealed that nothing had changed, and although Information Technology’s spam filters had got considerably better at spotting and removing phishing scams from our Inboxes, the attackers continue to come up with new and innovative ways to fool their intended victims.
I read a report written by Avanan – a large “cloud security” provider for platforms like Office365, Gmail, Citrix Sharefile & DropBox. This report reveals that after analyzing about 55 million e-mails on the platforms that they protect, they discovered that 1 of every 99 of those e-mails was a phishing e-mail! Furthermore over 30% of the phishing e-mails were sent to organizations that use Microsoft’s Office365’s platform. (The university uses Office365 for its e-mail) Somehow these e-mails were evading detection and Office365’s filters and were ending up in our e-mail Inboxes, and this despite Microsoft’s claim in September 2018, that they have the “the lowest miss-rate of phish emails reported among other security vendors for Office 365.”
So what has changed, and why are we unable to block these nefarious e-mails as effectively as we have been able to do so in the past?
Something that Microsoft mentioned in its analysis of its effectiveness in catching malware and phishing, piqued my interest: They noted that the common strategy for competing email security providers was to have their customers point their MX records (network information that is used to tell the world which mail servers accept incoming mail and where emails should be routed to.) to the competing cloud service, filtering the mail and then sending on to Office 365.
Microsoft bragged that although they could not determine what competitors catch, (because it has already been filtered by their competitors) they had good insight into what their competitors missed, and based their effectiveness on that assumption.
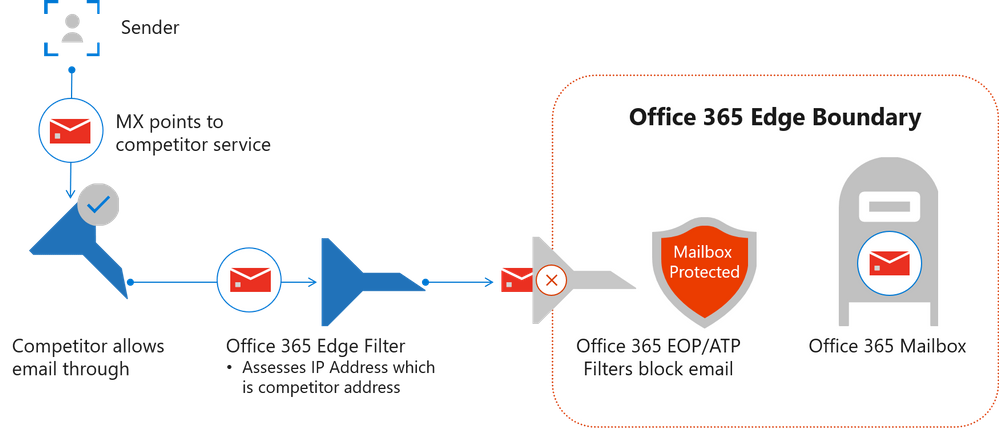
While this might be a good way of leveraging your competitive edge by building on your competitions’ short-comings, it does makes you vulnerable to becoming arrogant, thinking that you are better than your competitors, and using your market share to squeeze the competition out, and assume that you have “the lowest miss-rate of phish emails reported among other security vendors for Office 365.”.
Being so over-confident means that with Microsoft massive market share of the cloud e-mail, they overlook the risk that phishing scammers might be using Microsoft’s own e-mail infrastructure to send phishing e-mails, and test the malware and phishing filtering systems from within.
I have seen a number of phishing e-mails whose e-mail headers indicate that they use “free” Outlook.com e-mail addresses which immediately raises questions in my own mind as to how efficient their so-called malware and phishing catching ability really is, and might provide a key as to why so many obvious phishing e-mails are sneaking through to our Inboxes.
The 3 biggest threats to the university…
Phishing e-mails are messages that are disguised to look legitimate but have a criminal intent. By far, the most common type of phishing scams are those that have a payload or contain links that install malware when clicked upon.
The second most common attack method is “credential harvesting“, where potential victims are sent e-mail that directs them to a counterfeit login page in an attempt of getting them to type in a username and password.
However the 3rd category holds a far higher risk to institutions such as the university – namely extortion and “spear-phishing” emails. (I wrote an article on “sex-tortion” emails earlier in March this year, and will not go into any further detail in this article) Spear-phishing uses social engineering techniques to customize a message to the recipient. These attacks are more rare than ordinary credential harvesting e-mails, but are far more dangerous, as they often appear to come from a trusted colleague, and are often targeted at top executives at an institution.
Phishing attacks are increasing worldwide. A Kaspersky Labs report revealed that there was a 132% increase in phishing emails between 2017 and 2018, attributing the increase to a fact that we all do not want to hear – phishing is very, very effective. F5 Networks found spear-phishing attacks to be the root cause of 48% of the security breach cases in the past 2 years, and that over 90% of enterprise malware infections were caused by phishing e-mail.
Verizon Corporation. indicated that as much as 4% of people will click a link in any given phishing attack, making phishing far more lucrative for attackers than spam. They further implied that rate is estimated to increase up to 30% at organizations that have not trained and sensitized their employees how to spot and report phishing e-mails! That should be a sobering fact for the university as an institution.
Hiding in plain sight…
Phishers employ a technique called URL obfuscation that that is very effective at evading spam filters. Nearly all email these days is created HTML format, even simple text messages, (HTML is the standard markup language for creating web pages) and this enables phishing attackers to embed invisible characters that human readers cannot see, but are visible to Internet browsers.
Obfuscation can use the font and style attributes of HTML to conceal text. For example, the hyperlink could be obfuscated to look like it points to www.sun.ac.za but actually links to www.sunfake.ac.za. In another example that I saw, (used in a ABSA Bank phishing scam) the obfuscation tactic modified the BASE tag of the e-mail, that specifies the root address for all the links in a document, and pointed them to the phishing server. Since the viewer of the e-mail would never see the BASE tag, this tactic would be virtually impossible for humans to detect.
An obfuscated address is a type of phishing attack where the real URL that a user is directed to is obfuscated – or concealed – to encourage the user to click-through to the fake web site. As an example, the attacker may use a cleverly misspelled domain name (for example, www.adsa.co.za instead of www.absa.co.za), or hide the phishing URL in friendly text, such as “click here to verify your account now“.
The dangers of WordPress…
In the Avanan report, I mentioned earlier in this article, more than 30% of all the phishing e-mails they investigated, contained a link to a site built on WordPress, the popular content management system. Often the presence of “wp-includes” in web addresses or file names ending in .php in phishing e-mails would show that the fake phishing web-site was using the WordPress platform, such as the example below:
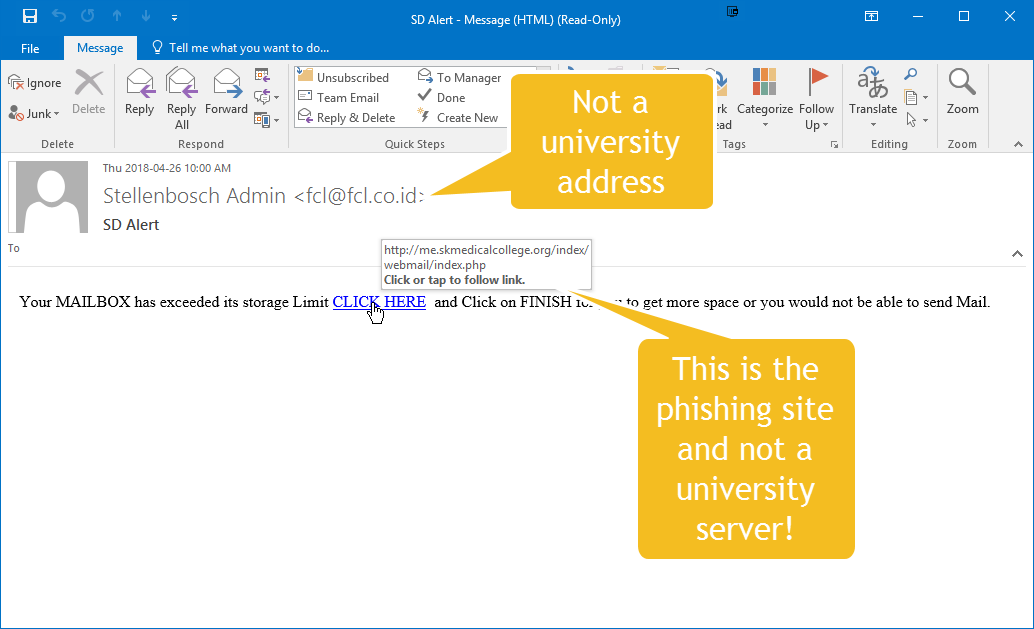
Statistics that are meant to frighten you…
Here are some more statistics that the Avanan report listed:
- E-Mail messages containing shortened links are 40.9% more likely to be phishing emails, than legitimate e-mails.
- 9% of all email sent to “undisclosed recipients” were phishing scams.
- 98% of message containing a cryptocurrency wallet address, were phishing scams.
- 4% of branded emails are phishing attempts. (We have seen the damage done by phishers to the university network were the e-mails were branded with university logos) Branded phishing attacks are typically forged in an effort to attract intended victims to click on a link to send them to a forged landing page in an effort to capture login credentials. Microsoft and Amazon were the two enterprises most often forged and made up 81% of the malicious branded messages. Financial institutions like ABSA Bank, Standard Bank and FNB and courier services like DHL and FedEx occupy 2nd place.
What can we take away from this?…
Phishing, Spear-phishing, Whaling and Pharming is very effective, and combining that sobering fact with the difficulty of detecting it through automation, means that phishing e-mails will be with us for many more years to come. Relying on Information Technology to do all the work and to protect you from these attacks is unobtainable and quite frankly, arrogant and short-sighted of us.
Phishing essentially moves the weaknesses of an institution’s IT infrastructure away from the “IT boffins in the server room” to the “PA in the professor’s office”. It is far easier to get the PA to click on a link!
Stay safe out there and don’t become a victim or a statistic!